BRATISLAVA – June 10, 2021 – ESET Research has uncovered a new APT group BackdoorDiplomacy that primarily targets Ministries of Foreign Affairs in the Middle East and Africa, and less frequently, telecommunication companies. Their attacks usually start by exploiting vulnerable internet-exposed applications on webservers in order to install a custom backdoor that ESET is calling Turian. BackdoorDiplomacy can detect removable media, most likely USB flash drives, and copy their contents to the main drive’s recycle bin. The research was exclusively previewed at the annual ESET World conference this week.
“BackdoorDiplomacy shares tactics, techniques, and procedures with other Asia-based groups. Turian likely represents a next stage evolution of Quarian, the backdoor last observed in use in 2013 against diplomatic targets in Syria and the United States,” says Jean-Ian Boutin, Head of Threat Research at ESET, who worked on this investigation along with Adam Burgher, Senior Threat Intelligence Analyst at ESET. Turian’s network encryption protocol is nearly identical to the network encryption protocol used by Whitebird, a backdoor operated by Calypso, another Asia-based group. Whitebird was deployed within diplomatic organizations in Kazakhstan and Kyrgyzstan during the same timeframe as BackdoorDiplomacy (2017-2020).
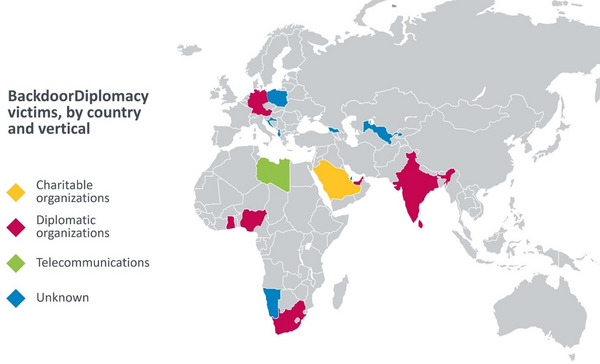
Victims of BackdoorDiplomacy have been discovered in the Ministries of Foreign Affairs of several African countries, as well as in Europe, the Middle East, and Asia. Additional targets include telecommunications companies in Africa, and at least one Middle Eastern charity. In each case, operators employed similar tactics, techniques, and procedures (TTPs), but modified the tools used, even within close geographic regions, likely to make tracking the group more difficult.
BackdoorDiplomacy is also a cross-platform group targeting both Windows and Linux systems. The group targets servers with internet-exposed ports, likely exploiting poorly enforced file-upload security or unpatched vulnerabilities – in one instance leading to a webshell, called China Chopper, used by various groups. The operators attempted to disguise their backdoor droppers and evade detection.
A subset of victims was targeted with data collection executables that were designed to look for removable media (most likely USB flash drives). The implant routinely scans for such drives and, upon detecting insertion of removable media, attempts to copy all the files on them to a password-protected archive. BackdoorDiplomacy is capable of stealing the system information of the victim, taking screenshots, and writing, moving, or deleting files.
For more technical details about BackdoorDiplomacy, read the blogpost “BackdoorDiplomacy: Upgrading from Quarian to Turian”on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
Victims by country and vertical
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. With solutions ranging from endpoint and mobile security to encryption, multi-factor authentication and endpoint detection and response, ESET’s high-performing, easy-to-use products unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an intelligent IT security company that enables the safe use of technology. This aim is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook and Twitter.