Last week, Progress Software released yet another patch for the MOVEit file transfer software to address the third in a series of recently discovered vulnerabilities.
If exploited, these vulnerabilities allow an unauthenticated attacker to gain unauthorized access to a MOVEit Transfer database. MOVEit users are urged to apply the latest patch. Until they have done so, software users should follow the mitigation steps provided by the MOVEit team and prepare to update as soon as possible.
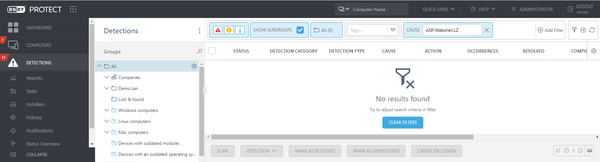
Likewise, organizations should also investigate the indicators of compromise published by CISA and Progress Software to determine whether their networks have been potentially compromised. ESET security products detect the webshell payloads seen in the attacks as ASP/Webshell.LZ. Hence ESET PROTECT customers can search for this detection name as a way of checking whether they have been attacked:
A search result of “No results found” means you have likely not been attacked. However, any hits from the search should trigger a review of the detections on the specific computers/servers where the detections occurred. ESET Inspect customers can see more detail on the actions that occurred prior to the detection of the webshells.
If you have purchased an ESET security service, such as ESET Detection and Response Advanced, make sure to request a threat hunt by one of our security specialists. If you have ESET Detection and Response Ultimate, then our security specialists have likely already performed a hunt in your environment and are actively monitoring for any threat activity related to this attack.
If the installed ESET protection detects ASP/Webshell.LZ within the environment, the customer will want to:
- Verify that they have applied patches as per Progress MOVEit’s advisory.
- Review MOVEit IIS logs for known indicators of compromise showing use of the known malicious human2.aspx. This will supply them with dates of the first attempted uses of the malicious webshell, and IP addresses used by attackers for the webshell.
- GET /human2.aspx
- human2.aspx = malicious and does not exist on a default install of MOVEit
- human.aspx = safe and exists on a default install of MOVEit
- Review MOVEit audit logs to look for exfiltrated data using MOVEit’s built-in reporting.
- Create a custom report inside of MOVEit to generate a report of all downloaded files from May and June 2023.
- Fields: *
- Tables: log
- Criteria: Action = 'file_download' AND (LogTime LIKE '2023-05%' OR LogTime LIKE '2023-06%')
- Compare this report to the dates/timestamps for the use of the webshell identified in IIS logs to find likely exfiltrated files.