If the recent 2019 ESET Global Press Event was any indication, with its 57 international journalists and nine research presentations, then cybersecurity has become Tier 1 NEWS. The event was flavored with a “healthy dose” of IoT threats, APT activities, cyberespionage, and more common threats like sextortion and mobile malware. The takeaway for many was that this diverse and complex threatscape could use a guidebook.
Well, that guidebook already exists. Thankfully, we have the MITRE ATT&CK™ knowledge base, which has iterated into a popular common taxonomy among IT security professionals, including incident responders, network defenders, threat intel analysts and malware researchers, all of whom have contributed to help enterprise management gain a better assessment of the digital threats to their businesses.
While ATT&CK’s knowledge base widens and deepens, endpoint security vendors and their clients still have some critical business to attend to: communicating and taking both proactive and reactive steps to leverage the information already assembled by malware researchers. At ESET, and at other vendors, this engagement takes place via an endpoint detection and response (EDR) tool – ESET Enterprise Inspector (EEI). To see how ESET employs the ATT&CK knowledge base in its research and EDR tool, join our November 13 webinar: Leveraging & Improving MITRE ATT&CK™ – ESET’s Approach.
ESET Enterprise Inspector
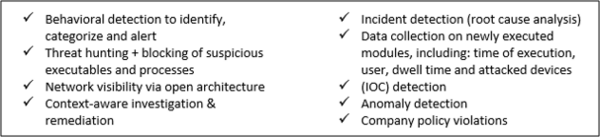
The solution comes with around 313 predefined configurable rules to detect potential threats in multiple execution configurations and enables:
Increasing these capabilities and the benefits that can be derived from them, requires efficient communication among malware researchers, threat analysts, product management teams and of course IT Security Desk staff. ESET’s efforts to address this need stretch back to the initial buildout of EEI, which began by processing internal sources of detection, documented APT/cybercriminal techniques, and over 30 years of ESET’s accumulated expertise and technology knowledge.
Many of the early rule(set) rules had their primary origin in our Host-based Intrusion and Prevention System (HIPS). These were expanded by collating and auditing external open-source data, an effort that ultimately led the EEI team to ATT&CK. The knowledge base provided valuable hints to help order, best document/classify and match tactics to detection rulesets included in ESET’s EDR tool.
As ESET Enterprise Inspector took on shape and functionality, it emerged that, in fact, much of the value lay in its role in building shared communications between ESET and clients. Similar to the way in which the ATT&CK team accentuates the creation of the common taxonomy, the EEI team has created a bridge to clients by which a dialogue can take place around complex threats and ESET mitigation options. “The shared taxonomy also enables ESET to communicate the value of managed security services, like ESET Threat Monitoring, Threat Hunting, or Deployment & Upgrade in a way which is more understandable, relatable and interactive to enterprises. This also results in a more targeted offering of these services,” Adam Luzsicza, Product Manager, Business Security.
EEI is interactive and iterative
Like the “widening and deepening” ATT&CK knowledge base, EEI is evolving as it leverages ESET's global network of over 110 million endpoints to rapidly detect and remediate emerging threats. Throughout its buildout, ESET engineers and researchers have generated new ideas, received requests and both encountered attack vectors and tactics that needed to be reflected in both ruleset creation and the platform’s functionality.
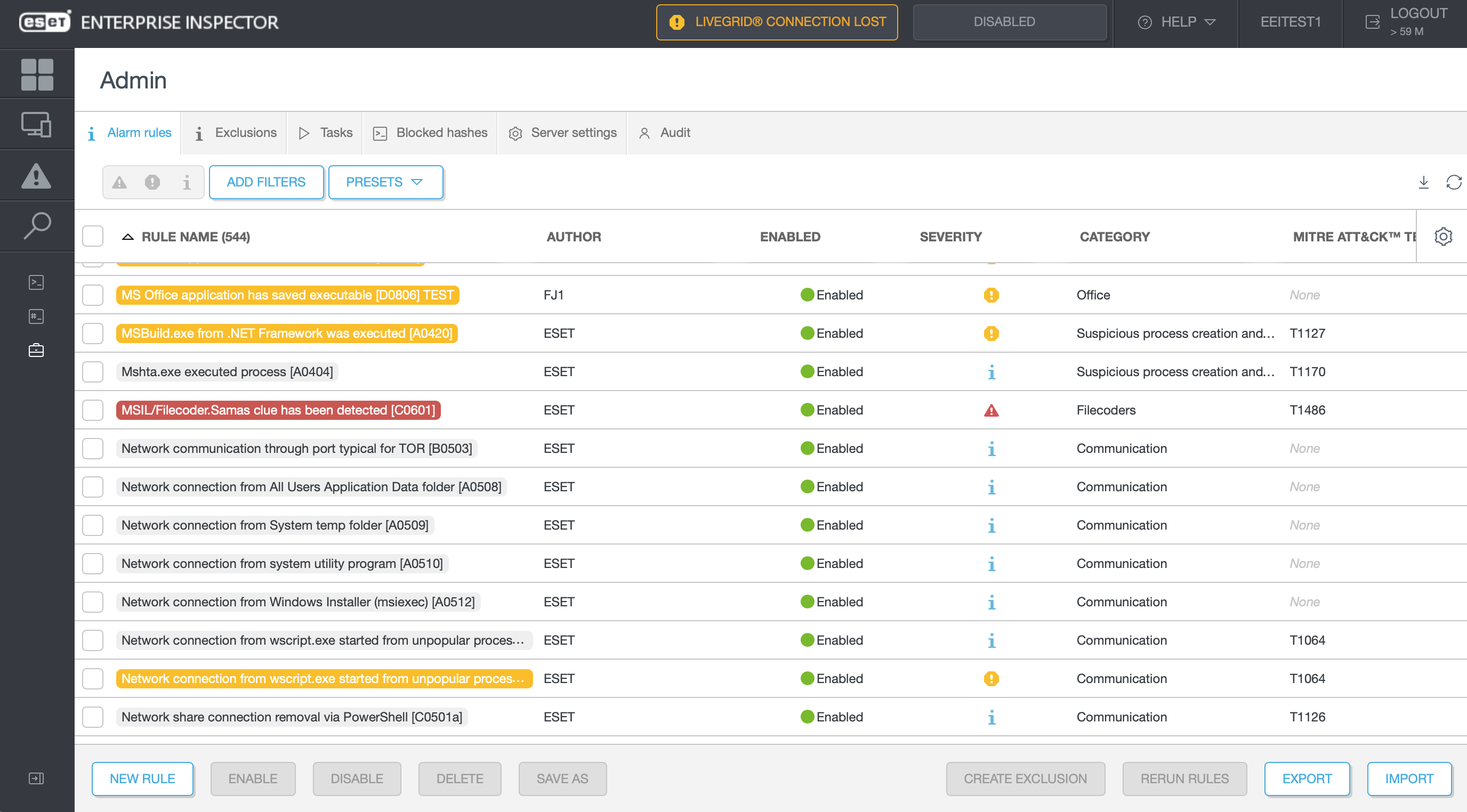
In version 1.3, released in September 2019, ESET specifically leverages ATT&CK’s taxonomy/tactics to build part of its ruleset. This is, of course, heavily bolstered by ESET’s own research and documentation of malware and APTs. The native rulesets in EEI are in fact written by ESET’s Malware Research team and delivered with 313 rules by default.
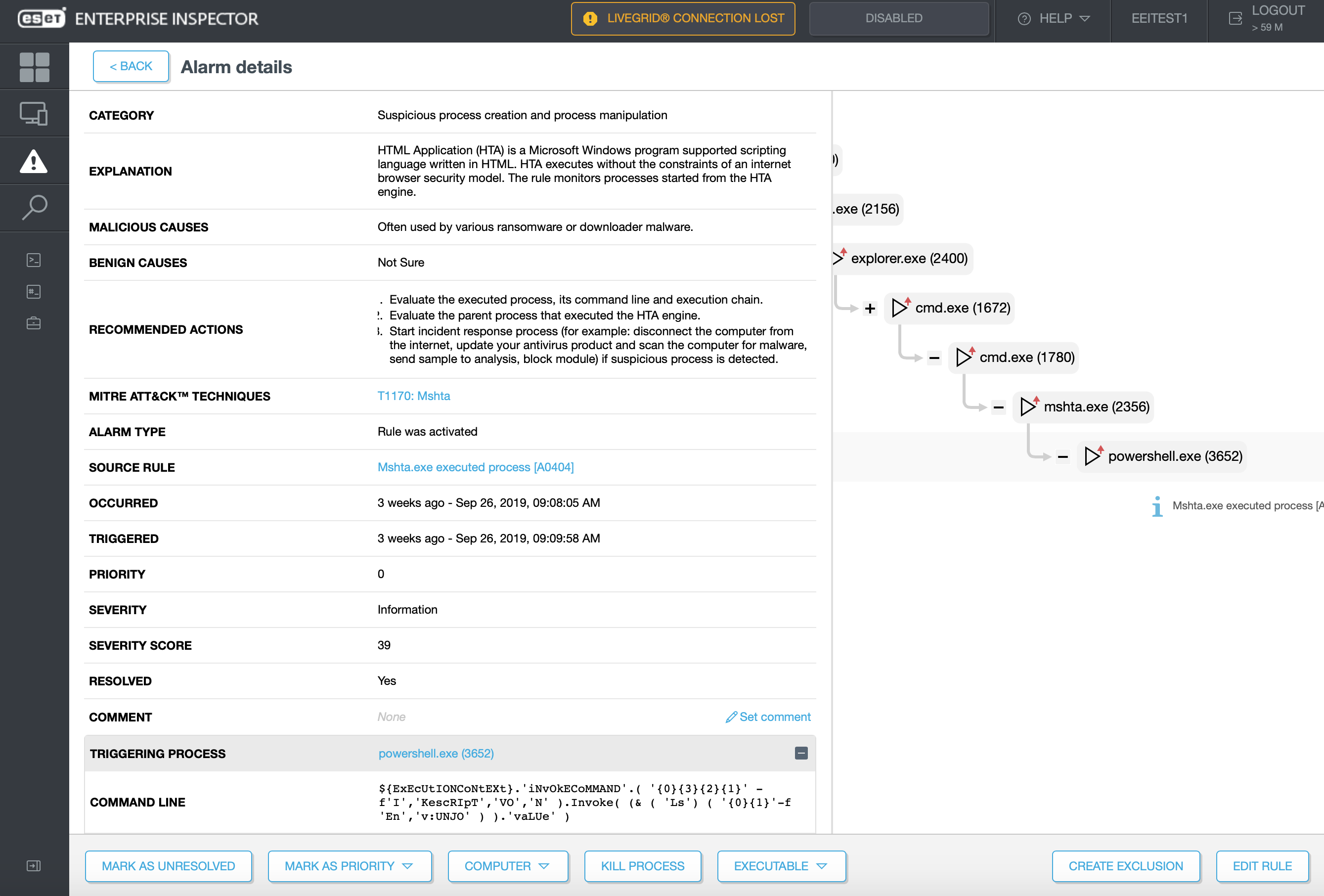
(Image 1. above - click to enlarge) Default rulesets automatically trigger alarms in EEI. Additionally, EEI users can reference the ATT&CK knowledge base directly from the dashboard.
While this is a clear improvement to the GUI, the true benefit runs deeper. That benefit stems from the engagement/interactivity taking place between the client-side user(s) of EEI and the EEI system itself, and the critical dialogue that can occur between users and ESET’s malware analysts/engineers.
Specifically, security engineers at an enterprise’s SOC need to understand better how to draw out more value from threat intelligence sources and leverage that intel to cut through the avalanche of false alerts that often plague network defenders’ EDR dashboards. That is where the rulesets, details on malicious and benign causes, and recommended actions built into EEI and coupled with references to MITRE ATT&CK techniques, come into daily play.
APTs are known to utilize very specific procedures that let them weasel their way into enterprise networks while avoiding detection. Yet many of these procedures are well-documented with actionable items that SOC teams can start scanning for right away, like known malicious IPs, domains, IOCs and other common persistence mechanisms.
Even when an initial scan picks up no indicators of compromise, that does not mean that SOC teams are finished. Security engineers need to step up their game by creating behavior-based detections/rules that thoughtfully consider all the stages of an adversary’s behavior and any artifacts that may be left behind. That is why in addition to the rules built into EEI by ESET, EEI also allows network defenders to create and edit their own rules for triggering alarms.
Based on an investigation into the alarms, the defenders can then perform a manual remediation action to exterminate any detected threats.
In this manner, security engineers can run through the entire breadth of the 266 techniques contained in the MITRE ATT&CK Enterprise Matrix and create custom-tailored detections for their enterprise network. Adversaries are always changing, which means we always need new detections. Moreover, not all detections/rules have the same value. A detection is only as good as its ability to isolate behaviors and approaches taken by real-life adversaries. This is where the dialogue with ESET’s malware researchers, analysts and engineers brings renewed improvement to the level of security maturity of an enterprise.
To learn more about how ESET employs ATT&CK for improved endpoint protection, join our November 13 webinar.
Learn more about ESET Enterprise Inspector’s Strong Performer status in the the Forrester Wave™: Endpoint Detection And Response, Q3 2018, report.