
You are what you eat. Well, your experience with cloud services reflect the same reality, they are what you make them. This necessitates some dedication to risk assessment, demonstrating the same level needed for assets found on your own network.
How safe is it?
How would you react to someone who told you “The Cloud” is impervious to interference, or that it automatically protects your data? Well my eyebrow raises, as high and pointedly as if I were Dwayne “The Rock” Johnson and I smelled something, well let’s call it fishy. Regardless of my own professional nose for identifying nonsense, there remains a lot of bad advice out there, and when it comes to the ‘the cloud’… there is a low ceiling.
The reality is that Could Computing cannot be perceived as some sort of magic security fortress that you can conjure whenever you wish to make your data more secure. Cloud services can only be what you make of them, which means that you should approach them with at least the same level of thoroughness on the risk evaluation side as you would with any data located on your intranet.
You’ll have to adopt a very tenacious approach when questioning your vendors about what exactly they do to secure their services. Take a very good look at their security policies and processes. Be specific about what the vendor’s responsibilities are and what exactly you plan to do on your end to protect your company.
Security policy - queries for the Cloud

This goes for both the Cloud vendor and your users, though consequences for the former will likely be the product of negotiation or existing Service Level Agreements. It should be clear to all concerned what will happen if someone fails to live up to their responsibilities in safeguarding your data.
Security procedures
When you are through with defining Cloud services’ objectives, you can start approaching vendors about their policies and processes. A lot of inspiration can be drawn from a document elaborating on Cloud Computing policy which also contains an extensive list of questions that you can find at the Gulf Cooperation Council eGovernment site. Here is a list of potential topics for your consideration.
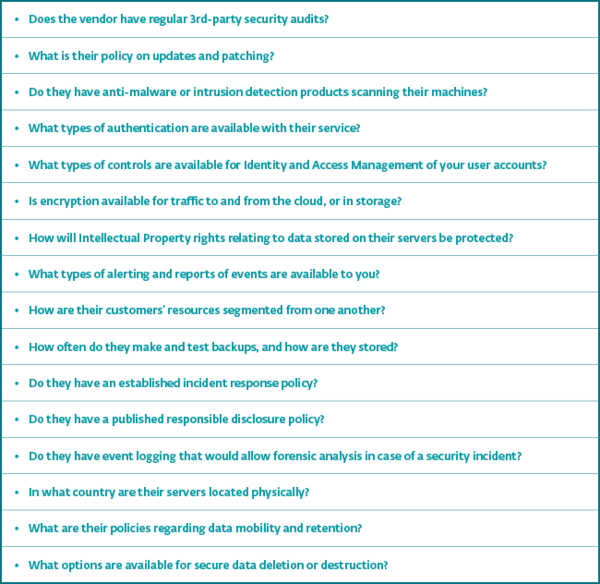
If you do your homework before jumping headfirst into the implementation phase, you can easily avoid a lack of clarity in the process and other issues. The capacity to access files and use services from any place connected to the internet is a significant one and it can either lead to an introduction of new threats to your environment, or it can be turned into an opportunity to acquire services of a credible partner leading to an improvement of your overall performance.