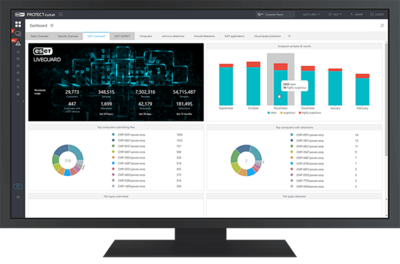
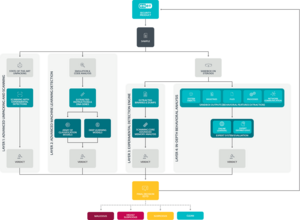
Advanced threat defense
A cloud-based technology that uses advanced scanning, cutting-edge machine learning, cloud sandboxing and in-depth behavioral analysis to prevent targeted attacks as well as new or unknown threats, especially ransomware.
ESET LiveGuard Advanced previously ESET Dynamic Threat Defense
Proactive defense against zero-day and never-before-seen threat types