If you are responsible for delivering cybersecurity services as a Managed Service Provider, or running them at a larger organization, then you know that even small mistakes can come at a high cost. Ironically, a common reaction when facing this kind of pressure is to throw money at several security products to build up a massive wall of protection.
While intended to be impenetrable, this response can have serious implications on system performance, value proposition and return on investment. In this respect, good cybersecurity poses a conundrum: too little action and security is forfeit; too much, and you are an overzealous spendthrift. So, while achieving sustainable security requires an active and hands-on approach, we argue it also requires a light touch.
To balance risks and cover multiple threats, users have long turned to running an array of standalone products in parallel in an effort to combine diverse security features. However, as we will see, sometimes less is more and developments in the cybersecurity industry means this proves unnecessary.
Since cybersecurity products hit shelves 30 years ago, leading vendors have followed the trend to build increasingly effective cyber defenses, and have also endeavored to layer key technologies and features to deliver comprehensive security products.
Regardless of these advances, the Do It Yourself (D.I.Y.) model persists, attempts at bringing together disparate products in hopes of achieving an "integrated" security suite continue despite the fact that the individual products often “Do Not Play Well Together”. These practices also fly in the face of industry efforts to build endpoint products that layer technology in a complimentary way to ensure security, but also to deliver demonstrated value with multiple features, low system impact and cross platform support.
ESET’s view is that best results against the most damaging threats are achieved by implementing an endpoint solution built on multi-layered technology in a disciplined fashion: maintaining regular system patching and updates, pursuing the intelligent use of automation and ongoing training for current or new versions of a chosen solution.
However, if the level of recurring activity on forums such as Reddit is any guide, then a comparison between the protection offered by a single multi-layered endpoint product and that of a multi-layered endpoint product combined with several ancillary products means that the question is far from having been put to bed. Unfortunately, decision makers, whether being managers of MSPs, CISOs, or unlucky board members of an SMB tasked with cybersecurity, will eventually face the same quandary.
Decision time
Before making a decision about your security priorities, strategy and solution, be sure to gather adequate and reliable information from third-party analysts. You’ll likely be navigating a web search with terms like: ‘full feature-set’ or ‘effective malware/ransomware detection technologies’. There you’ll find charts and diagrams (see below) describing features and the detection technologies behind them which are most often deployed on endpoints.
When drilling down through the layers of protection described, the reader will likely see that a majority of threats will be handled by Anti-Spam and URL blocking features; logical because the origin of most threats arrives via e-mail or malicious URLs. With ESET Endpoint protection those layers are backed by, ESET LIVEGRID, Augur our machine learning engine and by HIPS, ESET’s technology for the behavioral monitoring of system activity. This in turn can activate self-defense mechanisms that prevent the program or process from executing harmful activity.
Behind the clean descriptions of the independent features however, are a set of technologies at work that do not always have clear boundaries. Split into Continuous, Pre-Execution and Post Execution layers, it is actually these technologies which monitor, protect and in some cases actually defend your IT infrastructure.
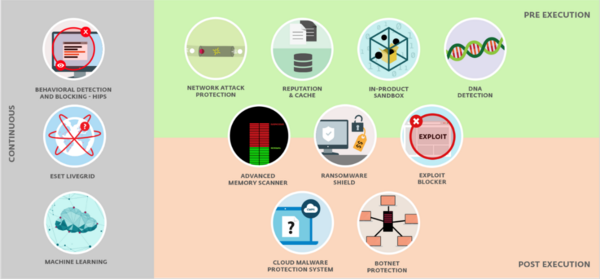
It should also be understood that the majority of vendors’ endpoint products attempt to address prevailing threats in methodologically comparable ways, albeit with different technologies, thus we can see that when the final layer(s) of the solution come into play, the vast majority of threats have already been eliminated.
In terms of percentages, this translates to numbers that miss 100% by only a few hundredths of a percent. At the scale of an MSP or large enterprise, these fractions of a percent can amount to, in absolute terms, a lot of bad objects surviving (in the ecosystem). However, as already mentioned, attempting to counter remaining risks with additional products has a clear drawback in that the technologies behind endpoint protection features are highly integrated and thus are unlikely to play nice with add-ons.
Seen this way, leveraging hi-tech add-on solutions to increase protection via the use of a parallel layer begins to look suspect, since those defensive layers are likely already in place and work in an integrated fashion.
A good example which comes to mind is Next-gen products, which claim to “dramatically boost security” via advances in Artificial Intelligence. The fact is, the majority of comprehensive Endpoint suites already apply machine learning and other advanced technologies to their multilayered solutions and have been for years if not decades. Now, ask yourself about detecting those remaining fractions of a percent: how much are they worth to you?
Inversely proportional added value?
As an MSP or other “power user”, operational benefitsand achievable return on investmentwill come from using fewer ancillary solutions, especially when a single solution is sufficient. It really comes down to having more trust in fewer or, ideally a single solution.
You must also consider that using multiple security products can have a technical impact on network performance, most importantly on the primary endpoint security solution you have implemented, not to mention the team managing it. More specifically, we can imagine administrator fatigue caused by using multiple and disparate user interfaces, which may increase the likelihood of broken processes and the number of false positives.
Simply put, trying to properly manage multiple security technologies requires more capacity, is technically complex, raises costs and is unlikely to add value in proportion to the slight (potential) increases in security. It may even make the system less secure due to in-fighting for access to low-level processes between competing security products. Instead, have your security teams master your chosen endpoint’s infrastructure and processes, and foster a collaborative relationship with your supplier.
Are MSPs educating clients’ end users and their management effectively?
Since most malware incidents on any network originate from the clients being serviced, educating its users on the role “human” factors play in security lapses is critical. This will also help management understand that throwing multiple security products together is not a complete solution. Instead, user education means both supporting and monitoring the implementation of best security practices, including good password hygiene and regular updates to your PCs’ OS and software, and familiarizing users with identification of phishing and social engineering attacks.
The value is added time, additional capacity and… increased security
While it sounds simple, the priorities highlighted above, coupled with a well-managed multi-layered security product are core components of both security and value for money. Improved client and end user knowledge will allow more effective control over their systems, lower risks and save on costs for all parties, except for the attackers.
Looked at in terms of ROI, if an MSP is able to save time and capacity by avoiding the use of multiple products, there will be more time to focus on managing the platform, properly performing updates, and completing necessary upgrades, integration and automation. This tight binary, i.e. -having disciplined core security practices and employing sound business rationale - is what is most likely to help your business grow and sustain your security practice in the MSP business space.
