There are a multitude of cybersecurity issues that enterprises must negotiate in the current digital landscape, including ransomware. Ransomware is a form of malicious code that blocks or encrypts the contents of a device and demands a ransom to restore access to the data. The devices in question include mobile phones and PCs but also extend to servers and Internet of Things (IoT) devices.
When a ransomware infection is successful, companies may lose access to their intellectual property, suffer halts in production, or lose clients — suffering additional reputational damage. Like other cyberattacks, ransomware infections can result in huge financial losses — the British pharmaceutical company Reckitt Benckiser estimated that the NotPetya ransomware cost it a whopping $140M.
In discussion with ESET, organizations identified ransomware as their biggest security problem, although this is not necessarily due to the prevalence of this type of malware. “Companies named ransomware their number one concern due to highly publicized attacks, such as WannaCry and NotPetya, that caused multibillion dollar damages, with brands appearing in articles in the world’s top media. Thus, even a person who had never experienced any ransomware infection perceived it as a grave threat,” explained Jakub Debski, Principal Product Manager at ESET.
More recently, new strains of ransomware like Sodinokibi and Ryuk have been wreaking havoc on businesses. One interesting aspect of Ryuk has come via its delivery as a payload of the powerful Emotet trojan, itself distributed via malicious emails. These threats have hit the mark at several large organizations for a high-ransom return. Thus, the prevailing trend of “big game hunting,” signals that (a) ransomware remains a fearful weapon and (b) that other compromises of network security may be afoot within an organization.
Still, other paths to ransomware infection exist. Cases in point are WannaCry, which remains a highly educative case for users concerned about the consequences of unpatched vulnerabilities, and NotPetya, which infamously demonstrated the consequences of runaway supply chain attack. We can also point to fresh threats like BlueKeep, which has been leveraged for coin-mining campaigns and could be leveraged to introduce ransomware via weaknesses in widely used Remote Desktop Protocol (RDP) products.
Email remains the most common channel for ransomware infection
In response to customer needs and concerns, ESET integrated Ransomware Shield (a tool that evaluates the behavior of malicious code in order to detect if it really is ransomware) into its business security solutions. ESET already provides its customers with cutting-edge behavior-based malware detection in the Host-based Intrusion Prevention System (HIPS), allowing users to set custom rules for protection against ransomware. However, should something slip past the 11 other security layers, Ransomware Shield will be automatically activated.
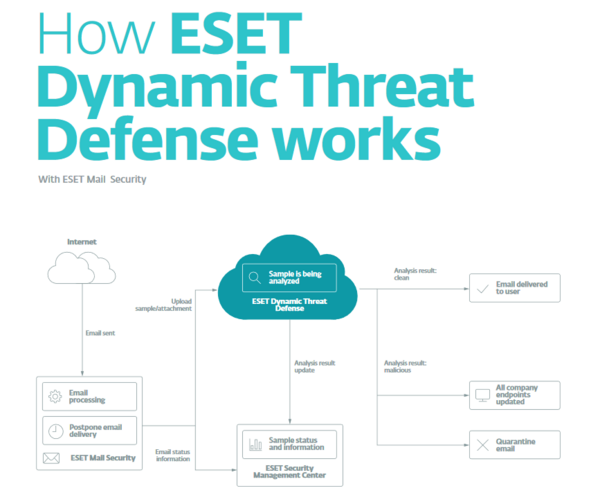
As email remains the most common ransomware distribution method, whereby an initial downloader file is delivered followed by the ransomware as a secondary infection, enter ESET Dynamic Threat Defense (EDTD). EDTD provides additional protection through its inclusion in Mail Security, File Security, and Endpoint Protection products, and utilizes a cloud-based sandboxing technology and multiple machine-learning models to detect never before seen threats.
For instance, ESET’s machine-learning technology recently discovered a suspicious sample on computers at Hong Kong universities that ESET researchers identified as an updated launcher being leveraged by the Winnti threat group. Submitting suspicious samples for machine-learning analysis in the cloud via EDTD is especially critical for harnessing the full might of cloud processing and taking advantage of more models to detect malware. Attachments classified as malicious by EDTD are then stripped off the email, informing the recipient and the wider network of the detection.
The need to raise security awareness among employees
The debate around whether the cause of a successful ransomware attack is the attackers’ skill or the negligent security habits of employees does not have a clear winner. Regardless, the risk of a ransomware infection is one of many reasons why companies should concentrate on training their employees in best cybersecurity practice.
In the case of WannaCry, the infection was spread by exploiting a vulnerability in Microsoft Windows. To prevent the attack, companies simply needed to install the available security patches, and companies that failed to do so suffered the consequences. “It is no small feat that both companies and consumers protected by ESET’s multilayered technologies were not impacted by WannaCry, as ESET had taken appropriate steps to add network detection of the exploit two weeks before the largest ransomware attack in history struck,” noted Debski.
Improperly allocated investment
Companies should examine whether correct measures that contribute to overall security have been implemented. “We see a trend of some companies spending hundreds of thousands to millions of USD on advanced solutions, but not a few thousand more on well-trained personnel to take responsibility for deploying and managing security measures on a network. Instead, companies often choose to accept the risk of certain weaknesses because they do not expect a ransomware attack to happen to them,” commented Debski.
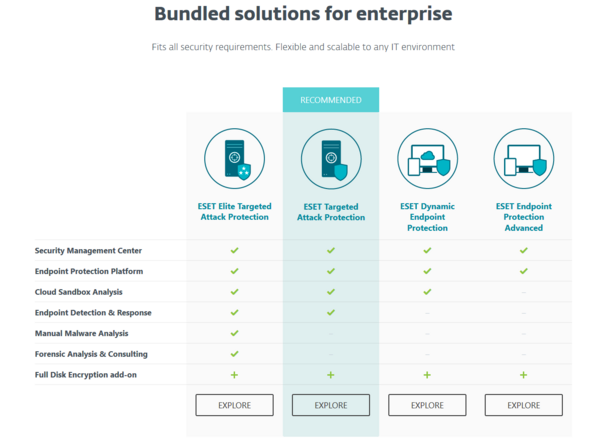
The deployment of a multilayered security suite like ESET Endpoint Protection should be paramount to all enterprises, followed by sustained maintenance and best security practices to ensure a holistic approach to security is a number one priority.
For further information on how to protect your company against ransomware and similar attacks, please see these useful resources:
- RANSOMWARE: an enterprise perspective
- Best practices to protect against Filecoder (ransomware) malware
- ESET vs. crypto-ransomware
- What is ransomware?