COVID-19 scams and social engineering target businesses and capitalize on rapid change
COVID-19, like Brexit before it, is demonstrating once again how rapidly scammers can tap into current news and switch gears to leverage any significant change to their benefit. The risks this brings are further amplified by large numbers of the global workforce switching to working from home.
The home office difference of COVID-19
Brexit, hurricanes, GDPR, embargoes and trade wars all come to mind when thinking about disruptions to business continuity. But those crises don't see tens of millions of workers, globally, opt for, or sent on, home office in a time scale measured in hours as with COVID-19.
Reuters reported on March 19 that the “Microsoft Teams chat and conferencing app gained more than 12 million daily users in one week, a 37.5% jump as more people worked from home during the coronavirus outbreak.” Reuters further reported that the total number of Teams "users grew from 32 million to 44 million in the period between March 11 and March 18 alone.”
The radically changed scale of telework/home office and the heightened scam threatscape have the potential to multiply the challenges facing enterprises and businesses of all sizes. Securing access via VPN and leveraging both multi-factor authentication and encryption are all good moves in helping secure your employees and your critical business data.
However, that still leaves the door open to considerable risks for corporate devices outside corporate networks and to malware targeted at corporate networks via online channels. To counter them, we recommend enabling a dynamic defense module – ESET Dynamic Threat Defense (EDTD) – that offers the full potential of ESET’s cutting-edge technologies and its multiple layers, including cloud sandbox and machine-learning protection, all manageable from an IT admin’s dashboard. But let’s get back to the risks.
Scams and social engineering can enable corporate espionage and targeted attacks
The line between scams and social engineering can blur, when the stakes are high. Business scams are as old as time, the purchase of substandard or fake goods, for example, but their digital counterparts sometimes bring even greater impacts. Online scammers are known to zero in on misfortune, exploiting users’ goodwill, with consumers commonly targeted. However, with businesses sharing more information in Corporate Social Responsibility reports and with millions of employees now working from home, businesses are at even greater risk.
In the case of COVID-19 – even prior to its pandemic status – we see again the same appeals for “aid”, and business opportunities where scams are thriving aplenty. Just like in past tenders, proposals and contracts up for grabs, scams are flourishing. Business reps, sales engineers and back office staff are now more likely to open (random) emails titled, “RE: Request for proposal (RFP)”, or to click on unsolicited PDFs – a prime source of ransomware infection as well as model material for EDTD’s capabilities to swing into action.
Staff could also give away “need to know” information, like the direct email and phone number of key staff like the CFO. Scams and spearphishing targeting the C-suite, also known as Business Email Compromise (BEC), led to losses totaling at least US$1.7 billion in 2019. So many “harmless acts” by employees risk ransomware infection, financial loss or, potentially worse - persistent threats introduced to your network.
Phishing, out come the sharks!
Phishing, a top threat to business, often intensifies as business competition heats up. When communications concentrate interest (buzz) around high-value business topics or projects, increasingly valuable info can begin to leak. What began as a legit business opportunity can grow to attract the interest of competitors and criminals alike. By this time even lower to moderately skilled cyber criminals may have collected enough material to direct a spearphishing or espionage campaign at your organization. And the aforementioned C-suite? Whether via oversharing, spearphishing or both – as of March 12, they and other key staff may have been more exposed.
Emails and documents: Shields up!
Prior to COVID-19, the threatscape was already pushing many businesses and organizations to increase security. Now, the rapid deployment of concrete steps to boost security is in order. Beefing up protection for email communications and deeper analysis of documents and other email-attached files is a great place to start.
For starters, email remains the most common distribution method for threats, including ransomware, and is also leveraged in targeted attacks. Thus, securing email is critical. In many cases an initial downloader is delivered via a malicious email or document, which leads to a secondary action: ransomware infection or worse, persistence on the network.
Enter ESET Dynamic Threat Defense. EDTD also provides additional protection through its inclusion in ESET Mail Security, ESET File Security and our Endpoint Protection products, and utilizes a cloud-based sandboxing technology and multiple machine-learning models to detect and block never-before-seen threats.
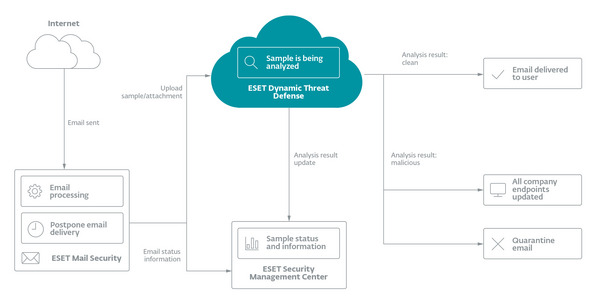
<Image 1. A new sample on its journey through EDTD’s cloud-based analysis>
For businesses newly faced with mass numbers of teleworkers, EDTD provides the ability to analyze samples within minutes, no matter where users are working. If anything malicious is detected for a single employee, protection extends to the whole company instantaneously.
EDTD leverages the same machine-learning technology that recently alerted ESET researchers to a suspicious sample on computers at Hong Kong universities. The sample was ultimately identified as an updated malware launcher being leveraged by the Winnti threat group.
Submitting suspicious samples for machine-learning analysis in the cloud via EDTD is especially critical for harnessing the full power of cloud processing and taking advantage of more models to detect malware. Email attachments classified as malicious by EDTD are stripped from emails, informing the recipient and the wider network of the malicious detection. EDTD is also able to run these same scans on files found on employee USBs.
EDTD works in concert with other technologies installed on endpoints such as ESET Ransomware Shield, which provides behavior-based detection of ransomware, and the Host-based Intrusion Prevention System (HIPS), which allows users to set custom rules to block processes that display ransomware-like behavior.
Upgrading at a time like this?
Many companies might have concerns about adding new technologies to the setup of their existing security suite. However, EDTD adds protection without any impacts to management or performance of managed networks. The machine learning processes that support the cloud sandboxing analysis in EDTD take place in the ESET cloud without requiring any use of on-premise customer resources. Thus, EDTD is a tool uniquely suited to immediately address the fact that overnight, hundreds of millions of users intensified their online activities.
With many users now mixing business and personal computing mindsets, and while not connected to better-protected and “monitored” corporate networks, many users may not use or maintain the practices, tools and security-mindedness needed to safely continue their work online. These risks fuel both social engineering and scams and give threats greater opportunity to strike millions of work computers.
Shifting supply chains
When markets shift, or IT security incidents and global health crises happen, businesses may scramble to substitute suppliers, change reporting and communication processes, and even change whole logistic systems at times. Unfortunately, a business seeking to rapidly address a perceived deficiency may enter into business with companies that haven’t done due diligence in risk assessment, don’t meet basic IT security norms or are scammers themselves. In these cases, a properly managed security suite becomes even more essential. Imagine the major shifts in logistics around COVID-19.
Elements of these scenarios have been seen before, courtesy of the Telebots APT group, which wreaked havoc on global supply chains via NotPetya malware, making it the most devastating cyberattack in history and costing some of its biggest victims upwards of $10 billion. In addition to direct impacts from ransomware experienced by some businesses, others unaffected by the malware cut contacts with their counterparts up and down the supply chain in domino effect in a bid to stay safe. Sound familiar?
Closing thoughts
The rapid change and increased risk in the examples provided here show that organizations should see COVID-19 and the wider threat landscape as an opportunity to make conservative, yet immediate improvements in protection. These can be provided by ESET Dynamic Threat Defense, which improves protection by helping to guard communications and IT’s perpetual weak spot, the human factor.
*This blog references ESET research on active threat groups which are documented on both the MITRE ATT&CK® website and at WeLiveSecurity.com.
They include:
1. Telebots APT group
2. Winnti threat group
