ESET to tease ESET Enterprise Inspector for macOS at RSA
For cybersecurity folk, turning the calendar over to 2020 helps mark the fact that a “new normal” has arisen, one where complex techniques and tactics are wielded by malicious actors to disrupt, damage, or destroy infrastructure, business operations and service continuity – and worse, public trust.
For businesses keen to combat this, tip-of-the spear solutions include Endpoint Detection and Response (EDR) tools, which have been developed by vendors to deliver increased insight into their client's networks. Many of these solutions will be on display at RSA 2020, including the as yet unreleased ESET Enterprise Inspector 1.4 (EEI). In a crowded field of EDR solutions, see the who and what behind our tool at booth #753 South Hall.
What’s required to manage EDR platforms?
Time, money – the usual suspects. What is less obvious may be the maturity and resources of the security team needed to manage EDR platforms to best effect. Luckily, in parallel to the development of these tools, an increasingly open collaboration environment has emerged around documenting threats. EDR tools like EEI not only give insight into the customer’s own network but exist to help integrate data from other sources. EEI brings in MITRE ATT&CKTM but also data routed directly from ESET’s own threat analysts and researchers.
As enterprises increasingly host complex, multiplatform environments, wider recognition of threats vectoring from diverse operating systems has emerged as a concern; macOS can be counted among these. And, while Windows and Linux dominate at the enterprise level, research and telemetry show that threats targeting diverse networks are successfully being sent via “poisoned” Apples.
Gartner, in its December 2019 Market Guide for Endpoint Detection and Response Solutions, states: “The techniques used by attackers and methods used to evade detection have also expanded, requiring detection engines and controls to identify them and produce alerts that also inform defenders how they should respond to the event and what remediation is possible. Increasingly, these controls and remediations are aligned to the MITRE ATT&CK framework, and many vendors now catalog their detection routines against ATT&CK controls, using MITRE terminology in alert and reporting." *To us, the EEI interface aligns with this view and aims to provide alarms, data and empowerment.
Problems of scale
Businesses make money via increases in scale and the creation of efficiencies; malware campaigns are no different. As such, attacking a few Macs on a Windows-centric network may not seem like good business acumen, but ESET has documented this very same tactic during an investigation of an updated macOS malware component employed by OceanLotus (APT32) and documented in the ATT&CK knowledge base.
Thus, ESET’s “Lone Mac” scenario (video above) makes a strong case for EDR systems to provide extensive data on malicious command and control traffic targeting those machines. Whether employed in graphic design, videography or C-level management tasks, Macs should be attended to with the same high level of security. ESET has addressed this need in its (unreleased) ESET Enterprise Inspector version 1.4.
With more than 350 (approx. 40 are specific to macOS at present) predefined configurable rules to detect potential threats in multiple execution configurations, EEI enables:
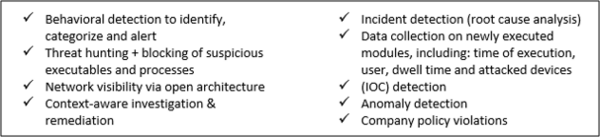
Via this EDR tool your security engineers can better leverage the 191 techniques (as of 10/09/19) contained in the MITRE ATT&CK Enterprise Matrix for macOS, the current set of 40 macOS rules created by ESET in EEI 1.4, and create custom-tailored detections for your own networks, including specific data related to macOS tactics and techniques.
EDR @ESET: Keys to a Community
EEI helps mature IT Security and Security Operations Center (SOC) staff leverage the system’s clear user interface for improved understanding of their network and the threatscape. It also keeps them in a persistent dialogue with their peers, including malware researchers and threat analysts at ESET and from across the industry. All of these “human components” of the protection system are thus informed by rules collated and/or built from both open-source and in-house ESET data, data audited by both researchers and analysts, and backed by over 30 years of ESET research into malware behavior.
Specifically, engineers at an enterprise’s SOC need to better understand how to draw more value from threat intelligence sources and leverage that intel to cut through the alert fatigue that can plague network defenders accessing EDR dashboards. And, for journeymen IT security staff with access, the platform is a great tool to accelerate their learning.
Bringing together a multiplatform EDR tool complete with a rule exclusion system, indicator of compromise (IoC) search and the ability to write custom XML-like rules, ESET Enterprise Inspector contributes to improved return on investment. Rules, both native and custom, details on malicious and benign causes, and recommended actions built into EEI couple with the ability to cross reference ATT&CK techniques, and all come into play at this level of proactive defense.
Those capabilities are vital in countering APTs, which utilize specific procedures to weasel into enterprise networks while avoiding detection. With EEI, SOC teams can immediately check for known malicious IPs and domains, IoCs and persistence mechanisms.
With macOS brought into the fold, another highly relevant vector can also be monitored and provide valuable data. One need only look at recent headlines to see that Macs and Mac users are being targeted by rogue developers and APTs like Lazarus group. To address this reality, EEI for macOS also allows network defenders to create and edit their own rules to trigger alarms. Based on an investigation into those, defenders can then execute remediation actions to neutralize detected threats.
Detection is only as good as its ability to isolate behaviors and approaches taken by real-life adversaries; increasing the diversity of data can only increase security. This is where the dialogue with ESET’s malware researchers, analysts and engineers can raise the level of security maturity in an enterprise.
*Gartner, “Market Guide for Endpoint Detection and Response Solutions,” Paul Webber, Prateek Bhajanka, Mark Harris, Brad LaPorte, 23 December 2019.
