
In ongoing consultations with clients, large companies named targeted attacks and hacking as two of their biggest security challenges since they can seriously impact the continuity of business activities in an organization.
Attackers have many means to infiltrate companies. However, many attacks, don’t require a very high level of technological sophistication. Instead, techniques like targeted social engineering, i.e. spear phishing, or the use of known vulnerabilities for which, patches may have been issued but businesses have not yet deployed, can lead to damaged reputation, revenue and data breaches.
On the other hand, high levels of sophistication can also be utilized as is in the case of a Zero Day attack. Chief among these was Stuxnet, a recorded attack where malicious code successfully deployed four zero-day vulnerabilities to impede a uranium enrichment program in Iran, and which, according to media, was a state-sponsored attack.
There are many reasons why organizations become repeat targets. Their bank accounts contain more resources than those of an average person or small business and they also have considerable amounts of interesting data that can be monetized. Attacks targeting companies can also be used as a form of competition. Most often, this concerns data hunting, i.e. obtaining interesting information or intellectual property. These attacks can be accompanied by blackmail. For example, a client database is stolen from a company and is later approached by the perpetrators and asked, “what they are going to do about their loss”.
Different ways to monetize attacks bring different consequences
Organizations often find it difficult to admit they have been breached by these types of attacks. Consequently, this may give other companies the false impression that such attacks happen only occasionally. A typical example of targeted attacks, common in recent years, are DDoS as a Service – attacks, which are sponsored by one company to attack the website of another, with the effect of disrupting business and directing customers away from the targeted company and (possibly) towards the attacker’s “employer”. These are criminal tactics, and the attackers know very well which business areas to target for maximum gain.
There are of course other approaches. Take the example of the British National Health Service, which has become a frequent target of ransomware attacks. Digitization of health services has resulted in a situation where the malicious encryption of medical data may lead to a halt in medical interventions and surgeries. Under such conditions, targeted organizations are often more inclined to pay a ransom for the “hijacked” patient data.
Even in small European countries like Slovakia, attacks often focus on corporate accounting and finance departments. One documented spear phishing technique has been to address these departments with an email or an SMS in the name of the company’s CFO, urging the relevant employee to pay an invoice received from a dummy firm. The money that gets “massaged” out of the legitimate company is then withdrawn by the dummy company’s account.
Innovative approaches to old tricks
In many rural areas worldwide, one quick glance at powerlines will reveal how easy it is to make illegal connections to the power grid. As of late, cyberattackers have followed a similar model, focusing their resources on illegally mining various cryptocurrencies, which have proven to be highly popular in the public’s imagination.
A more complex example was a targeted attack meant to infect StatCounter, which provides a service very similar to Google Analytics and uses a special script legitimately placed on websites to obtain data about website visitors. In this case, attackers successfully breached StatCounter and subsequently gained access to the service’s end users by injecting JavaScript code in all websites that use Stat Counter’s service.
The problem came to light when visitors navigated to the now compromised websites which contained the infected scrip, and who’s devices then began covertly mining bitcoins for the attackers. During the second stage, the attackers proceeded to steal bitcoins directly from infected devices when they attempted to access a popular cryptocurrency exchange. To get an idea of the scale of such an operation, StatCounter can be found on more than two million websites.
Such an attack means that system resources of infected devices at the company legitimately using the service are additionally tasked to mine. This may not concern only computers, but also mobile devices and especially servers. The subsequent cryptomining accelerates wear and tear on devices and also increases electricity bills. In addition, we should not forget that malicious cryptomining code is usually capable of uploading other types of malicious script onto the network.
Investigations may take months and are looking for a needle in a haystack
When a large company falls victim to such an attack, it is necessary to carry out a complicated investigation of what happened and how the company has been affected. Research shows that it takes about 150-200 days for companies to find out they’ve been infected. Further investigation regarding the method by which the company was infected and where the malicious code originated may take even longer.
Facing such substantial risks, large companies should leverage solutions like ESET Dynamic Threat Defense to detect new, never before seen threats and EDR tools like ESET Enterprise Inspector (EEI) to monitor all the data from the corporate network collected by ESET Endpoint Security, and perform long-term analysis of this data in the broader context of the enterprise. EEI is a tool for retrospective forensic analysis and provides the affected company with information on how the mechanism was introduced and the moment an infection was initiated.
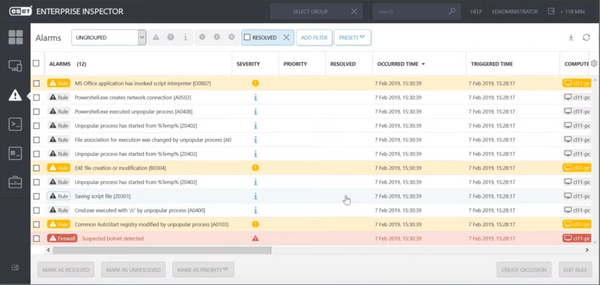
[picture description: Via ESET Enterprise Inspector, administrators can determine precisely how suspicious code was introduced on a corporate network.]
A growing demand for forensic tools investigating network security
ESET is seeing a big demand for security products able to detect network anomalies. This concerns not just anomalies in the behavior of applications on the network, but also in the behavior of people active on the network. Subsequently, it is up to a security expert to assess the information to find out whether action should be taken. Regardless of sophistication, successful attacks are usually well-conceived. “First, you may see a small hint or indication, which appears on the network. It may remain idle for a long time. However, its internal clock will eventually communicate that it is the right time to connect with its control server,” explains Michal Jankech, Chief Product Manager, ESET. “This is one of the reasons why it is so complicated to find out what caused an infection in the company.”
Now, thanks to specialized EDR software, the company is able to identify unknown executable files that have appeared on its network are communicating with a server in a country where the company has no business relationships. Assessing and filtering out such disturbances is a critical, although difficult, task. If left unmonitored, something may slip through at your company’s peril.
“Nowadays, every customer demands better insight into their network. They work under the assumption that no prevention is 100% secure and want to know what else deserves their attention,” adds Jankech. ESET Enterprise Inspector, part of a special corporate protection package called ESET Targeted Attack Protection, is designed to protect organizations from targeted attacks and persistent threats. Managed from a single console, the package provides comprehensive insight that is needed for the effective protection of a corporate network.