What is Retefe malware?
Retefe (detected by ESET as JS/Retefe) is usually spread as an email attachment pretending to be an order, invoice or similar file. It executes a Powershell script which modifies browser proxy settings and installs a malicious root certificate which claims to be issued by a well-known certification authority, Comodo. (Some variants may also install Tor and Proxifier, and schedule them to be launched automatically through the Task Scheduler).
The result of these techniques is a Man-in-the-Middle attack, where the infected user makes a connection to an online banking webpage that matches the list in the configuration file of Retefe. The malware modifies the banking webpage displayed to the user. Subsequently, it attempts to harvest logon credentials and – in some cases – tries to trick the user into installing the mobile component of the malware (detected by ESET as Android/Spy.Banker.EZ). This mobile component is used to bypass two-factor authentication via mTANs.
All major browsers, including Internet Explorer, Mozilla Firefox and Google Chrome, are affected. You can find more details on our blog WeLiveSecurity.com.
Is my computer infected?
You can check your computer for Retefe indicators of compromise:
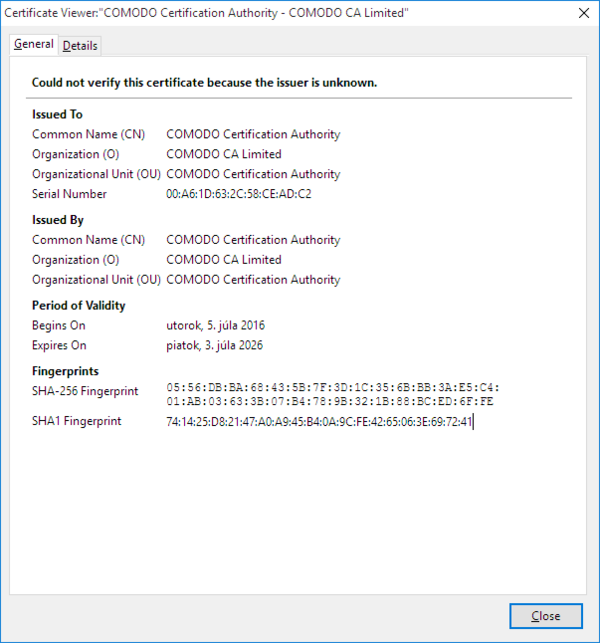
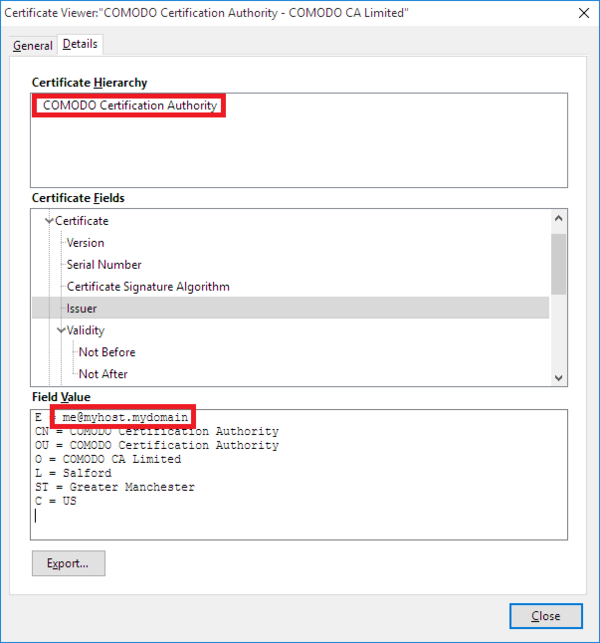
- 1 Check for presence of one of the malicious root certificates claiming to be issued by COMODO Certification Authority, with the issuer’s email address set to me@myhost.mydomain:
- For Mozilla Firefox, go to the Certificate Manager:
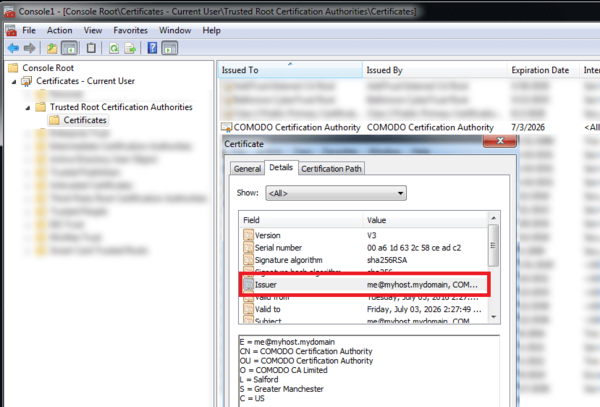
For other browsers, look in the system-wide installed root certificates through MMC (Microsoft Management Console):
So far, we have seen two such certificates with the following details:
- Serial number: 00:A6:1D:63:2C:58:CE:AD:C2
- Valid from: Tuesday, July 05, 2016
- Expires: Friday, July 03, 2026
- Issuer: me@myhost.mydomain, COMODO Certification Authority, …
and
- Serial number: 00:97:65:C4:BF:E0:AB:55:68
- Valid from: Monday, February 15, 2016
- Expires: Thursday, February 12, 2026
- Issuer: me@myhost.mydomain, COMODO Certification Authority, …
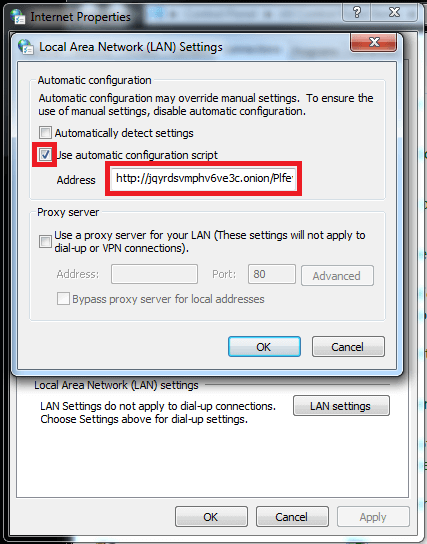
- 2 Presence of malicious Proxy Automatic Configuration script (PAC) pointing to a .onion domain
"http://%onionDomain%/%random%.js?ip=%publicIP%"
where %onionDomain% is an onion domain randomly selected from the configuration file
%random% is a string of 8 characters from alphabet A-Za-z0-9
%publicIP% is the user’s public IP address
For example: "http://e4loi7gufljhzfo4.onion.link/xvsP2YiD.js?ip=100.10.10.100"
- 3 Check for presence of Android/Spy.Banker.EZ on your Android device (can be checked using ESET Mobile Security)
or by using
You can use this tool created by ESET to automatically check for Retefe infection indicators mentioned above.
After downloading the ZIP archive, extract it and launch the retefe-checker.js JavaScript.
*The Refete Checker is a tool created by ESET (hereinafter referred to as “Tool”) provided to you at your request. By clicking the button “DOWNLOAD RETEFE CHECKER”, you agree that you use the Tool on an “as is” basis. Although we do our best to provide the best results, 100% accuracy is not possible, and thus we don’t guarantee it with the Tool. Under certain circumstances, some known indicators of compromise might not get discovered by the Tool; likewise, it is possible that the Tool can generate false alarms. By using the Tool, you agree that ESET can not be held responsible for any damage that might arise in connection with the test, its result or with any advice we might provide in connection with this Tool.
What should I do if my computer is infected by Retefe?
- 1 If you are using any of the services from the list of targets below, change your logon credentials as well as check for suspicious activity (e.g. for fraudulent transactions in your online banking).
- 2 Remove the Proxy Automatic Configuration script (PAC):
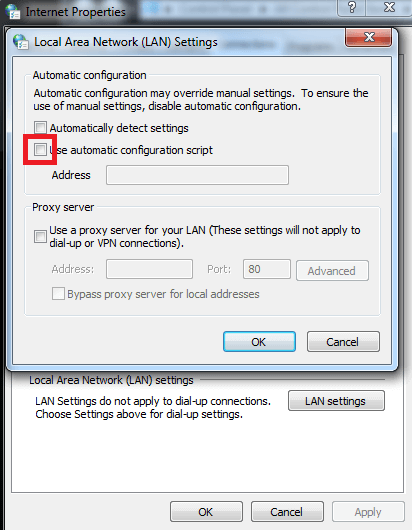
- 3 Delete the above mentioned certificate.
- 4 For proactive protection use reliable security solution with dedicated banking and payment protection.
And don’t forget to protect your Android device as well.
*.facebook.com
*.bankaustria.at
*.bawag.com
*.bawagpsk.com
*.bekb.ch
*.bkb.ch
*.clientis.ch
*.credit-suisse.com
*.easybank.at
*.eek.ch
*.gmx.at
*.gmx.ch
*.gmx.com
*.gmx.de
*.gmx.net
*.if.com
*.lukb.ch
*.onba.ch
*.paypal.com
*.raiffeisen.at
*.raiffeisen.ch
*.static-ubs.com
*.ubs.com
*.ukb.ch
*.urkb.ch
*.zkb.ch
*abs.ch
*santander.co.uk
*shkb.ch
*smile.co.uk
*szkb.ch
*tescobank.com
*ulsterbankanytimebanking.co.uk
*valiant.ch
*wir.ch
*zuercherlandbank.ch
accounts.google.com
clientis.ch
cs.directnet.com
e-banking.gkb.ch
eb.akb.ch
ebanking.raiffeisen.ch
hsbc.co.uk
login.live.com
login.yahoo.com
mail.google.com
netbanking.bcge.ch
onlinebusiness.lloydsbank.co.uk
tb.raiffeisendirect.ch
uko.ukking.co.uk
urkb.ch
www.banking.co.at
www.hsbc.co.uk
www.oberbank-banking.at
wwwsec.ebanking.zugerkb.ch