How many connected devices are on your network?
Whether you use IoT devices knowingly or not, the security of those devices is important not only for your network but also for the entire internet. If you use the internet for online shopping, social media, or listening to music, you should care if your Internet of Things (IoT) devices are secure.
It’s possible that you already have either an IoT device connected to your home network, or have other network capable devices in your home and don’t even know it. Some examples of connected devices that you may have in your home include smart TVs, webcams, gaming systems, home audio speakers, and even thermostats, vacuums and refrigerators!
These devices are usually designed with a simple setup and configuration, allowing you to plug it in and quickly begin using it, and just as quickly forget that it is connected to your home network.
As sales of consumer IoT devices outpace personal computers, tablets and even mobiles, they provide cybercriminals an expanding threat surface made even more attractive due to their lack of cybersecurity controls, infrequent patching and updating for security issues.
The fact that consumers don’t realize, or forget, that their devices are connected to the internet opens further opportunities for these devices to become an “inside man” to bypass firewalls and access other devices on your network.
Use Connected Home Monitor to detect IoT vulnerabilities
There is a new option to help protect your IoT devices, your home network, and even your favorite shopping or social website—ESET has enhanced the Connected Home Monitor feature within its recently released home products, available to try or upgrade to for free.
The Connected Home Monitor feature includes IoT vulnerability detection, a router-connected smart devices test, and a catalog list of connected devices on your network.
It’s possible you don’t remember connecting a device to your network, and it’s also possible that one of your devices has security vulnerabilities. Whether you are an ESET customer or not, you can use a free trial of any of our products to test this for yourself.
From the ESET main menu, click Tools, choose Connected Home Monitor, and then click Scan your network to see a list of your connected IoT devices:
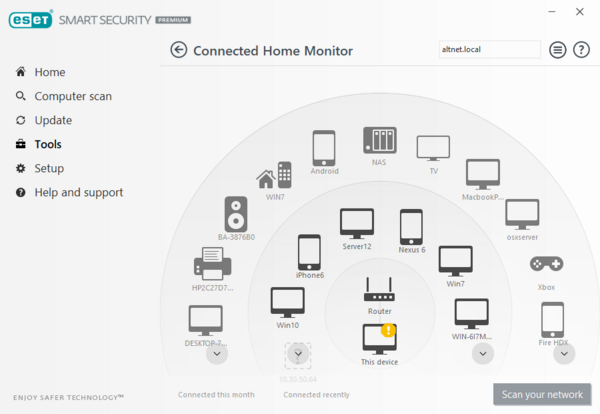
A list of devices connected to your network will be shown along with a categorization of the connected devices by type.
Why this feature is needed
Increasingly, consumer IoT devices are being used by cybercriminals for illegal activity. However, there is a common misconception that if you are not a criminal, or “have nothing to hide,” that you won’t be a target of cybercriminals or don’t need to worry about the security of your network. This is not true. Even if you have nothing of value on your network-connected devices, they can be misused to access paid services on your behalf, or their computing power and your internet connection might be misused to attack others. In either case, you could be held responsible for any possible charges made for paid services, as well as “charges” arising from any unlawful use of your computer or internet connection. The Dyn DDOS demonstrated the potential for misuse last year, and the recent news about Reaper further illustrates this today.
Just last year, many popular websites were taken offline by a botnet, including Twitter, Pinterest, Reddit, GitHub, Etsy, Tumblr, Spotify, PayPal, Verizon, Comcast, and the PlayStation network. Since then, ESET has received reports of computers and devices being used for cryptocurrency mining (for example, Monero or Bitcoin).
Here comes the Reaper
This year, a new botnet has been identified, called Reaper. All of these botnets are sinister because they are infecting not only computers and routers but are also targeting IoT devices. However, you should be concerned with just about anything that connects to the internet such as smart TVs, webcams, and all of the other devices mentioned in this article.
Why should you care about your devices being part of a botnet? If you have ever received spam email from your friend, were informed that your account is sending spam, or you have tried to access one of the popular websites mentioned above and couldn’t, you should care. How would you like to know that your devices are partly responsible for generating spam or bringing down major websites on the internet? How would you feel knowing that your computers or IoT devices are serving as a hosts for a cybercriminals’ activities?
There are many statistics regarding the total number of IoT devices now in use worldwide, but for the average consumer, you should be concerned by only one number… how many smart devices (IoT) you have, and whether they are part of the problem.
Detection is key since new vulnerabilities are discovered frequently. However, it’s too difficult to search through lists of vulnerabilities and fixes for all of your IoT devices, and to know which vulnerabilities affect your particular router, gaming system, Blu-ray player or smart TV… this is where ESET Connected Home Monitor comes in.
Detection is essential for IoT security
The Connected Home Monitor feature included in ESET Internet Security and ESET Smart Security Premium enables you to test your router-connected smart devices for security issues such as known vulnerabilities and then suggests options for fixing them.
The enhanced feature is continuously updated to detect and alert you to new devices connected to your network, as well as the latest vulnerabilities affecting your devices. If a vulnerability is found in a device, ESET will report the cause and possible steps you can make to fix it, such as changing default configurations or updating the device’s firmware from the manufacturer.
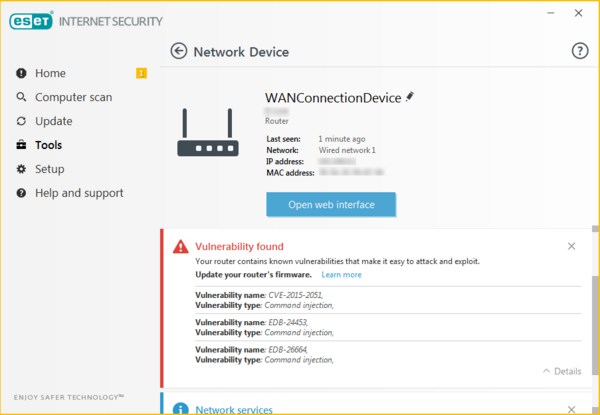
You can try ESET for free to test your IoT devices and to catalog the devices connected to your network. With ESET and Connected Home Monitor, you can continually scan and test your home routers and connected devices to help defend against any new vulnerabilities from Reaper or other botnets in the future.