It’s 3 a.m., and you’ve just received a call – it’s the head of IT ops, alerting you that a security breach occurred during off hours. Since you’re the security-monitoring analyst of a business’s IT operation, you must put some work in, so you rush to the office.
At the office, the situation is catastrophic – the breach progressed prior to your arrival, and it seems like devices are being encrypted by ransomware. Since you’re all alone, with other team members at home, you must act swiftly while thinking: How could this have happened? Everything seemed to be normal yesterday. No alerts about malicious behavior…or at least, that’s what it looked like. Who has the time to sift through all that noise anyway?
As you try to quickly contain the breach, however, you forget to transfer critical log files to a separate drive. Thinking that it won’t matter, you call the head of IT and say that all is well and go home, enjoying the rest of your allotted sleep time.
However, you’ve just made several mistakes, which will come back to bite you as soon as the follow-up – digital forensic incident response – takes place.
Setting the stage
Let’s sketch the situation at our security analyst’s firm:
- It’s a midsized company employing a very small generalist IT team with one dedicated security staff.
- The security monitoring analyst has only basic knowledge of detection tools. Meanwhile, they’re running a whole security stack, which requires time, effort, and people to use.
- The same analyst is also the only one receiving notifications in an email format, checking them occasionally.
With the stage set, let’s return to the lonely analyst and see where they made their mistakes.
Incident response mistakes
First, any cyber-minded expert would say that having a mid-sized company mostly protected by a single member of staff is a red flag. Considering how many tasks there can be with detection & response alone, often representing thousands of alerts, it’s not a job for one.
Mind you, with a solution like ESET Inspect, which can organize detections according to their severity, this wouldn’t be such a problem – especially if the person working with the EDR/XDR was experienced enough to know when and how to react…which our analyst wasn’t.
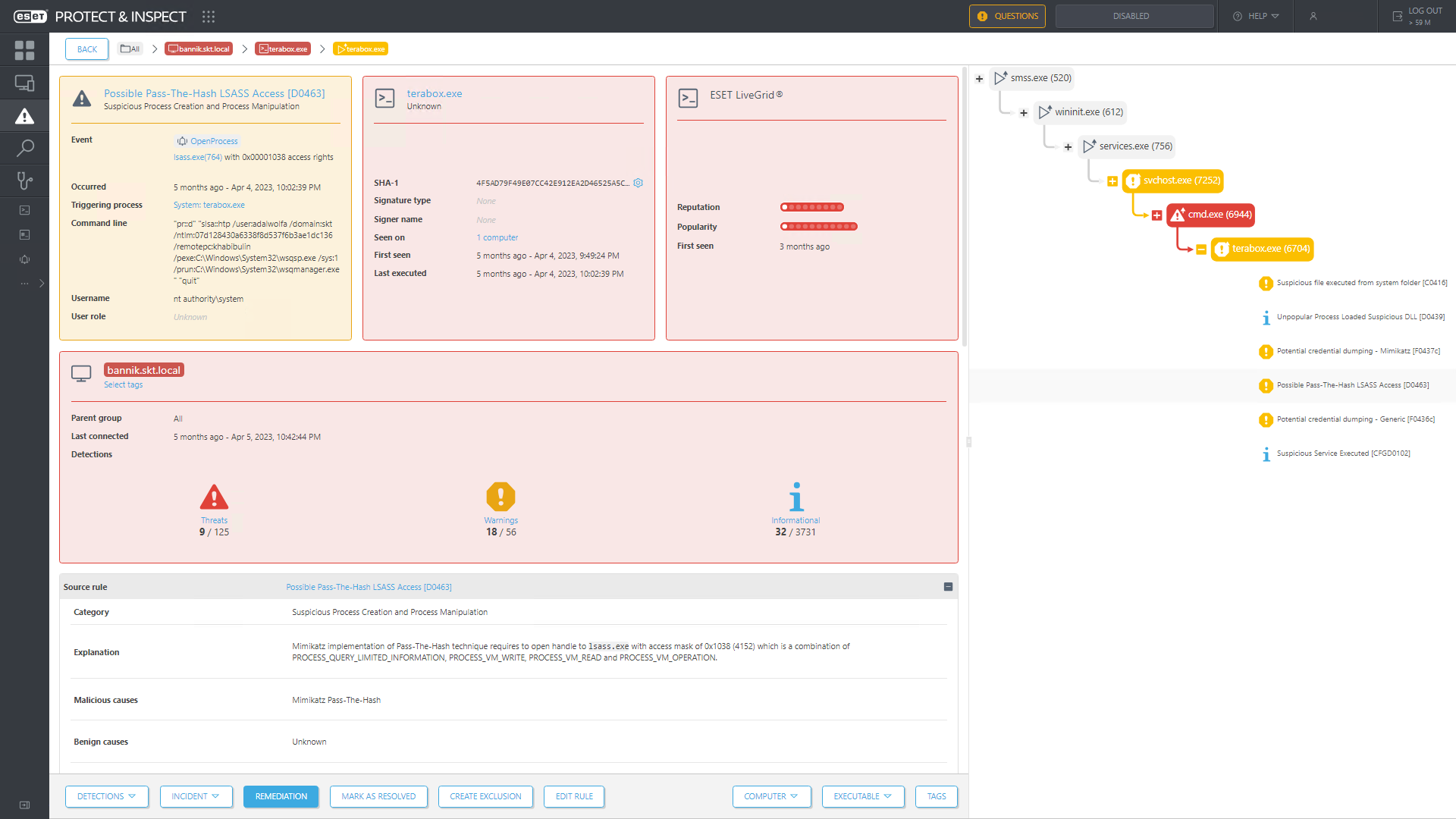
For example, a sophisticated incident such as a ransomware attack could begin simply as the exploitation of a remote desktop service (RDS) application server or a VPN, with attackers later downloading tools onto the PC that’s hosting the service to compromise the entire network. An EDR/XDR solution should flag such behavior and send out a notification. However, if the analyst doesn’t react, or it gets lost in noise generated by their platform, then the blame is certainly not on the product.
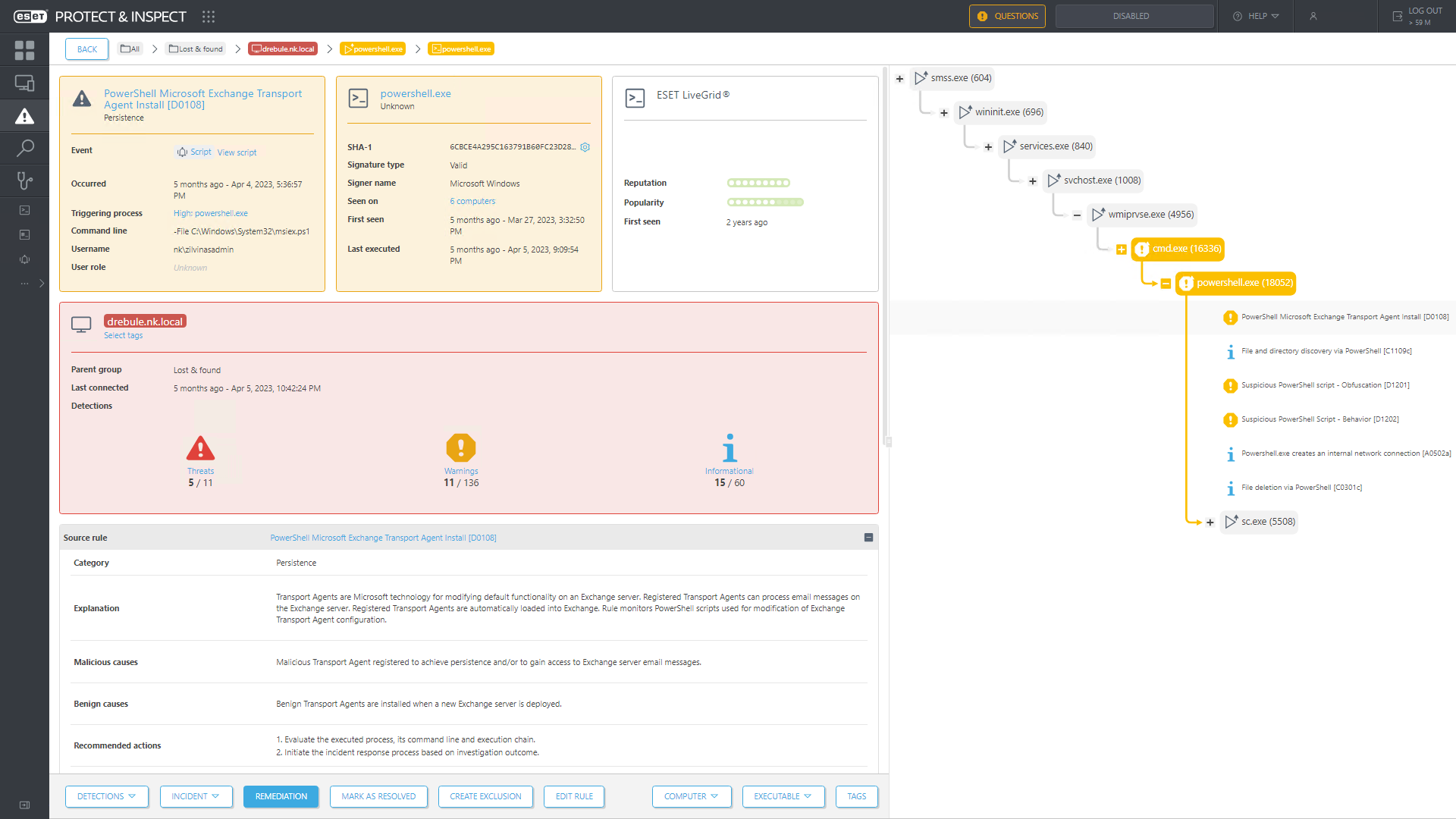
Second, ransomware actors like to commit multi-staged attacks, seeking to evade detection by changing up their tactics – using fileless techniques or moving through a network seemingly undetected. The security analyst should have notified the rest of the team, as standing against an operation-breaking incident alone is a fool’s errand. Who knows if the right decisions had been made?
Third, every piece of evidence must be accounted for in a timely manner. Without informing and handing those critical log files to the rest of the team on time, the analysts broke the chain of custody, raising questions about the integrity of the evidence. During legal proceedings, a lawyer or insurance agent could raise this as an issue, since it highlights both a problem with timely reporting and a lack of oversight, damaging a business’s claims.
What is digital forensic incident response (DFIR)?
All of this and more are what a digital forensic incident response process can uncover. If the question concerns an incident’s origin, looking to prevent future occurrences, DFIR offers that needed critical look.
While incident response is immediate, digital forensics follow closely, enabling analysts to investigate the who, what, where, and why of an incident. In essence, it works much like standard investigation at a crime scene, collecting evidence through a chain of custody and informing the impacted business of the efficacy of their response processes while satisfying both compliance and insurance expectations with duly documented assessments.
For instance, an analyst could work with ESET Inspect and manually collect logs (from other ESET products) to conduct DFIR, auditing an entire incident’s footprint. This helps find gaps in security and build future resilience.
DFIR is not just forensics
While the goal of digital forensic investigations is to support cyber resilience, it’s also to prevent potential legal risks. Every action taken during an incident response must be recorded to ensure that evidence can be trusted and verified later. The consequences of failing to do so could lead to heavy fines, especially if the documentation is problematic, as it was in the case of the Intercontinental Exchange, when it failed to follow proper procedures in light of the SEC’s disclosure practices.
A DFIR team would make copies of data before analysis, preventing the originals from being tampered with by analytic or incident response processes. Remember, a single analyst’s misstep could jeopardize an entire investigation, which is why forensics put an emphasis on clear documentation.
Preventing mistakes
Is our story far-fetched? Not really. SMBs often find themselves in the crosshairs of threat actors, with both a lack of cybersecurity budget and skilled personnel to cover their entire operation. It’s not a secret that outsourcing to a managed service provider (MSP) has been a popular choice for this reason.
In fact, cyber insurers themselves have started to encroach on this area for this reason and more – offering MSPs of their own. The benefit is an existing close security relationship and oversight, which guarantees the insurers a lot of wiggle room and potentially more security for their partners.
However, an MSP, unlike a mature SOC operation, is not fully equipped to provide services such as DFIR (it’s not their main focus).
For this, there are Managed Security Service Providers (MSSPs) or even Managed Detection and Response Services (MDR), which typically have dedicated teams and tools for it. It’s more than that, as they’re manned by top experts capable of handling an incident’s entire lifecycle, and they’re less likely to commit the mistakes of our lone security monitoring analyst.
ESET offers remote DFIR assistance as part of its ESET MDR Ultimate service – an Enterprise-level SOC – enabling end-to-end digital security with proactive threat hunting, perfectly combining ESET technology and digital security expertise to effectively respond to any threat 24/7.
Learning from your mistakes
All in all, DFIR serves a very important role during the incident response process, one that puts all the ducks in a row – establishing an incident’s source, steps taken, and the underlying process gaps or security holes to be patched to prevent a future occurrence. What’s more, such post-mortems also satisfy compliance asks and judiciary proceedings, giving business a leg up in such situations.
The efficiencies and knowledge unlocked by DFIR go toward building a prevention-first posture, preventing mistakes such as those committed by our security analyst, better preparing a business against tomorrow’s threats today.









