1bn+
users worldwide
400k+
business customers
ESET Dynamic Threat Defense
provides another layer of security for ESET products like Mail Security and Endpoint products by utilizing a cloud-based sandboxing technology to detect new, never before seen type of threats. Future proof your company IT security with:

Behavior-based Detection

Machine Learning

Zero-day Threats Detection

Cloud Sandbox
Unparalleled speed
Every minute counts. That is why ESET Dynamic Threat Defense is designed to analyze the majority of samples in under 5 minutes. If samples were previously analyzed, it simply takes a few seconds until all devices at your organization are protected.
Full visibility
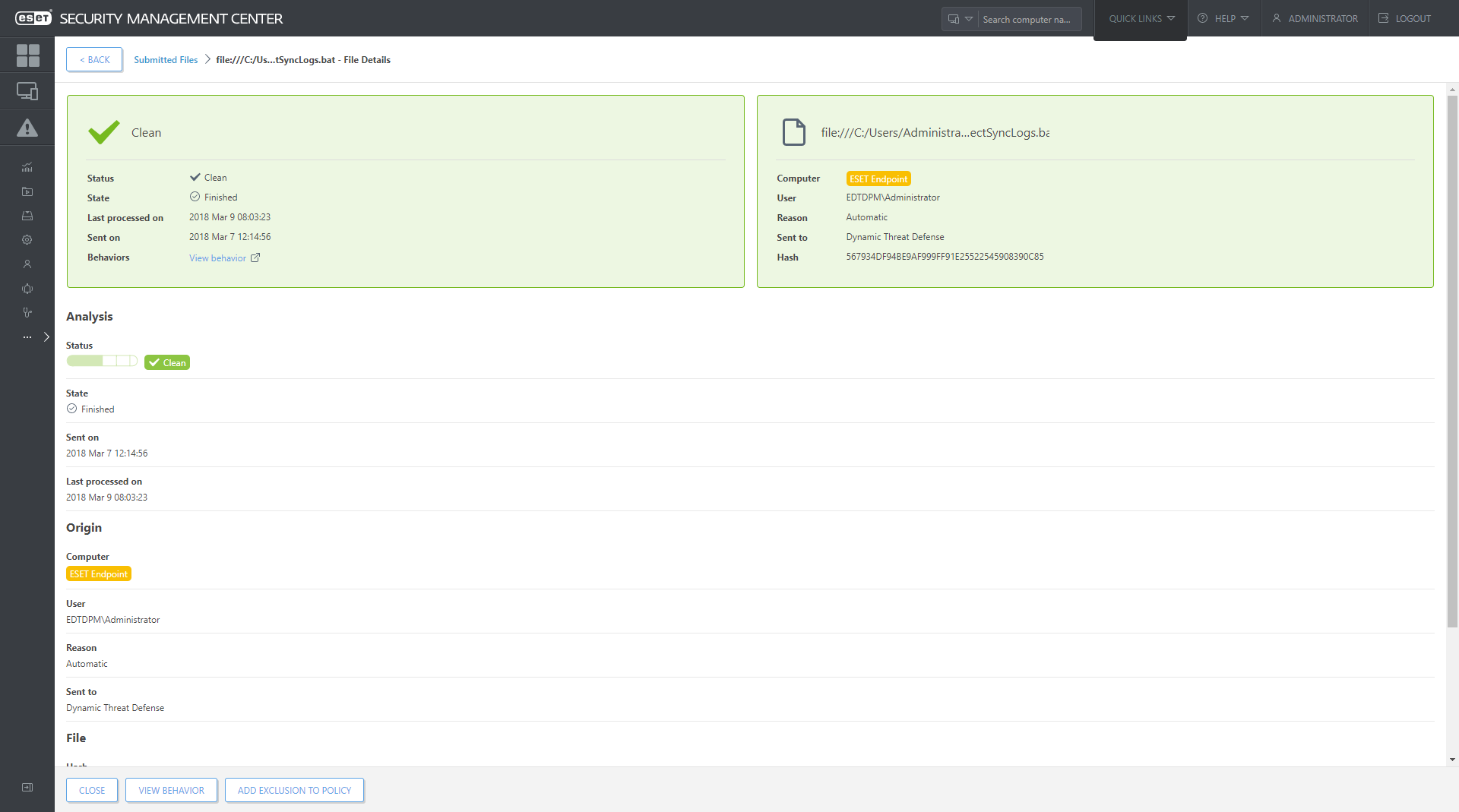
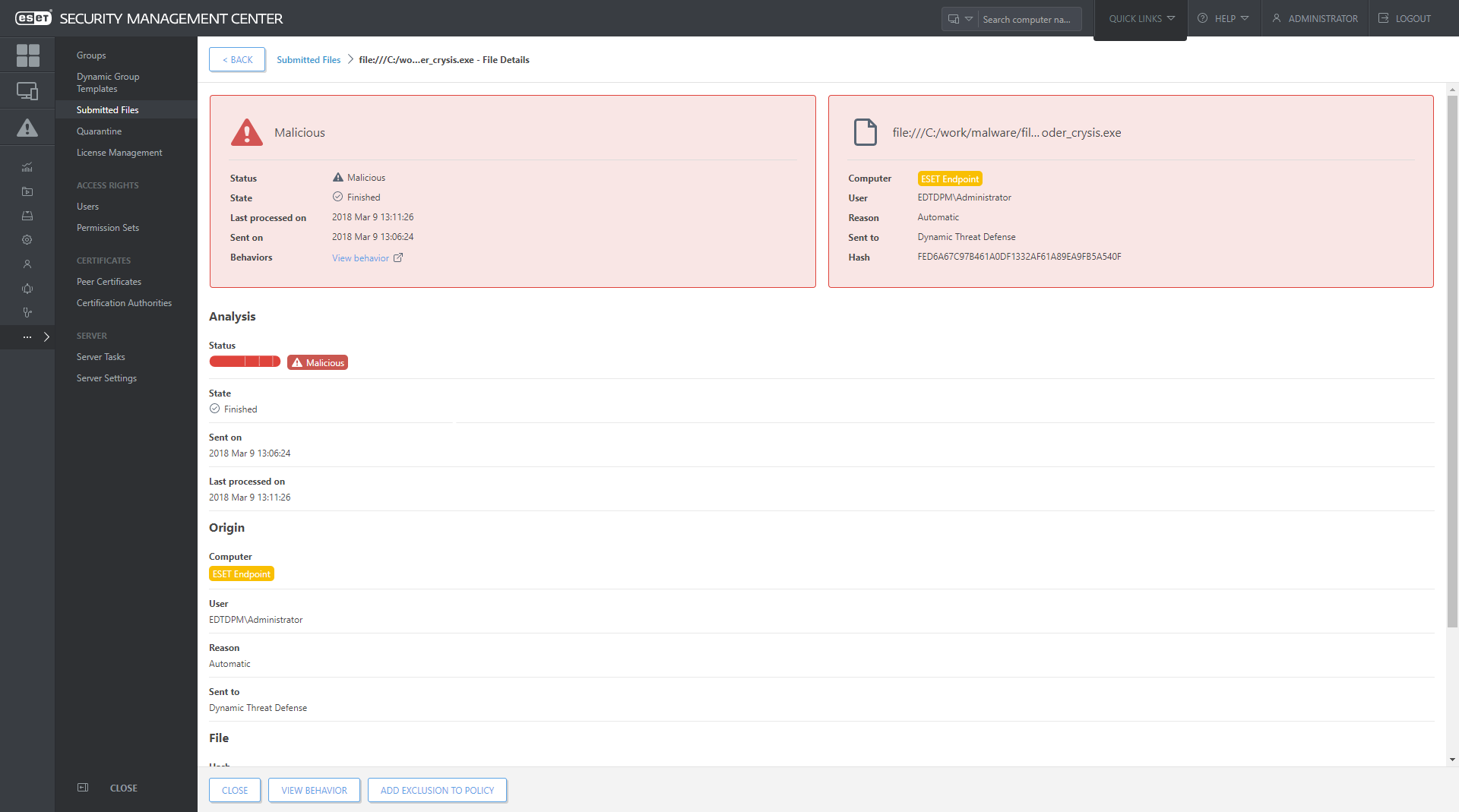
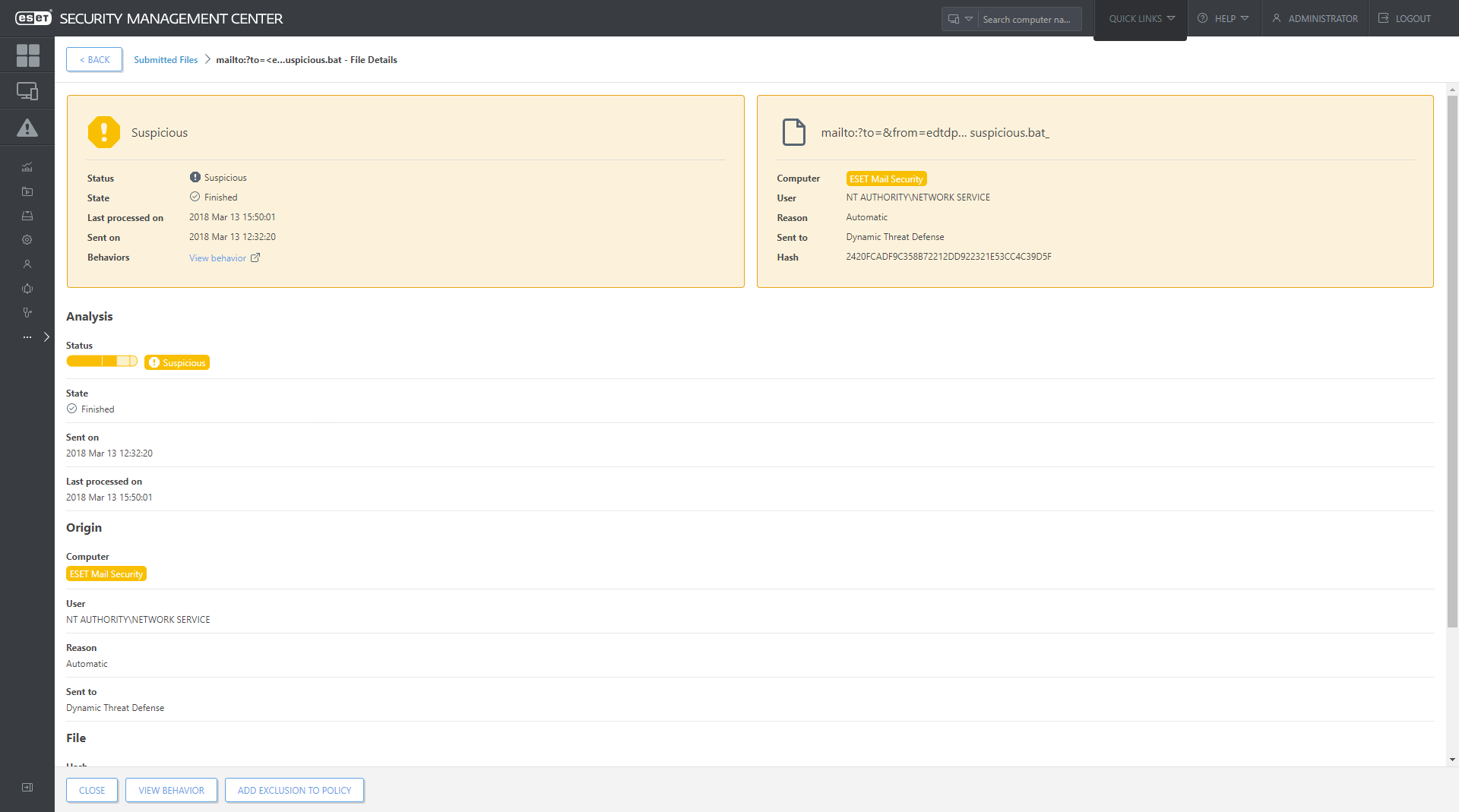
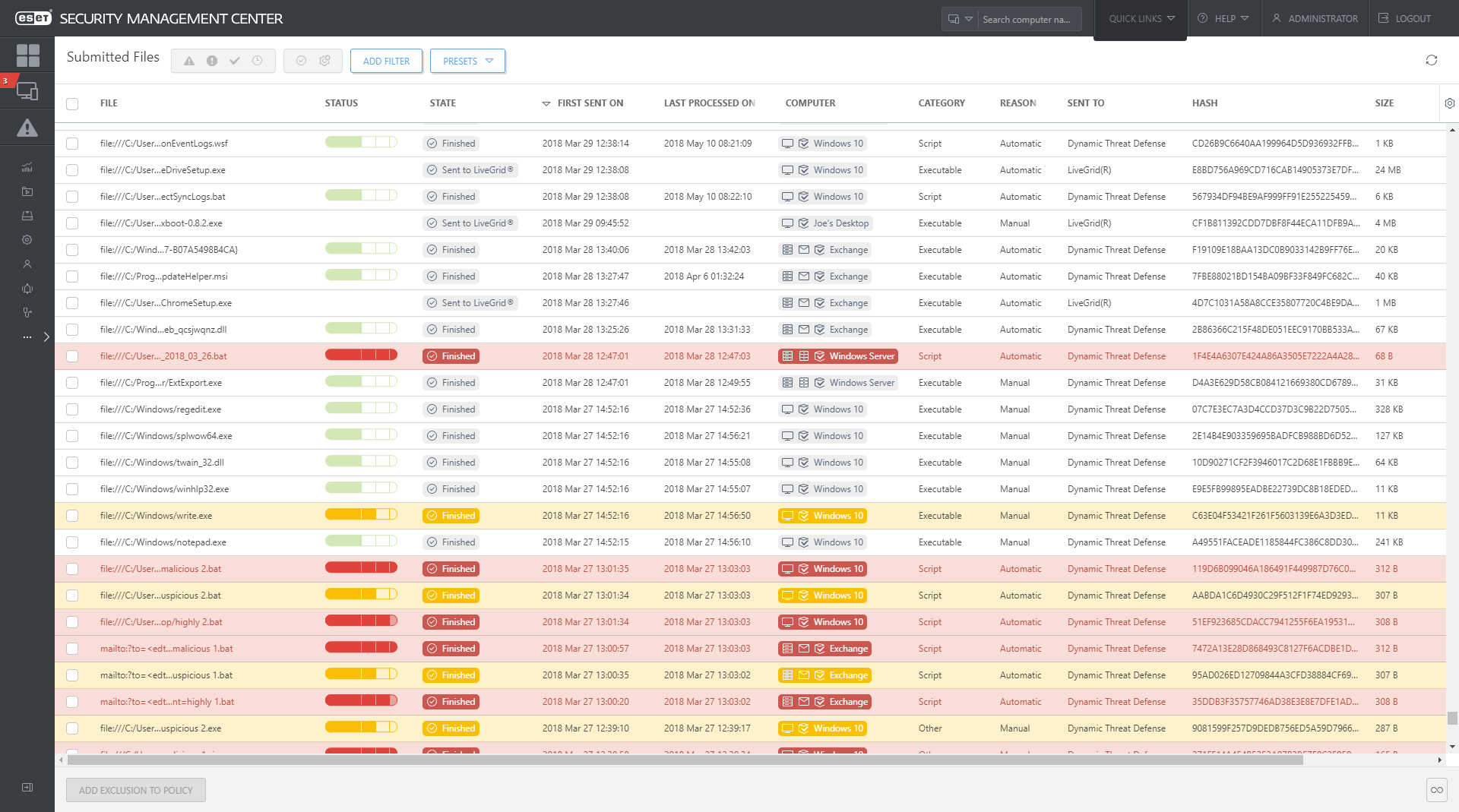
Every sample analyzed by ESET Dynamic Threat Defense is listed in the “Submitted files” section of ESET Security Management Center, which also provides transparency for all data sent to ESET LiveGrid® - cloud malware protection system.
Use cases
PROBLEM
Ransomware tends to enter unsuspecting users’ mailboxes through email.
SOLUTION
- ESET Mail Security automatically submits suspicious email attachments to ESET Dynamic Threat Defense.
- ESET Dynamic Threat Defense analyzes the sample, then submits the result back to Mail Security usually within 5 minutes.
- ESET Mail Security detects and automatically remediates attachments that contain the malicious content.
- The malicious attachment never reaches the recipient.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
The ESET difference
Automatic protection
The endpoint or server product automatically decides whether a sample is good, bad or unknown. If the sample is unknown, it is sent to ESET Dynamic Threat Defense for analyzing. Once analysis is finished, the result is shared and the endpoint products respond accordingly.
Mail Security protection
Not only does ESET Dynamic Threat Defense work with files, but it also works directly with ESET Mail Security, to ensure that malicious emails are not delivered to your organization.
Mobility
Nowadays, employees are constantly traveling and not on premise. That is why ESET Dynamic Threat Defense is able to analyze files no matter where users are. The best part is that if anything malicious is detected, the whole company is immediately protected.
Tailored customization
ESET allows per-computer detailed policy configuration for ESET Dynamic Threat Defense so the admin can control what is sent, and what should happen based off the received result.
Explore our customized solutions
Please leave us your contact details so we can design a personalized offer to fit your requirements.
No commitment.
Looking for the complete security of your network?
Related enterprise-grade solutions
ESET Dynamic Endpoint Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
ESET Dynamic Mail Protection
- Security Management Center
- Mail Security
- Cloud Sandbox Analysis
Related products and services
- ESET Security Management Center
Real-time network security visibility, reporting and management on a single screen. - ESET Dynamic Threat Defense
Cloud-based sandboxing technology detects never before seen or zero-day threats. - ESET Mail Security
Powerful server malware protection, spam filtering and email scanning for all major email platforms. - Premium support
Gives you 365/24/7 access to customer care specialists with years of experience in IT security.
Stay on top of cybersecurity news
Brought to you by awarded and recognized security researchers from ESET's 13 global R&D centers.