Protect your business with ESET
Multilayered technology, machine learning and human expertise combined with automated security management

Powerfull Endpoint protection for all devices

Advanced File server security




Small and medium-sized businesses are now increasingly attractive targets for cybercriminals. They are more valuable targets for cybercriminals than consumers, and more vulnerable than large enterprises.
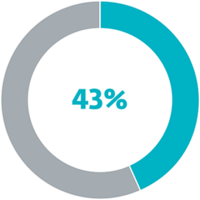
43% of victims in data breaches are SMBs.
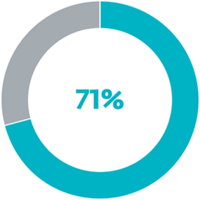
71% of breaches are financially motivated
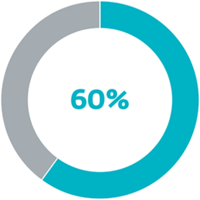
60% of victims paid the ransom demanded.
Keep your network clean and protect your endpoints (computers, smartphones, tablets and fileservers) against emerging threats.
ESET protection comes with the powerful Web Control, Firewall and Anti-Spam filter to provide additional layers of protection for a company network and your mobile workforce.
Encryption prevents the data from being readable and misused, should that data fall in the wrong hands.
ESET Endpoint Encryption is a simple-to-use encryption for companies large and small, which supports full disk encryption (FDE), file/folder encryption, email encryption and USB encryption.
81% of data breaches were caused by weak or stolen passwords. Two-factor Authentification helps to strengthen your password access.
ESET Secure Authentication Is a mobile-based two-factor authentication system which provides additional security for accessing a company network and sensitive data.

Monitors applications and processes that try to modify data, blocks suspicious activity, and alerts you

Third-party tests prove that ESET endpoint protection places the lightest load on your network

Quality service and fast response in all markets from high-trained professionals at your disposal

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 4,000 mailboxes

protected by ESET since 2016
more than 14,000 endpoints
ISP security partner since 2008
2 milion customer base

blocks access to a device screen, other than to see the malware user interface.

changes the device's PIN code, rendering its content and functionality inaccessible.

encrypts the MBR (Master Boot Record) and/or critical file system structure, and thus prevents the user from accessing the operating system.

encrypts user files stored on disk