Over the last few months malicious software has created mayhem for many network and security administrators around the world. Numerous attacks, such as Wannacry (a.k.a. WannCrypt), have created an increased need for data on the versions of software and patch levels installed on endpoints.
Software vendors release patches to fix bugs or security vulnerabilities and to improve stability and performance. Patches can be implemented automatically or manually, depending on what the update involves or the settings chosen by the end user. Software designed for consumers often includes automated update mechanisms, this helps avoid people declining important updates that they may not fully understand the necessity to install.
Corporate and small business environments have different requirement when it comes to patch management. Consider all the applications that a company uses, some of them old or written in house. The teams responsible for those applications need time to ensure that patches released by software companies will not break their internal systems or the applications a business relies on. None of us like to hear the words ‘the system is down’ either at work or as a customer.
Understanding the status of the endpoint, or servers, helps businesses understand the risk that a vulnerability presents. When news breaks about the latest malicious code using a particular vulnerability to exploit a system understanding what and how many systems may be affected is critical. The ability to tell the company board and management that there are X number of vulnerable systems or that all machines are patched and safe is crucial to providing a safe and stable business environment.
There are numerous patch management systems available that gather data but here at ESET we see patch management and security being intrinsically linked.
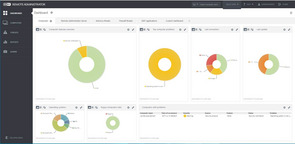
That’s why we have ESET Remote Administrator (ERA). It provides a holistic view on security and the status of the endpoint. Informing system administrators about the devices at risk and what actions may need to be taken when a vulnerability is disclosed publicly.
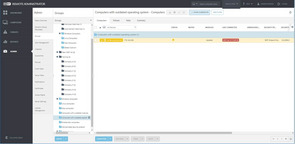
Delivering a pictorial view that can be drilled down on and showing devices not running current operating systems versions or that have outstanding security notifications will enable the business to manage and understand the exact status of their endpoints in real-time.
When Wannacry was released by cybercriminals company boards and management teams everywhere were connecting with chief security officers and administrators to find out if their organizations were vulnerable. With ERA the information is readily accessible, reporting on devices that have the correct Microsoft patch installed, or more importantly which devices do not have the correct patch installed.
Tony Anscombe, Global Security Evangelist