In late 2023, when ESET researchers discovered a novel attack method abusing the near field communications (NFC) data of Czech banking customers, they warned about the possibility of its expansion into other regions or countries.
Sadly, but not surprisingly, the worst-case scenario has happened, and threat actors are now using similar techniques all around the world. This trend is clearly demonstrated by the total number of NFC attacks reported by ESET telemetry surging more than 35 times in H1 2025 compared to H2 2024, according to the ESET Threat Report H1 2025.
Luckily, fans of contactless payments are not defenseless. With a bit of awareness and the right cybersecurity tools covering their backs, users can continue to pay wirelessly with peace of mind.
Tap to pay
NFC, or near field communication, is a short-range wireless technology that utilizes radio waves, allowing communication between devices in close proximity, typically within a few centimeters.
This invention has significantly simplified cashless payments, especially for people who never leave their smartphone behind and try to use its capabilities to the fullest.
On top of its popularity and usability, this technology is already protected by multiple layers of security such as encryption and tokenization, which prevents cards from being duplicated. The fact that the payment process requires close proximity to work makes attackers’ efforts even more complicated.
Considering overall smartphone penetration, growing adoption of cashless payments, and incorporated security, it is no surprise that the global NFC market is anticipated to grow from $21.69 billion in 2024 to $30.55 billion by 2029.
From the lab and into the wild
As always, growing trends in our digital world also attract cybercriminals, and here we are again – explaining a new threat: The scam as described by ESET researchers combines standard malicious techniques (social engineering, phishing, and Android malware) with a tool called NFCGate, creating a totally novel attack scenario.
NFCGate allows the relay of NFC data between two devices, and its original purpose wasn’t malicious. It was developed by students from the Secure Mobile Networking Lab at the Technical University of Darmstadt in Germany as a research tool.
The attack scenario starts with the cybercriminals sending SMS messages to potential victims concerning a tax return, including a link to a phishing website impersonating a bank. These links most likely led to malicious progressive web apps (PWA). These sneaky mobile apps are accessible from web browsers, thus avoiding standard vetting processes on app stores, and their installation doesn’t trigger warnings about installing a third-party application.
In this scam, malicious PWAs mimicking banking applications tricked victims to install them and insert their credentials. Once the attackers had the credentials, they gained access to the victim’s account and called the victim, pretending to be a bank employee. Using the stolen information, they tried to persuade the victim that their account had been compromised, and that to “protect” their funds, they needed to change their PIN and verify their banking card. To do so, victims were urged to download another mobile app from the link that was sent to them via SMS. This app was in fact the NGate malware, which is abusing NFCGate technology.
ESET researchers suspect that within the NGate app, the victims would enter their old PIN to create a new one and place their card at the back of their smartphone to verify or apply the change.
Since the attacker already had access to the compromised account, they could simply transfer the funds to another account, but using NGate makes the whole con much easier – attackers can access the victim’s funds without leaving traces back to their own bank account. They could simply mimic the victim’s bank card on their own device and use it for cash withdrawals or to make payments.
Farming payment cards
Despite the police arresting a member of the gang and the malicious activities being subsequently put on hold, ESET telemetry went on to detect NGate malware in other regions. And from tracing only about one detection per week, the researchers began to see dozens of them.
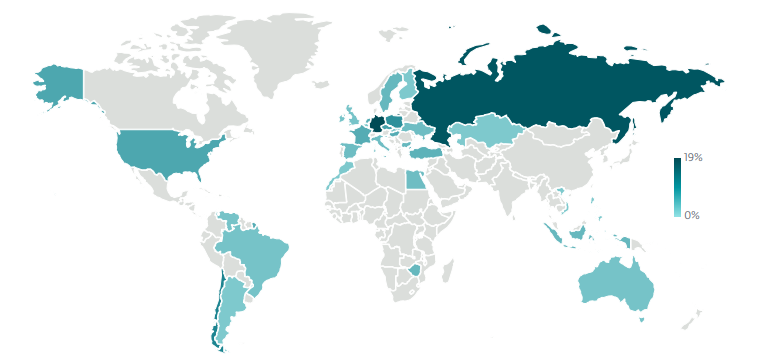
<image> Geographic distribution of NFC-related Android malware and scams in H1 2025
Inspired by the success of NGate, cybercriminals evolved this method further, making it simpler and ready to be deployed at scale. This tactic received the name Ghost Tap.
At the beginning of the process criminals use various phishing techniques, again, trying to persuade victims to enter their payment card details on fake websites and then trick them into sharing the one-time passcode meant to confirm the card for a digital wallet.
Then, with the card data and code at their disposal, the attackers register the stolen credentials in their own Apple or Google wallets, relay these loaded wallets to other devices, and make fraudulent contactless payments anywhere in the world.
This technique allows cybercriminals to stay anonymous and perform cash-outs on a larger scale. Theoretically, they could have whole farms of Android phones loaded with compromised card data making automated fraudulent transactions.
How to protect your bank account
A penny saved is a penny earned, so don’t let cybercriminals clean out your bank account so easily. Here are a few tips on how to protect your hard-earned cash from sticky-fingered attackers.
Train your eyes to spot phishing – To make NFC attacks work, cybercriminals still need to deceive their targets into downloading malicious apps and/or handing out their banking details. Learn how to avoid phishing attempts.
Set up low payment limits – Banks usually limit the amount of cash you can withdraw from an ATM each day and have algorithms to spot unusual transactions. You can enhance these protective measures even further by setting a maximum limit on how much you can purchase through contactless payments.
Protect your contactless payments – You can use RFID blockers, devices or materials designed to prevent unauthorized access to information stored on RFID (Radio-Frequency Identification) chips in debit/credit cards.
Use a reliable cybersecurity solution – A robust cybersecurity protection can discover and stop financial attacks at many stages, from phishing links to malicious apps to network attacks.
How ESET can secure bank accounts and transactions
To protect the digital lives of modern people enjoying technological advancements, ESET developed all-in-one protection called ESET HOME Security, recently honored with AV-Comparatives’ Product of the Year 2024 Award for ESET HOME Security Essential. Among many other things, it also secures Android smartphones, mobile payments, and financial transactions thanks to ESET Mobile Security for Android, which is capable of preventing financial attacks at multiple stages. Let’s see how it works:
Android antivirus with 24/7 scanning can detect all kinds of malware, including malicious applications. This powerful tool also detects NFC scams thanks to signature-based detection.
Anti-Phishing protects against malicious websites attempting to acquire your sensitive information, such as banking information or credit card details. This feature checks links coming from browsers, SMS, apps, and notifications.
Payment Protection ensures that other apps will not recognize when a financial app has been launched and will not be able to replace or read the screens of the affected app.
Security Audit helps you to monitor the device and review the permissions given to each application installed on your device to prevent security risks.
No need to return to cash
Cashless payments are quick and convenient, and users shouldn’t give up on them just because cybercriminals pull a new trick from up their sleeves. If you want to continue using tap payments without worrying about your bank account being drained, stay vigilant and protect your smartphone with a robust cybersecurity solution.







