We’ve written about spearphishing before, highlighting ESET Research’s telemetry finds concerning this insidious, highly personalized attack type.
However, the story isn’t over. In their latest findings, researchers have gone on to detail a series of successful phishing attempts by the Iran-aligned MuddyWater APT group, using a very specific attack technique — internal spearphishing. If you thought that spearphishing was a bit too surreptitious, this time, it’s even worse; targeting the trust placed between coworkers as its main weapon.
Key points of this article:
- The ESET APT Activity Report Q2 2025-Q3 2025 shows how the Iran-linked MuddyWater APT has been successful with its internal spearphishing.
- This is unique due to the high success rate of this technique, leading victims to click on and download an RMM tool or a malicious archive file.
- Internal spearphishing follows the compromise of an employee’s professional inbox, using it to send spearphishing emails to their coworkers.
- By figuratively skirting an organization’s security perimeter, MuddyWater can bypass multiple detections and gain access to copious amounts of data.
- Monitoring for this attack is troublesome, leading to numerous alerts so narrow in scope that they could remain insufficient to detect it.
- Prevention relies on human alertness, inbox hardening, and continuous authentication.
What is internal spearphishing?
Internal spearphishing, as the name suggests, is when you deploy a tailored phishing attack, but vector it not from an external email server, but from within an already compromised organizational inbox. This is a lot like a standard insider threat, but not quite.
An employee isn’t culpable here, up to a point. The compromise of a mailbox can happen either after someone steals a physical device that lacks authentication controls, or gains access to account credentials. What follows then is a takeover of the account by the perpetrator, who might send emails with malicious attachments or URLs to deliver malware or to phish even more credentials.

While the above image represents a typical urgent spearphishing email from an outside source (like a court summons), the fact that the attacker can pose as a verified employee is what makes the trickery of internal spearphishing even more believable and successful. While you might not share your password with your colleague (except with IT, maybe?), attachments and links sent by trusted collaborators could pose trouble, even to the most perceptive individuals.
It’s not just emails
While we mostly discuss internal spearphishing as an email-borne vector, modern firms also often employ other communication tools — like MS Teams, Slack, or Discord. If you’ve ever used these platforms, you know that they’re no strangers to your collaborating partners sharing stuff (PDFs, links, docs, etc.).
Did you know? More outsiders on the “inside”
Members of the Red Team at UK-based security services provider Jumpsec discovered a way to deliver malware using MS Teams with an account outside the target organization.
Even though Microsoft Teams has client-side protection, the Red Team members found a way to go around this restriction by changing the internal and external recipient ID in the POST request of a message, tricking the system into thinking an external user was, in fact, an internal account.
In a similar story, the “Chat with Anyone” feature of MS Teams is said to make phishing easier, letting external users send direct messages via email.
Therefore, it could be easy to internally spearphish one’s way through people’s inboxes at a rapid rate via multiple channels. Sure, an existing account (usually) needs to be compromised first, but, since phishing is still among the top attack vectors (confirmed by ESET MDR telemetry), assuming it won’t happen is the real vulnerability here.
Phishing for consequences
The consequences of an internal spearphishing attack lie first and foremost in the broken trust between colleagues, and they metastasize into further consequences related to persistence (including lateral movement), followed by cyber espionage in the form of data exfiltration or, perhaps, even by a ransomware attack.
Really, it all depends on what a threat actor might be looking for. The findings in the ESET APT Activity Report Q2 2025-Q3 2025 mostly indicated espionage, but there’s more mud in the waters than that.
Muddy waters all around the globe
We’re at the point in the story where we must introduce our villain — the Iran-aligned MuddyWater APT group, also known as Mango Sandstorm or TA450.
The group is mainly known for cyber espionage campaigns targeting governments and businesses across sectors in critical infrastructure (oil and gas, defense, telcos, manufacturing, etc.). MuddyWater adapts its social engineering tactics to local contexts, employing target-specific lures (spearphishing) for initial access in multistage operations, with a strong geopolitical focus in places like Nigeria, Greece, Saudi Arabia, Israel, and the United States, among others.
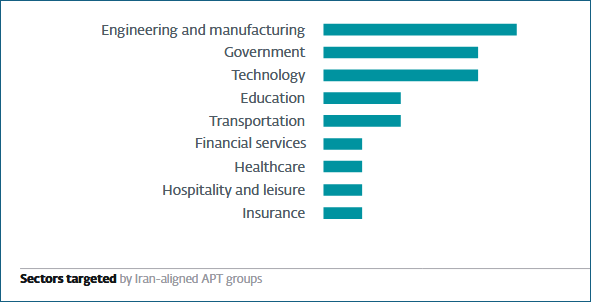
In the group’s repertoire are legitimate tools used by MSPs, like remote monitoring and management software (such as SimpleHelp, Atera, Level, and PDQ) or Ligolo, a reverse tunneling tool often used by pentesters and more. Critically, it is the use of legitimate tools that helps mask malicious activity within a corporate environment, especially when IT admins don’t know how to interpret abnormal system behavior within their EDR/XDR tools of choice.
The group also likes to leverage free file-sharing platforms like OneHub, Egnyte, or Mega, where it usually hosts installers for the above-mentioned RMM software, the links to which are contained in malicious PDF attachments to spearphishing emails.
The use of spearphishing is a running theme here. While spearphishing emails are more difficult to spot than regular phishing emails due to their custom-tailored nature, there are many ways they can be mitigated, starting with cloud-app or email-based security.

ESET also tracks MuddyWater’s use of a custom reverse tunneling tool, alongside the use of MiniDump, to obtain credentials from Local Security Authority Subsystem Service (LSASS) dumps and leverages the CredNinja penetration testing tool. Additionally, MuddyWater operators also use the VAX One backdoor, named after the legitimate software that it impersonates, including Veeam, AnyDesk, Xerox, and the OneDrive updater service.
Another running theme here is the use of legitimate IT tools. Since this is a familiar playbook of MuddyWater, such activity is relatively easy to detect and block. As mentioned above, email-borne threats can be detected by a specialized security layer, while malicious downloads can be caught early by cloud sandboxing and behavioral detection.
Our telemetry also tracks other techniques connected to the group, such as steganography, which obfuscates data in digital media such as in the pixels of images.

Image 4. These pictures aren't the same. Enhance the one on the right and notice the imperfect pixelation hiding malicious code. (Source: ESET Research).
ESET’s latest on MuddyWater
Based on the recent ESET APT Activity Report and additional ESET research, it looks like MuddyWater has been steadily getting more advanced. In its latest campaign, the group used more advanced techniques to deploy MuddyViper, a new backdoor, by using the Fooder loader to reflectively load MuddyViper into memory and execute it.
Memory-based fileless malware is much more difficult to detect, especially for malware signature-based security tools, as opposed to something like ESET’s cloud-based, AI-powered tools, including ESET LiveGuard Advanced equipped with behavioral detection.
A notable characteristic of Fooder is its frequent use of a custom delay function that implements the core logic of the classic Snake game, combined with “Sleep” API calls, intended to delay execution to hide malicious behavior from automated analysis systems. MuddyWater developers have also adopted CNG, the next-generation Windows cryptographic API, a very atypical move across the threat landscape.
During the same campaign, the operators deliberately avoided hands-on-keyboard interactive sessions, which is a historically noisy technique involving lots of mistyped commands. So, we can say that the APT group is definitely keener on staying under the radar than it was before.
Inspecting sediments, or MuddyWater’s keys to success in 2025
MuddyWater was especially successful in 2025, which can be attributed to the use of internal spearphishing messages, wherein most recipients interacted with their malicious contents, as well as their more advanced techniques.
Phishing, spearphishing, internal spearphishing … same, but different. For initial access, the latter is a very potent technique, as cybersecurity tools and security professionals are more often focused on phishing emails that come from external sources. You wouldn’t expect your colleague to try to compromise you or your workplace, after all.
Moreover, monitoring for an internal spearphishing attack is difficult, and can lead to alert fatigue or notification alerts that are so narrow in scope that their efficacy is likely insufficient to detect a number of these attacks. In a way, this is truly an attacker living off the land, using trusted access at their disposal. This goes against the basic mantra of SOC analysts, who usually expect threat actors to laterally move on from phishing to initial access within an internal network, not to wholly bypass the email perimeter and evade detection to abscond with extensive intelligence on their victims.
In short, when a threat wears a familiar face, it’s harder to spot. Unless initial access is detected by either endpoint protection, XDR, or MDR, it will take a more considerable amount of time to spot the crocodile hidden in the lake.
How to detect internal spearphishing
First, there’s no one-size-fits-all approach here. With internal spearphishing, as soon as your preventive security layers fail, you may hardly notice malicious behavior; however, there are some detection strategies that could still work:
Boost prevention with awareness
A great way to prevent account theft is to teach the employees about phishing. A good cybersecurity awareness program includes simulated phishing scenarios that include internal mails, hammering in in knowledge about phishing’s telltale signs while collecting useful information about employee behavior to devise further security measures.
Step up your authentication game
Authenticating just on boot? That’s not enough. Did you know that email clients can also be set up with additional security? Well, they can. Consider adding a passworded VPN or an additional OTP authentication step before letting the employees access their emails. While this might prove bothersome, the added layers could deter malicious actors from forcing their way in — even with harvested account credentials.
All right; but what if they steal an employee’s open laptop/work phone? Well, that’s what continuous authentication and location-based controls were made for.
Strengthen your cloud app protection
Not many know that anti-phishing protections applied by cloud security solutions can also protect against internally issued threats. For example, ESET Cloud Office Security filters for malicious contents, even for emails exchanged between two colleagues, and can check for malware on apps like Teams when exchanging files.
Extend your mail server protection
Just like with cloud app protection, securing dedicated mail servers with anti-phishing measures is another option. One effective approach is to prevent users from accessing phishing websites by filtering emails that contain malicious links. ESET Mail Security enhances this process with a sophisticated parser that scans both the message body and subject line to detect harmful URLs. Any email containing malicious files or links is automatically quarantined, ensuring that it never reaches the user's inbox.
If you doubt your prowess in catching internal spearphishers, or you want another set of eyes to keep watch over your environment 24/7, seek out an MDR service that, via a combination of AI-native detection, human ingenuity, and global telemetry, can pinpoint hidden dangers in as few as six minutes.
Revealing covert ops
Protection against MuddyWater-like campaigns is difficult, as it takes more than a basic security strategy relying on endpoint protection.
ESET’s chief recommendation for prevention has always been to layer multiple defensive measures, and the same stays true for internal spearphishing. These days, when you can’t necessarily trust your own collaboration partners’ comms, it’s better to rely on an up-rated security baseline to reveal even the most insidious troublemakers.
For more thorough insights into novel ESET telemetry and threat landscape, make sure to follow ESET Research on Twitter (today known as X), BlueSky, and Mastodon, or subscribe to our ESET Threat Intelligence feeds and APT Reports to stay on top of malicious groups like MuddyWater and its latest campaigns.









