Every freelancer and micro business owner knows how hard it is to make a living this way. Their day-to-day involves a lot of multitasking in management, sales, HR, marketing, and even PR, leaving little room to consider cybersecurity admin duties. And cybercriminals know it.
Preying on busy and stressed people, they launch increasingly sophisticated scams to steal money or data, putting businesses at risk of reputational damage, financial loss, and even bankruptcy. What’s more, with the help of AI tools, these scams can be crafted faster, made more convincing, and deployed on a larger scale. So, no, this storm isn’t running out of rain.
There’s no easy way out, especially for businesses that can’t afford dedicated IT staff or enterprise-grade cybersecurity solutions. But hang in there—you can still protect your livelihood.
The first step is to deploy an affordable cybersecurity solution tailored precisely for micro businesses. Yes, such solutions exist - like ESET Small Business Security. Second, try to carve out a little time to focus on prevention: Learn about scams targeting small offices/home offices (SOHO) and take a few proactive measures. Good thing, then, that this blog will help you with both.
Key points of this article:
- “Small is safe” is not a sound security argument. On the contrary, cybercriminals actively target small businesses and micro businesses, knowing that they often lack dedicated IT staff and robust security measures.
- Real-life stories of entrepreneurs show how cyberattacks look—just a few seconds of inattention or distraction can lead to monetary loss or a hijacked account.
- The simpler and more creative a scam is, the more convincing it can be.
- Comprehensive protection starts with a change of mindset, prevention, and a reliable cost-effective cybersecurity solution tailored to micro businesses.
Why “being too small” won’t protect you
Before we dive into scam awareness and prevention, let’s make one thing clear: Being “too small to bother with” is not a “protective layer.” It’s a fallacy; amongst the public, this is an oft-repeated argument, but that’s not actually how it works. While everyday people represent the majority of victims of cybercrime, it is largely businesses that are profiled, and not just the big players.
Why so? It’s because every business has a name, address, license, Employer Identification Number (EIN), and bank account, and it handles various kinds of customer data - all of which are immensely valuable to scammers. Even if they don’t go straight after your money, they can still sell the data on the black market or exploit it for further scams and cyberattacks.
Even so, for the majority of cybercrime at this level of complexity, attackers would be unlikely to invest too deeply. So, rather than targeted attacks, they would likely launch large-scale malicious campaigns against businesses - increasingly identified by AI - seen as easy targets.
Still not convinced? Here are some numbers:
- An estimated $444 billion has been lost to scams worldwide in the past 12 months. That’s more than Egypt’s entire GDP. (Global State of Scams 2025)
- Over 80% of U.S. small businesses have been breached in the past 12 months (ITRC Consumer & Business Impact Report 2024)
- 60% of small businesses say that they are most concerned about cybersecurity (Q1 2024 MetLife and U.S. Chamber of Commerce Small Business Index)
- More than 40% of the U.K.’s micro businesses (i.e., those with 1 to 9 employees) experienced a data breach or cyberattack in 2024 (a third of those were phishing attacks), with average short-term direct costs reaching £3,040 ($4,005) (Cybersecurity breaches survey 2025)
A real-life story: From voting in a contest to account takeover
A Cleveland-based entrepreneur—who sells granola—described to CNBC how she was scammed on Instagram in 2023. It started with a message from a small business owner she personally knew, asking her to vote in a contest. The contest was legitimate, so the entrepreneur clicked on the provided link. As it turned out, her acquaintance’s account had already been hijacked, and the same fraudulent message was sent to everyone in her contact list. After clicking the link, the entrepreneur lost her account as well.
List of scams targeting entrepreneurs and micro businesses
Phishing and spearphishing
Phishing scams trick individuals into downloading malware or giving away sensitive data like account credentials or banking info. Scammers often impersonate trusted sources, also creating a fake sense of urgency—like alerts about expired accounts—to prompt quick action. Variations include QR-code phishing (quishing), SMS phishing (smishing), and voice phishing via phone(vishing).
Phishing’s more advanced form is spearphishing, utilizing highly tailored messages based on deep background research of a target. It’s like the difference between over-the-counter and prescription medication; one’s more tailored and potent than the other.
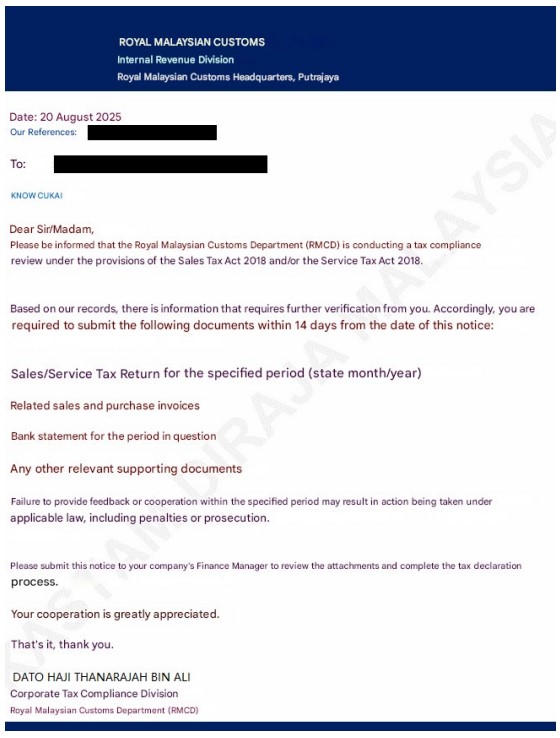
Description: Machine translation of a tax-themed spearphishing email, sent to a Malaysian organization, delivering malware.
Business Email Compromise (BEC)
In this high-risk social engineering scam, attackers impersonate trusted figures—like a company’s CEO or finance manager—to trick employees into transferring money or sensitive data. They may also pose as subcontractors or partners, or inject themselves into real communication threads to appear legitimate.
With AI and deepfake technology—including audio, video, and live calls—these scams are becoming even more convincing. In one case, reported by the Hong Kong police, scammers used a deepfake conference call to trick an employee of an international firm into paying out $25 million. While those losses are much higher than a small business owner might face, the mechanism of the scam is very relevant.
Fake invoice/supplier/vendor scams
Scammers send invoices that look legitimate, often mimicking real suppliers or vendors. Their goal is to trick businesses into paying for goods or services that were never provided. These invoices often exploit busy environments where payment approvals are rushed.
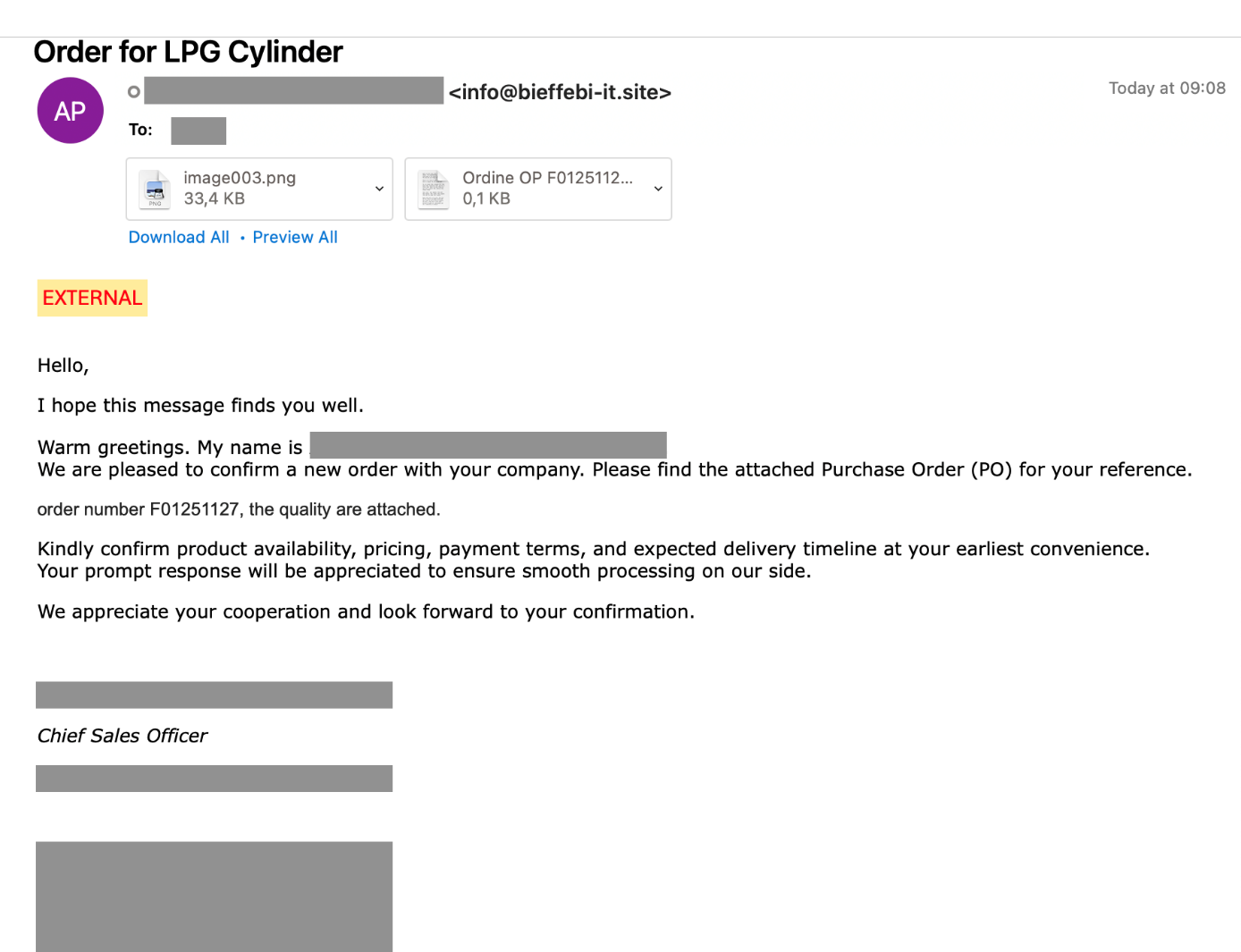
Description: This is a fake order confirmation abusing a stolen identity from real person.
Fake renewal notices
Businesses receive fraudulent notices for renewals such as domain registrations, business licenses, or software subscriptions. These notices often look official and urgent, pushing the victim to pay quickly without verifying authenticity.
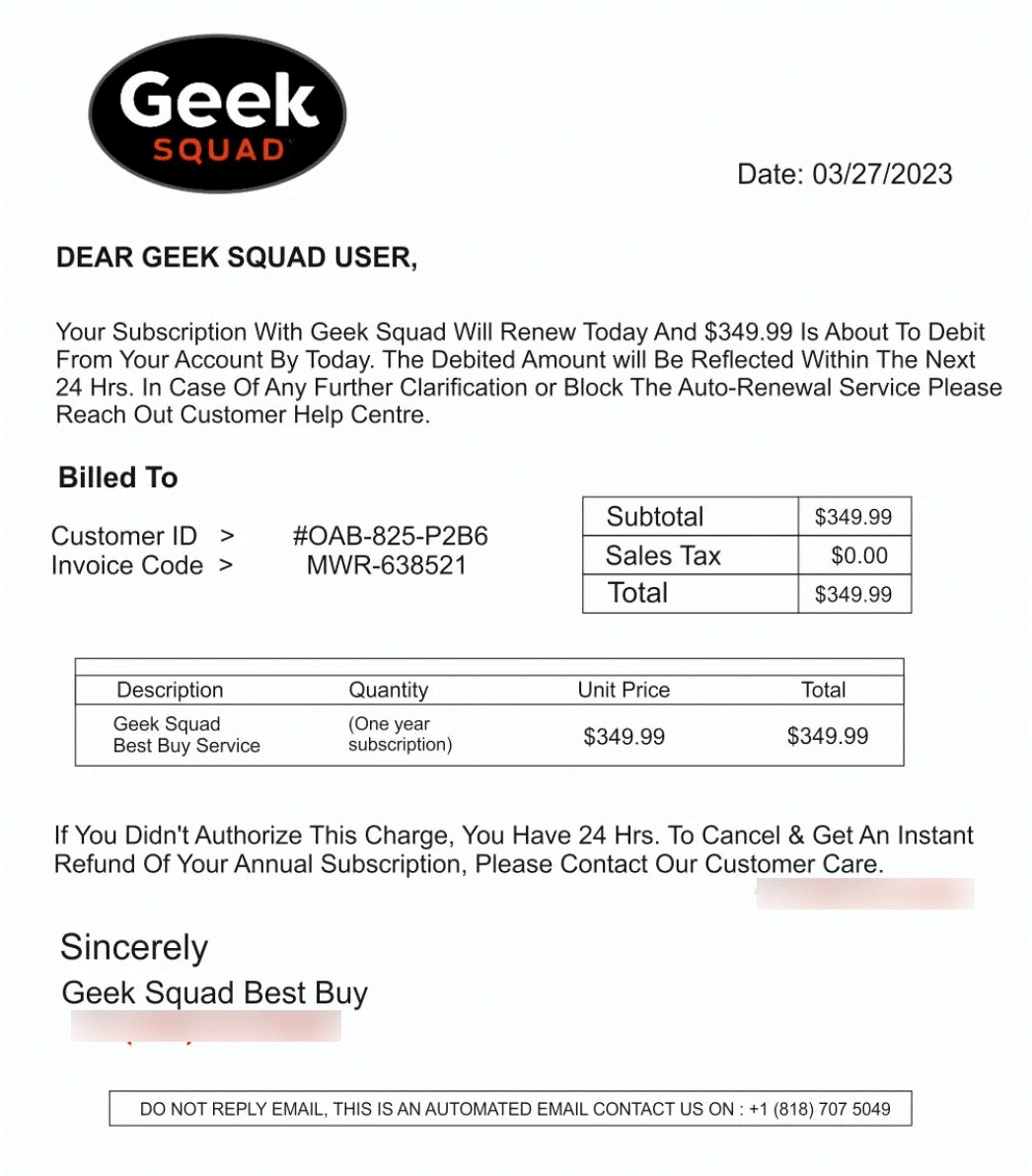
Description: Fake subscription renewal notice impersonating Geek Squad tech support and repair service. (Image source: Reddit)
Government Impersonation
Scammers pose as government officials or agencies, claiming the business owes compliance fees, regulatory charges, or penalties. These scams rely on fear and urgency, making victims believe they must pay immediately to avoid legal trouble.
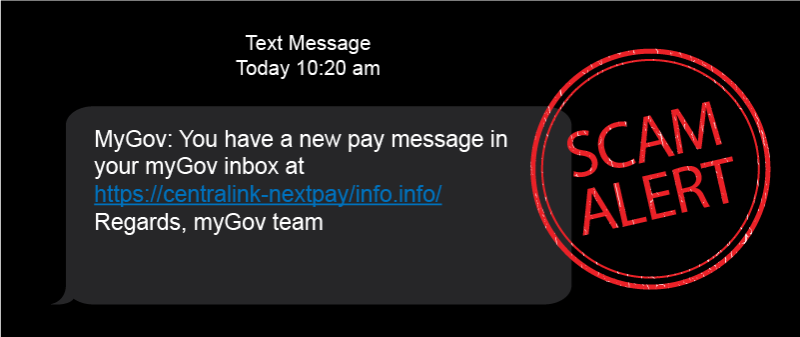
Description: An example of a fraudulent message claiming to be from an Australian government agency.
Legal/law enforcement scams
These scams often target victims of other scams. Cybercriminals pose as law enforcement agents or legal professionals - reaching out via malicious ads, calls, SMS, or chat messages - and offer help for a fee. They may promise to recover lost funds, provide legal advice or consultations, open new cases, or enroll victims in fake class-action lawsuits. Scammers often impersonate Europol, Interpol, or lawyers from fictitious firms to appear legitimate.
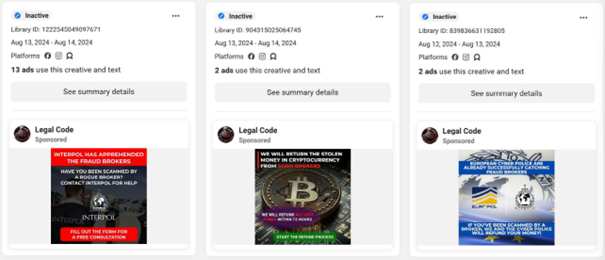
Description: Examples of fraudulent ads as listed in the Meta Ad Library. These now-inactive ads were detected by ESET as HTML/Nomani and are described in detail in the ESET H2 2024 Threat Report.
Fake loan offers
In this scam, fraudsters promise quick business loans, but require an “insurance” or “processing” fee up front. Once the fee is paid, the scammers disappear, leaving the victim without the promised funds.
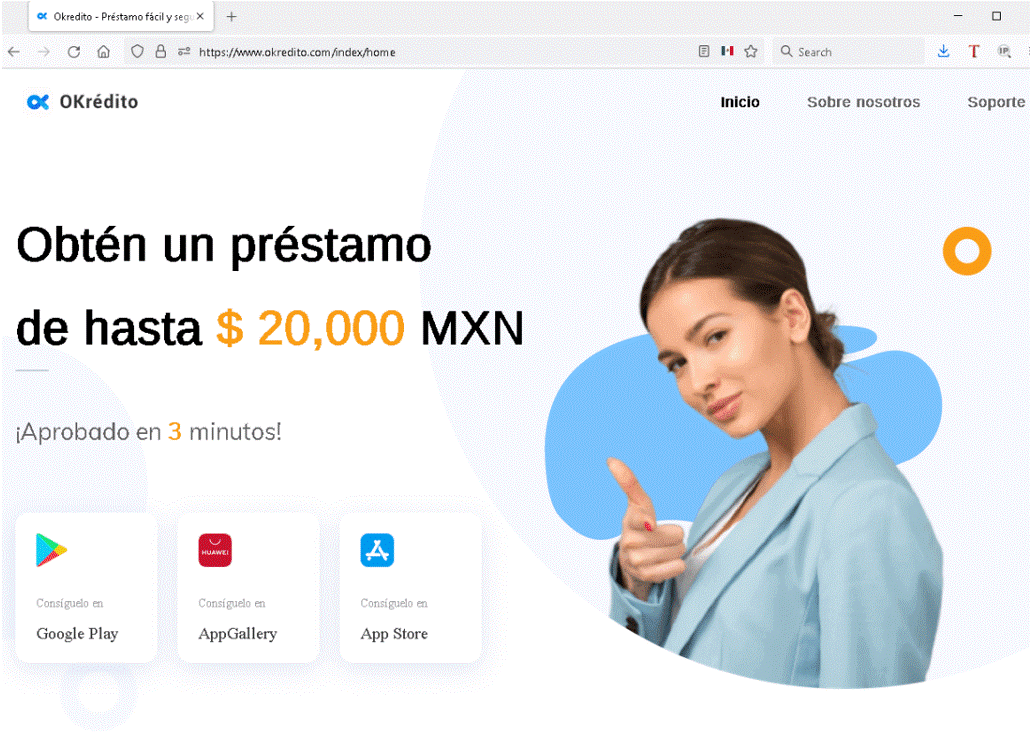
Description: A scam website offering a personal loan app. Despite their attractive appearance, these services are, in fact, designed to defraud users by offering them high-interest-rate loans endorsed with deceitful descriptions, all while collecting their victims’ personal and financial information to blackmail, and, in the end, get their hands on their funds.
Tech support scam
Scammers pretend to be tech support members of trusted companies, claiming your device has an issue. To “help,” they request remote access - but they do anything but help. Here, scammers try to steal sensitive data, attempt to install malware, or carry out other cyberattacks. They may also demand payment for these fake services.
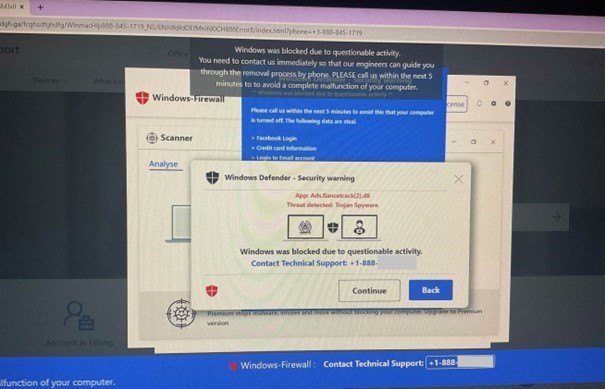
Description: A fake security alert manipulating the targeted user to call “technical support.
A real-life story: A bank imposter got into an account
In 2024, a southern Maine art studio owner told WGME-TV her story about scammers posing as a bank, alerting her to suspicious charges on her account. They offered help, suggesting that she screen-share her phone to execute a wire transfer to “protect” her funds—a Small Business Administration disaster loan provided after her studio was damaged during a storm. With this access, attackers simply transferred thousands of dollars out of the account. According to the Federal Trade Commission, more than 1,300 such scams were reported in Maine H1 2024, resulting in millions of dollars in losses.
Delivery scams
These scams involve fake messages about package delivery issues. Victims are tricked into sharing personal information, installing malicious apps, or paying bogus fees to “resolve” the problem.
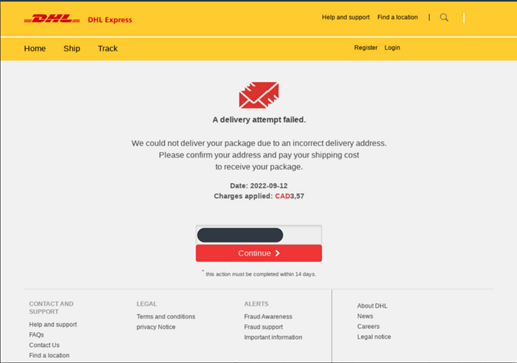
Description: Delivery scam email reported by ESET telemetry. It claims that the delivery attempt has failed and requests shipping address verification.
Expert insights
“AI made everything faster. ESET telemetry shows that a majority of cyberattacks against businesses begin with phishing emails. Traditionally, phishing tricks people into revealing personal data or downloading malware. Spearphishing goes further, utilizing personalized messages after attackers gather details about a specific target. Today, AI automates this process, making spearphishing increasingly common.
For example, you might publish a post about attending a conference on social media, and the next day, you could receive a fraudulent email from a person claiming to have met you there, offering photos and wanting to connect with you. For a person lacking awareness, it is easy to get hooked and click on a malicious link.”
- Július Selecký, ESET Solution Architect
A quick guide to avoiding scams
These tips can easily and measurably improve your cybersecurity posture without overburdening your budget:
Educate yourself about scams: Stay aware of new threats, and watch for warning signs such as suspicious links or attachments, unusual payment requests, urgent or threatening language, or requests for sensitive information. ESET’s free, easy-to-use link checker can help you avoid dangerous URLs.
Provide cybersecurity awareness training for your employees: You can start with the free version of ESET Cybersecurity Awareness Training.
Enable Multi-Factor Authentication (MFA): Wherever possible, add an extra layer of security to your accounts with MFA.
Stay on top of software updates: Cybercriminals use automated tools, tirelessly searching for known vulnerabilities. Don’t make it easy for them, and update your software regularly.
Do regular backups: This helps you recover from a cyberattack and get back to business quickly.
Deploy reliable cybersecurity: Free or low-cost cybersecurity solutions and cybersecurity bundled in other software may look appealing, but they have limitations. Search for SOHO-oriented cybersecurity with anti-scam capabilities. Do not forget to cover all your devices—PCs, phones, tablets, and servers.
What to do if you’re targeted
If you find yourself in the middle of an ongoing scam, don’t panic. There’s still hope to get out (relatively) unscathed. Here are some immediate steps to take if you suspect a scam:
- Do not provide any further information to the suspected attackers.
- Disconnect all the affected systems from the network and run a malware scan.
- Check your accounts for unusual activity and replace every password.
- Report the incident to the authorities or relevant cybersecurity bodies, such as the FBI’s Internet Crime Complaint Center or the FTC’s Bureau of Consumer Protection.
- Notify the other employees, and if customer data is involved, prepare a clear communication plan. Check your legal obligations for breach notifications.
- Collect and save all documents and electronic communications connected with the scam case. (They may be useful if the offender is arrested and you apply for restitution.)
- Be aware of possible identity theft—scammers may use stolen data for imposter scams.
- Stay vigilant—attackers, armed with more personal data, may try to victimize you again through legal or law enforcement scams.
How ESET protects small businesses
ESET understands that small businesses not only need reliable cybersecurity solutions, but also ones that are affordable and easy to use.
ESET Small Business Security is a formidable AI-powered protection solution capable of blocking scams, safeguarding your transactions, and protecting your business from various kinds of malware, including ransomware. Also, it is very easy to use (no IT staff or deep knowledge of IT is needed), with simple deployment and management. This all comes at the cost of a daily pack of noodles, and delivers protection for up to 25 devices—including PCs, phones, tablets, and Windows Servers.
Here are ESET Small Business Security’s key features:
Award-winning, AI-powered antimalware: Intelligent defense system combines real-time threat detection and cloud-based analysis to stop viruses, ransomware, phishing, and emerging threats quickly and reliably.
Anti-scam capabilities: ESET Small Business Security consists of multiple layers of protection complementing each other to stop scam attempts. The multilayered protection includes Safe Banking, Safe Browsing, Browser Privacy & Security, Anti-Phishing, Ransomware Remediation, Safe Server, Webcam Protection & Microphone Monitor, Network Inspector, ESET Folder Guard, Secure Data, VPN, and VPN for Router.
Multiplatform protection: ESET Small Business Security protects both personal and business devices running on multiple platforms, including Windows, MacOS, Android, iOS, and Windows Server. The subscription can be easily shared with employees and family members via management platform ESET HOME.
Performance efficiency: Designed to be lightweight and fast, ESET solution runs seamlessly in the background with minimal impact on system performance. Presentation Mode ensures uninterrupted usage, even during high-demand activities. ESET Endpoint Security is also integrated with AI PCs to boost detection and performance efficiency even further.
ESET has been named a Leader in the IDC MarketScape for Consumer Digital Life Protection (CDLP) and SOHO segments.
We believe that powerful, yet lightweight, technologies paired with a comprehensive AI strategy are among the top ESET strengths.
According to IDC MarketScape: “ESET is a suitable choice for individuals, families, and SOHO users seeking reliable and lightweight digital life protection. Its prevention-first approach is ideal for those who value proactive security measures that do not compromise device performance.”
It’s not a matter of “if,” but of “when”
Amid multiple global crises, inflation, and increasingly tighter regulations, it’s understandable that many entrepreneurs feel they don’t have the necessary mental bandwidth to deal with other problems—such as cyberthreats and scams.
Sadly, the data shows that the question is not “if,” but “when” you’ll encounter a scam while doing business, which means this topic is unavoidable.
Hopefully, this guide has shown you that cybersecurity is achievable, even for small business owners. All it takes is to adopt a prevention-first strategy and choose cybersecurity solutions that are tailor-made for small office/home office environments.
Frequently asked questions
Why is cybersecurity important for self-employed people and micro businesses?
Because cybercriminals actively target small businesses, knowing they often lack dedicated IT staff and enterprise-grade security. Attacks can lead to reputational damage, financial loss, or even bankruptcy.
Does being “too small” protect my business from cyberattacks?
No. Every business has valuable data—such as banking details, licenses, and customer information—that attackers can exploit or sell. Automation and AI allow cybercriminals to launch large-scale campaigns against businesses of all sizes.
How does AI make scams more dangerous?
AI speeds up scam creation, makes phishing messages more convincing, and enables large-scale deployment. It can analyze online activity and craft personalized spearphishing emails automatically.
What is spearphishing, and why is it growing?
Spearphishing uses personalized messages based on long-term information gathering about a specific target. AI can support this process, making spearphishing more common and harder to detect and distinguish from legitimate messages.
How can I protect my business without a big budget?
- Educate yourself and your employees about scams and warning signs.
- Enable Multi-Factor Authentication (MFA) on accounts.
- Keep software updated to prevent exploitation of known vulnerabilities.
- Perform regular backups to recover quickly after an attack.
- Deploy affordable cybersecurity solutions tailored for micro businesses, like ESET Small Business Security.
What are the benefits of ESET Small Business Security?
ESET Small Business Security offers seamless and easy-to-use AI-powered protection for small businesses. Use it to safeguard online transactions, lock and locate devices, block and remediate ransomware, restore affected files, and shield Windows servers. Encrypt sensitive data and avoid phishing scams. Stay secure and anonymous with Anti-Theft, Safe Browsing, and unlimited VPN and VPN for Router. This solution protects both work and personal devices. It is reliable, cost-effective, and light on resources.








