The malware that has been targeting Tesco Bank has several other banks and service providers on its target list, ESET researchers have found. Uncovered by ESET Threat Intelligence services, the Retefe Trojan, active in its current form since at least February, 2016, is capable of redirecting its victims to modified banking pages to harvest logon credentials. In some cases, it has also tried to trick the user into installing a mobile component of the malware (detected by ESET as Android/Spy.Banker.EZ). This mobile component was then used to bypass two-factor authentication.
Detected by ESET as JS/Retefe, this malicious code is usually spread as an email attachment pretending to be an order, an invoice or a similar file. Once executed, it installs several components including an anonymizing service Tor and uses these to configure a proxy for targeted banking sites.
Retefe also adds a fake root certificate disguised as if issued and verified by a well-known certification authority, Comodo. This makes the fraud very difficult to spot from a user’s perspective.
Retefe has been on the radar, of security researchers, in past. Most recently when it targeted UK banking customers earlier this year. Since then it has added the mobile component and extended its list of targets.
Among services targeted by the Retefe Trojan, are large banks in the UK, Switzerland (the most affected country, according to ESET LiveGrid cloud system) and Austria, as well as popular services like Facebook and PayPal.
The full list can be found below.
“The possible connection between the large attack on Tesco Bank, where thousands lost their funds and the Retefe banking trojan is disturbing. We have of course notified all companies targeted by Retefe and have offered assistance in mitigating the threat. Also, we advise users to take steps to protect themselves,” comments ESET security evangelist Peter Stančík.
ESET researchers have determined the indicators of compromise for the Retefe malware and urge users of the below mentioned services to check if their computers are infected. They can do it manually or use ESET’s Retefe Checker website, where they can find a downloadable tool that checks the computer for the mentioned indicators automatically.
Users can check their computers for Retefe by looking for the following indicators of compromise:
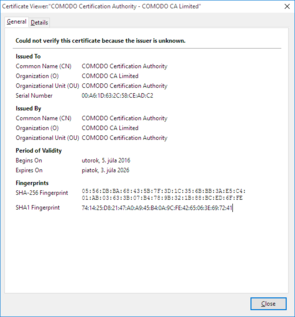
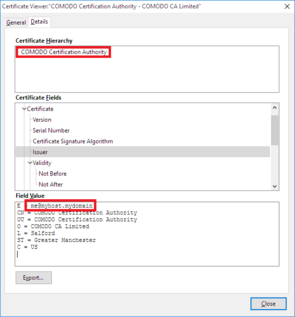
1. Presence of one of the malicious root certificates claiming to be issued by COMODO Certification Authority, with the issuer’s email address set to me@myhost.mydomain:
For Mozilla Firefox, go to the Certificate Manager:
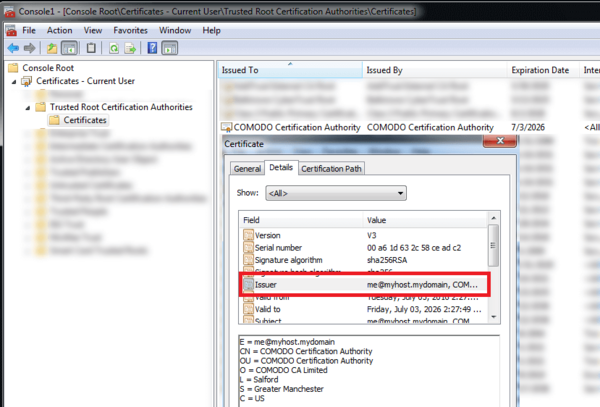
For other browsers, look in the system-wide installed root certificates through MMC (Microsoft Management Console):
So far, we have seen two such certificates with following details:
- Serial number: 00:A6:1D:63:2C:58:CE:AD:C2
- Valid from: Tuesday, July 05, 2016
- Expires: Friday, July 03, 2026
- Issuer: me@myhost.mydomain, COMODO Certification Authority
and
- Serial number: 00:97:65:C4:BF:E0:AB:55:68
- Valid from: Monday, February 15, 2016
- Expires: Thursday, February 12, 2026
- Issuer: me@myhost.mydomain, COMODO Certification Authority
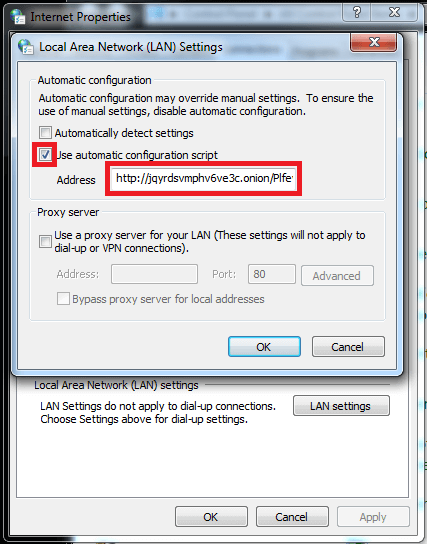
2. Presence of malicious Proxy Automatic Configuration script (PAC) pointing to a .onion domain
-http://%onionDomain%/%random%.js?ip=%publicIP%, where
- %onionDomain% is an onion domain randomly selected from the configuration file
- %random% is a string of 8 characters from alphabet A-Za-z0-9
- %publicIP% is the user’s public IP address
For example: -http://e4loi7gufljhzfo4.onion.link/xvsP2YiD.js?ip=100.10.10.100
3. Presence of Android/Spy.Banker.EZ on your Android device
(can be checked using ESET Mobile Security)
Internet users who discover any of the mentioned indicators of compromise should take the following steps, recommended by ESET security experts:
If you are using any of the services from the list of targets below, change your logon credentials as well as check for suspicious activity (e.g. for fraudulent transactions in your online banking).
1. Remove the Proxy Automatic Configuration script (PAC):
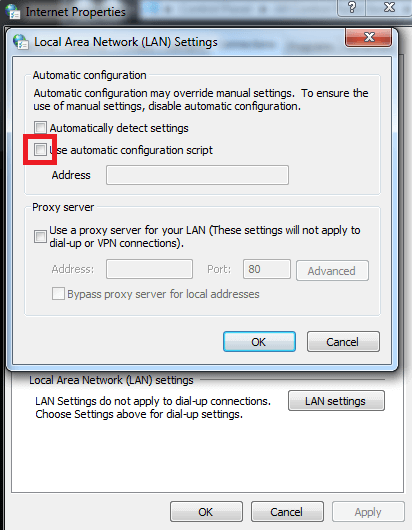
2. Delete the above mentioned certificate.
For proactive protection use reliable security solution with dedicated banking and payment protection. And don’t forget to protect your Android device as well.
Learn more about the Retefe Trojan horse and its connection with the cyberattack on Tesco Bank in a technical article on ESET’s official blog, WeLiveSecurity.com.
List of targets
*.bankaustria.at
*.bawag.com
*.bawagpsk.com
*.bekb.ch
*.bkb.ch
*.clientis.ch
*.credit-suisse.com
*.easybank.at
*.eek.ch
*.gmx.at
*.gmx.ch
*.gmx.com
*.gmx.de
*.gmx.net
*.if.com
*.lukb.ch
*.onba.ch
*.paypal.com
*.raiffeisen.at
*.raiffeisen.ch
*.static-ubs.com
*.ubs.com
*.ukb.ch
*.urkb.ch
*.zkb.ch
*abs.ch
*baloise.ch
*barclays.co.uk
*bcf.ch
*bcj.ch
*bcn.ch
*bcv.ch
*bcvs.ch
*blkb.ch
*business.hsbc.co.uk
*cahoot.com
*cash.ch
*cic.ch
*co-operativebank.co.uk
*glkb.ch
*halifax-online.co.uk
*halifax.co.uk
*juliusbaer.com
*lloydsbank.co.uk
*lloydstsb.com
*natwest.com
*nkb.ch
*nwolb.com
*oberbank.at
*owkb.ch
*postfinance.ch
*rbsdigital.com
*sainsburysbank.co.uk
*santander.co.uk
*shkb.ch
*smile.co.uk
*szkb.ch
*tescobank.com
*ulsterbankanytimebanking.co.uk
*valiant.ch
*wir.ch
*zuercherlandbank.ch
accounts.google.com
clientis.ch
cs.directnet.com
e-banking.gkb.ch
eb.akb.ch
ebanking.raiffeisen.ch
hsbc.co.uk
login.live.com
login.yahoo.com
mail.google.com
netbanking.bcge.ch
onlinebusiness.lloydsbank.co.uk
tb.raiffeisendirect.ch
uko.ukking.co.uk
urkb.ch
wwwsec.ebanking.zugerkb.ch
About ESET
Since 1987, ESET® has been developing award-winning security software that now helps over 100 million users to Enjoy Safer Technology. Its broad security product portfolio covers all popular platforms and provides businesses and consumers around the world with the perfect balance of performance and proactive protection. The company has a global sales network covering more than 200 countries and territories, and regional offices in Bratislava, San Diego, Singapore and Buenos Aires. For more information visit www.eset.com or follow us on LinkedIn, Facebook and Twitter.