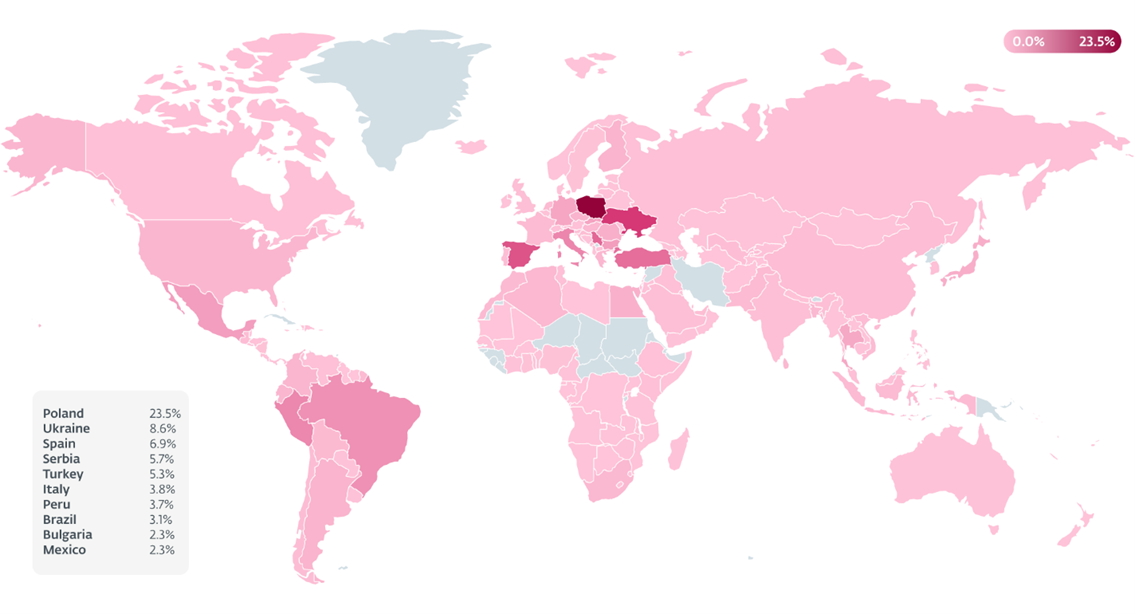
- In the second half of 2023, ESET detected multiple AceCryptor campaigns using the Rescoms remote access tool (RAT) in European countries, mainly Poland, Bulgaria, Slovakia, Spain, and Serbia.
- The threat actor behind these campaigns in some cases abused compromised accounts to send spam emails in order to make them look as credible as possible.
- The goal of the spam campaigns was to obtain credentials stored in browsers or email clients, which in case of a successful compromise would open possibilities for further attacks.
BRATISLAVA — March 20, 2024 — ESET Research has recorded a dramatic increase in AceCryptor attacks, with ESET detections tripling between the first and second halves of 2023, correlating to the protection of 42,000 ESET users worldwide. Furthermore, in recent months, ESET registered a significant change in how AceCryptor is used, namely that the attackers spreading Rescoms (also known as Remcos) started utilizing AceCryptor, which was not the case beforehand. Rescoms is a remote access tool (RAT) that is often used by threat actors for malicious purposes; AceCryptor is a cryptor-as-a-service that obfuscates malware to hinder its detection. Based on the behavior of deployed malware ESET researchers assume that the goal of these campaigns was to obtain email and browser credentials for further attacks against the targeted companies. The vast majority of AceCryptor-packed Rescoms RAT samples were used as an initial compromise vector in multiple spam campaigns targeting European countries, including Central Europe (Poland, Slovakia), the Balkans (Bulgaria, Serbia), and Spain.
“In these campaigns, AceCryptor was used to target multiple European countries, and to extract information or gain initial access to multiple companies. Malware in these attacks was distributed in spam emails, which were in some cases quite convincing; sometimes the spam was even sent from legitimate, but abused, email accounts,” says ESET researcher Jakub Kaloč, who discovered the latest AceCryptor with Rescoms campaign. “Because opening attachments from such emails can have severe consequences for you or your company, we advise you to be aware about what you are opening and use reliable endpoint security software able to detect this malware,” he adds.
In the first half of 2023, the countries most affected by malware packed by AceCryptor were Peru, Mexico, Egypt, and Türkiye, with Peru, at 4,700, having the greatest number of attacks. Rescoms spam campaigns changed these statistics dramatically in the second half of the year. AceCryptor-packed malware affected mostly European countries.
AceCryptor samples that we’ve observed in the second half of 2023 often contained two malware families as their payload: Rescoms and SmokeLoader. A spike detected in Ukraine was caused by SmokeLoader. On the other hand, in Poland, Slovakia, Bulgaria, and Serbia, increased activity was caused by AceCryptor containing Rescoms as a final payload.
All spam campaigns that targeted businesses in Poland had emails with very similar subject lines about B2B offers for the victim companies. To look as believable as possible, attackers did their research and used existing Polish company names and even existing employee/owner names and contact information when signing those emails. This was done so that in the case of a victim Googling the sender’s name, the search would be successful, which might lead to the victim opening the malicious attachment.
While it is unknown whether the credentials were gathered for the group that carried out these attacks or if those stolen credentials would be later sold on to other threat actors, it is certain that successful compromise opens the possibility for further attacks, especially for ransomware attacks.
In parallel with the campaigns in Poland, ESET telemetry also registered ongoing campaigns in Slovakia, Bulgaria, and Serbia. The only significant difference, of course, was that the language used in the spam emails was localized for those specific countries. Apart from the previously mentioned campaigns, Spain also experienced a surge of spam emails with Rescoms as the final payload.
For more technical information about the AceCryptor and Rescoms RAT campaign, check out the blogpost “Rescoms rides waves of AceCryptor spam”. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Heatmap of countries affected by AceCryptor, according to ESET telemetry
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X (Twitter).