This cyberespionage campaign dates back to at least August 2021 and is still ongoing as of March 2022.
Mustang Panda, the APT group behind this campaign, is targeting mainly governments and NGOs. Most victims are located in East and Southeast Asia, but a few are in Europe (Greece, Cyprus, Russia) and Africa (South Africa, South Sudan).
Known victims include research entities, internet service providers, and European diplomatic missions.
The compromise chain includes decoy documents that are frequently updated and relate to events in Europe and the war in Ukraine.
The campaign uses a custom loader to execute Hodur, a new Korplug variant.
Every stage of the deployment process utilizes anti-analysis techniques and control-flow obfuscation, which sets it apart from other campaigns.
BRATISLAVA, MONTREAL —MARCH 23, 2022 — ESET Research discovered a still-ongoing cyberespionage campaign using a previously undocumented Korplug variant by the Mustang Panda APT group. The current campaign exploits the war in Ukraine and other European news topics. Known victims include research entities, internet service providers (ISPs), and European diplomatic missions mostly located in East and Southeast Asia. ESET researchers named this new Korplug variant Hodur due to its resemblance to the THOR variant documented in 2020. In Norse mythology, Hodur is Thor’s blind half-brother.
Victims of this campaign are likely lured with phishing documents abusing the latest events in Europe such as Russia’s invasion of Ukraine. This has resulted in more than three million residents fleeing the war to neighboring countries according to the UNHCR, leading to an unprecedented crisis on Ukraine’s borders. One of the filenames related to this campaign is “Situation at the EU borders with Ukraine.exe”.
Other phishing lures mention updated COVID-19 travel restrictions, an approved regional aid map for Greece, and a Regulation of the European Parliament and of the Council. The final lure is a real document available on the European Council’s website. This shows that the APT group behind this campaign is following current affairs and is able to successfully and swiftly react to them.
“Based on code similarities and the many commonalities in Tactics, Techniques, and Procedures, ESET researchers attribute this campaign with high confidence to Mustang Panda, also known as TA416, RedDelta, or PKPLUG. It is a cyberespionage group mainly targeting governmental entities and NGOs,” explains ESET malware researcher Alexandre Côté Cyr who discovered Hodur. Victims of Mustang Panda are mostly, but not exclusively, located in East and Southeast Asia with a focus on Mongolia. The group is also known for its campaign targeting the Vatican in 2020.
While ESET researchers haven’t been able to identify the verticals of all victims, this campaign seems to have the same targeting objectives as other Mustang Panda campaigns. Following the APT’s typical victimology, most victims are located in East and Southeast Asia, along with some in European and African countries. According to ESET telemetry the vast majority of targets are located in Mongolia and Vietnam, followed by Myanmar, with only a few in other affected countries, namely Greece, Cyprus, Russia, South Sudan, and South Africa. Identified verticals include diplomatic missions, research entities, and ISPs.
Mustang Panda’s campaigns frequently use custom loaders for shared malware including Cobalt Strike, Poison Ivy, and Korplug (also known as PlugX). The group has also been known to create its own Korplug variants. “Compared to other campaigns using Korplug, every stage of the deployment process utilizes anti-analysis techniques and control-flow obfuscation, to make the investigation more difficult for us malware researchers,” concludes Côté Cyr.
For detailed technical analysis, read the blogpost "Mustang Panda’s Hodur: Old tricks, new Korplug variant" on WeLiveSecurity and follow ESET Research on Twitter for the latest news from ESET Research.
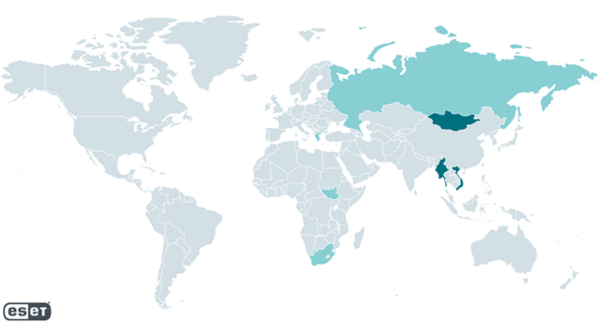
Most victims affected by Mustang Panda in this campaign are in East and Southeast Asia

One of the decoy documents used in this campaign: a real document from the European Council’s website
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.