- TA410 is an umbrella group comprised of three teams ESET researchers named FlowingFrog, LookingFrog and JollyFrog, each with its own toolset and targets.
- ESET telemetry shows victims all around the world, mainly in the governmental and education sectors.
- TA410 had access to the most recent known Microsoft Exchange remote code execution vulnerabilities, (e.g., ProxyLogon in March 2021 and ProxyShell in August 2021).
- ESET researchers found a new version of FlowCloud, a complex and modular C++ RAT used by FlowingFrog with several interesting capabilities, including:
- Controlling connected microphones and triggering recording when sound levels above a specified threshold volume are detected.
- Monitoring clipboard events to steal clipboard content.
- Monitoring file system events to collect new and modified files.
- Controlling attached camera devices to take pictures of the compromised computer’s surroundings.
BRATISLAVA, MONTREAL — APRIL 27, 2022 — ESET Research reveals a detailed profile of TA410, a cyberespionage umbrella group loosely linked to APT10, known mostly for targeting US-based organizations in the utilities sector, and diplomatic organizations in the Middle East and Africa. ESET researchers believe this group consists of three different teams using different toolsets, including a new version of FlowCloud discovered by ESET. It is a very complex backdoor with interesting espionage capabilities. ESET will present its latest findings about TA410, including results from ongoing research, during Botconf 2022.
These teams, referred to as FlowingFrog, LookingFrog, and JollyFrog, have overlaps in TTPs, victimology and network infrastructure. ESET researchers also assume that these subgroups operate somewhat independently, but that they may share intelligence requirements, an access team that runs their spearphishing campaigns, and also the team that deploys network infrastructure.
Most TA410 targets are high-profile organizations in the diplomacy and education sectors, but ESET has also identified victims in the military sector, a manufacturing company in Japan, a mining company in India, and a charity in Israel. An element worth mentioning is that TA410 targets foreign individuals in China. According to ESET telemetry, this happened at least twice; for instance, one victim is a French academic, and another is a member of a diplomatic mission of a South Asian country in China.
Since 2018, ESET has seen various targets of TA410, as depicted on the map.
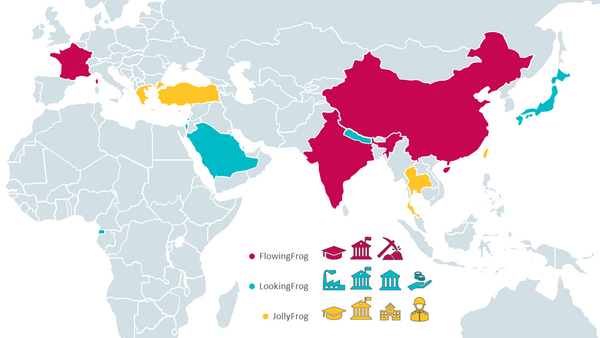
Map of countries and verticals targeted by TA410
Initial access to targets is obtained by exploiting vulnerable internet-facing applications such as Microsoft Exchange, or by sending spearphishing emails with malicious documents. “This indicates to us that their victims are targeted specifically, with the attackers choosing which entry method has the best chance of infiltrating the target,” explains ESET malware researcher Alexandre Côté Cyr. Even though ESET researchers believe that this version of FlowCloud, used by the FlowingFrog team, is still undergoing development and testing, the cyberespionage capabilities of this version include the ability to collect mouse movements, keyboard activity, and clipboard content, along with information about the current foreground window. This information can help attackers understand stolen data by contextualizing it.
FlowCloud can also gather information about things happening around the victim’s computer by taking pictures using connected camera peripherals and recording audio using a computer’s microphone. “This latter function is triggered automatically by any sound over a threshold of 65 decibels, which is in the upper range of normal conversation volume. Typical sound recording functions in cyberespionage malware are triggered either when an action on the affected machine is performed – for instance, when a videoconference app is run – or when a specific command is sent to the malware by its operators,” clarifies Côté Cyr.
TA410 has been active since at least 2018, and was first publicly revealed in August 2019 by Proofpoint in its LookBack blogpost. A year later, the then-new and very complex malware family called FlowCloud was also attributed to TA410.
For detailed technical analysis, read the blogpost "A lookback under the TA410 umbrella: Its cyberespionage TTPs and activity" on WeLiveSecurity, and follow ESET Research on Twitter for the latest news from ESET Research. For YARA and Snort rules, consult ESET's GitHub account.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.