- ESET researchers discovered a malware campaign that targets Chinese-speaking people in Southeast and East Asia.
- The attackers purchased advertisements to position their malicious websites in the "sponsored" section of Google search results. ESET reported these ads to Google and they were promptly removed.
- The websites and installers downloaded from them are mostly in Chinese and, in some cases, falsely offer Chinese-language versions of software that is not available in China.
- We observed victims mostly in Southeast and East Asia, suggesting that the advertisements were targeting that region.
- The malware delivered by this campaign is FatalRAT, a remote access Trojan that provides a set of functionalities to perform various malicious activities on a victim’s computer.
BRATISLAVA, MONTREAL — February 16, 2023 — ESET researchers discovered a malware campaign that targets Chinese-speaking people in Southeast and East Asia by buying misleading advertisements to appear in Google search results that lead to downloading Trojanized installers. The unknown attackers created fake websites that look identical to those of popular applications such as Firefox, WhatsApp, Signal, Skype, and Telegram, but in addition to providing the legitimate software, also deliver FatalRAT, a remote access Trojan that grants the attacker control of the victimized computer. The attacks affected users mostly in mainland China, Hong Kong, and Taiwan, but also in Southeast Asia and Japan.
FatalRAT provides a set of functionalities to perform various malicious activities on a victim’s computer. Among other capabilities, the malware can capture keystrokes, steal or delete data stored by some browsers, and download and execute files. ESET Research observed these attacks between August 2022 and January 2023, but according to our telemetry, previous versions of the installers have been used since at least May 2022.
The attackers registered various domain names that all pointed to the same IP address: a server hosting multiple websites that download Trojanized software. Most of these websites look identical to their legitimate counterparts but deliver malicious installers instead. The other websites, possibly translated by the attackers, offer Chinese-language versions of software that is not available in China, such as Telegram. While, in theory, there are many possible ways that potential victims can be directed to these fake websites, a Chinese-language news site reported that they were being shown an advertisement that led to one of these malicious websites when searching for the Firefox browser in Google. The attackers purchased advertisements to position their malicious websites in the "sponsored" section of Google search results; we reported these ads to Google and they were promptly removed.
“Although we couldn’t reproduce such search results, we believe that the ads were only served to users in the targeted region,” explains Matías Porolli, the ESET researcher who discovered the campaign. “Since many of the domain names that the attackers registered for their websites are very similar to the legitimate domains, it is also possible that the attackers rely on URL hijacking to attract potential victims to their websites,” he adds.
“It is possible that the attackers are solely interested in the theft of information like web credentials to sell them on underground forums, or to use them for another type of crimeware campaign, but for now, specific attribution of this campaign to a known or new threat actor is not possible,” elaborates Porolli. “Finally, it is important to check the URL that we are visiting before we download software. Even better, type it into your browser’s address bar after checking that it is the actual vendor site,” advises Porolli.
For more technical information about this malware campaign, check out the blogpost “These aren’t the apps you’re looking for: Fake installers targeting Southeast and East Asia” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
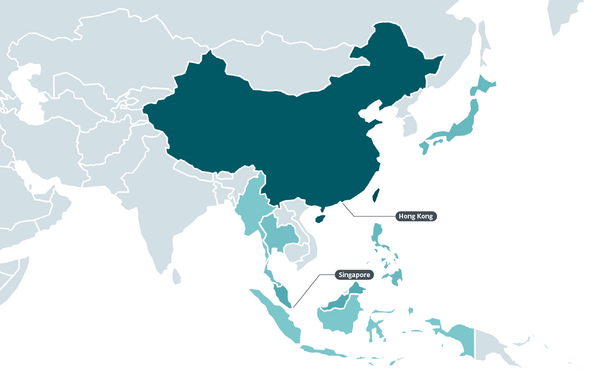
Countries where ESET detected the attacks between August 2022 and January 2023
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure, and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.