ESET researchers discovered and analyzed an ongoing malicious campaign distributing a backdoor via torrents, using Korean TV content and sometimes games as bait. The backdoor is spread via South Korean and Chinese torrent sites. The malware allows the attacker to connect the compromised computer to a botnet and control it remotely.
The malware concerned is a modified version of a publicly available backdoor named GoBot2; the modifications to the source code are mainly South Korea-specific evasion techniques. Due to the campaign’s clear focus on South Korea, ESET has dubbed this Win64/GoBot2 variant GoBotKR. With 80% of all detections, South Korea is the most affected, followed by China (10%) and Taiwan (5%). According to ESET telemetry, GoBotKR has been active since 2018.
“The attackers behind this campaign try to trick users into executing the malware by booby-trapping the contents of the torrents with malicious files that have deceptive filenames, extensions and icons,” says ESET Researcher Zuzana Hromcova, who analyzed the malware. “Directly opening the intended MP4 file will not result in any malicious action. The catch here is that the MP4 file is often hidden in a different directory, and users might first encounter the malicious file mimicking it.”
According to ESET, the malware is not particularly complex technically. However, the actors behind GoBotKR are building a network of bots that can then be used to perform DDoS attacks of various kinds. Therefore, after being executed, GoBotKR first collects system information about the compromised computer, including network configuration, OS version information, and CPU and GPU versions. In particular, it collects a list of installed antivirus software.
“This information is sent to a C&C server, which helps the attackers determine which bots should be used in the respective attacks. All C&C servers that we extracted from the analyzed malware samples are hosted in South Korea and registered by the same person,” elaborates Hromcova on her investigation.
The bot has many capabilities, such as allowing misuse of the compromised computer; allowing botnet operators to control, or further extend, the botnet; and evading detection and hiding from the user. Among other supported commands is the possibility of directing a DDoS attack on specified victims; copying the malware to connected removable media or to public folders of cloud storage services (Dropbox, OneDrive, Google Drive); and seeding torrents with the malicious file as a means to further extend the botnet.
From a research perspective, GoBotKR is especially interesting for its evasion techniques, which were expanded to target South Korea. In particular, the malware scans running processes on the compromised system to detect selected antivirus products, including products of a South Korean security company. If any of the products are detected, it terminates itself. Another evasion technique detects analytical tools running on the system, again referencing the same South Korean security company. In the third evasion technique, attackers misuse legitimate South Korean online platforms to determine the IP address of the victim. “Overall, the modifications show us that the attackers customized the malware for a specific audience, while taking extra effort to remain undetected in their campaign” concludes Hromcova.
For more details on GoBotKR and its capabilities, read the ESET blogpost “Malicious campaign targets South Korean users with backdoor-laced torrents,” published on WeLiveSecurity.com.
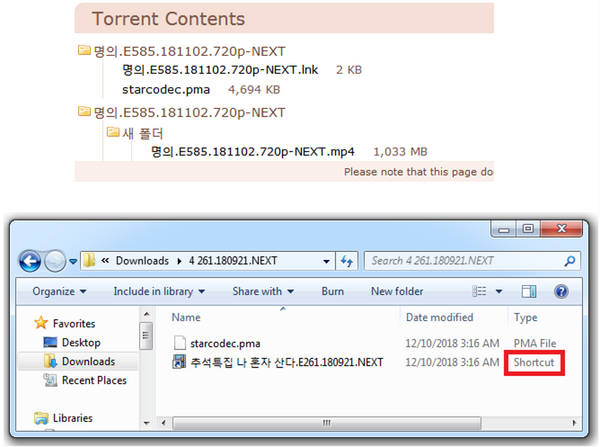
Figure 1. Contents of some torrents delivering the malware (the MP4 video is not displayed on the second screenshot); the malware is executed by a LNK file with a deceptive filename and icon
______________________________________________________________________________________________
About ESET
For 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give consumers and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D centers worldwide, ESET has become the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003. For more information, visit www.eset.com or follow us on LinkedIn, Facebook and Twitter.