- Focused only on Israeli targets, POLONIUM attacked more than a dozen organizations in various verticals, such as engineering, information technology, law, communications, branding and marketing, media, insurance, and social services.
- Microsoft assesses that POLONIUM is an operational group based in Lebanon that coordinates its activities with other actors affiliated with Iran's Ministry of Intelligence and Security.
- According to ESET telemetry, the group has used at least seven different custom backdoors since September 2021, with its most recent actions observed as recently as September 2022. ESET named the five previously undocumented backdoors with the suffix “-Creep.”
- The group has developed custom tools for taking screenshots, logging keystrokes, spying via the webcam, opening reverse shells, exfiltrating files, and more.
- For command and control communication, POLONIUM abuses common cloud services such as Dropbox, OneDrive, and Mega.
BRATISLAVA, MONTREAL — OCTOBER 10, 2022 — ESET researchers recently analyzed previously undocumented custom backdoors and cyberespionage tools deployed in Israel by the POLONIUM APT group. ESET named the five previously undocumented backdoors with the suffix “-Creep.” According to ESET telemetry, POLONIUM has targeted more than a dozen organizations in Israel since at least September 2021, with the group’s most recent actions being observed in September 2022. The verticals targeted by this group include engineering, information technology, law, communications, branding and marketing, media, insurance, and social services. POLONIUM is a cyberespionage group first documented by Microsoft in June 2022. According to Microsoft, the group is based in Lebanon and coordinates its activities with other actors affiliated with Iran’s Ministry of Intelligence and Security.
According to ESET Research, POLONIUM is a very active threat actor with a vast arsenal of malware tools and is constantly modifying them and developing new ones. A common characteristic of several of the group’s tools is the abuse of cloud services such as Dropbox, Mega, and OneDrive for command and control (C&C) communications. Intelligence and public reports about POLONIUM are very scarce and limited, likely because the group’s attacks are highly targeted, and the initial compromise vector is not known.
“The numerous versions and changes POLONIUM introduced into its custom tools show a continuous and long-term effort to spy on the group’s targets. ESET can infer from their toolset that they are interested in collecting confidential data from their targets. The group doesn’t seem to engage in any sabotage or ransomware actions,” says ESET researcher Matías Porolli, who analyzed the malware.
POLONIUM’s toolset consists of seven custom backdoors: CreepyDrive, which abuses OneDrive and Dropbox cloud services for C&C; CreepySnail, which executes commands received from the attackers’ own infrastructure; DeepCreep and MegaCreep, which make use of Dropbox and Mega file storage services, respectively; and FlipCreep, TechnoCreep, and PapaCreep, which receive commands from attackers’ servers. The group has also developed several custom modules to spy on its targets by taking screenshots, logging keystrokes, spying via the webcam, opening reverse shells, exfiltrating files, and more.
“Most of the group’s malicious modules are small, with limited functionality. In one case the attackers used one module for taking screenshots and another for uploading them to the C&C server. On a similar note, they like to divide the code in their backdoors, distributing malicious functionality into various small DLLs, perhaps expecting that defenders or researchers will not observe the complete attack chain,” explains Porolli.
For more technical information about POLONIUM, check out the blogpost “Polonium targets Israel with Creepy malware” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
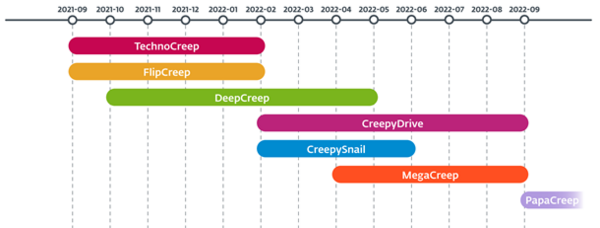
Timeline of observed backdoors deployed by POLONIUM