- ESET Research discovered a sophisticated backdoor, Deadglyph, that has unusual architecture.
- ESET attributes the malware to the Stealth Falcon group, which, according to MITRE, is linked to the United Arab Emirates (UAE).
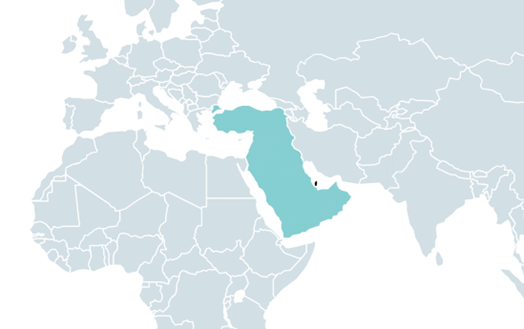
- The victim is a governmental entity in the Middle East that was compromised for espionage purposes. A related sample found on VirusTotal was also uploaded to the file-scanning platform from this region, specifically from Qatar.
- Traditional backdoor commands are implemented via additional modules received from its Command and Control (C&C) server.
- ESET has obtained three out of many modules: process creator, file reader, and info collector.
BRATISLAVA — September 22, 2023 — ESET researchers have discovered and analyzed a sophisticated backdoor, used by the Stealth Falcon group, that has been named Deadglyph by ESET. According to the US not-for-profit security organization MITRE, the group is linked to the United Arab Emirates. Deadglyph has an unusual architecture, and its backdoor capabilities are provided by its C&C in the form of additional modules. Deadglyph has a range of counter-detection mechanisms and it is capable of uninstalling itself to minimize the likelihood of its detection in certain cases. ESET made the discovery in the midst of routine monitoring of suspicious activities on the systems of high-profile customers, some based in the Middle East region. The victim of the analyzed infiltration is a governmental entity in the Middle East that was compromised for espionage purposes. A related sample found on VirusTotal was uploaded from Qatar.
ESET derived the name from artifacts found in the backdoor, coupled with the presence of a homoglyph attack. A homoglyph is a deceptive string of characters appearing like a reliable string. In the case of this backdoor, it was mimicking Microsoft Corporation in one instance.
This previously undocumented backdoor exhibits a notable degree of sophistication and expertise. The traditional backdoor commands are not implemented in the backdoor binary; instead, they are dynamically received by it from its C&C server in the form of additional modules. This backdoor also features a number of capabilities to avoid being detected, including continuous monitoring of system processes and the implementation of randomized network patterns.
ESET Research has managed to obtain three of these modules, uncovering a fraction of Deadglyph’s full capabilities: process creator, file reader, and info collector. The info collector module collects extensive information about the computer, including details about the operating system, installed software and drivers, processes, services, users, and security software. Additionally, the file reader module is able to read specified files; in one case, the module was used to retrieve the victim’s Outlook data file.
Additionally, ESET Research has found a related shellcode downloader that could potentially be used to install Deadglyph.
Based on the targeting and additional evidence, with high confidence ESET attributes Deadglyph to the Stealth Falcon APT group. Also known as Project Raven or FruityArmor, according to MITRE this threat group is linked to the United Arab Emirates. Active since 2012, Stealth Falcon is known to target political activists, journalists, and dissidents in the Middle East. It was first discovered and described by Citizen Lab, which published an analysis of a campaign of spyware attacks in 2016.
For more technical information about Stealth Falcon and Deadglyph, check out the blogpost “Stealth Falcon preying over Middle Eastern skies with Deadglyph” on WeLiveSecurity. Make sure to follow ESET Research on Twitter (now known as X) for the latest news from ESET Research.
Victimology of Deadglyph; the related sample was uploaded to VirusTotal from Qatar (in darker color)
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure, and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.