ESET Threat Report
H2 2025
A view of the 2025 H2 cyber threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts.

H2 2025
A view of the 2025 H2 cyber threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts.

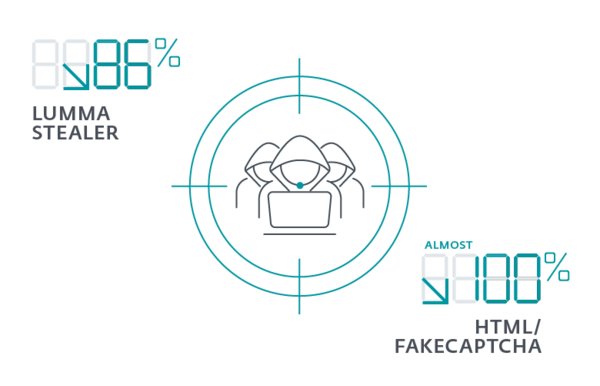
Even though Lumma Stealer managed to come back after the May 2025 disruption, detections of the infostealer plummeted in the second half of the year by 86%, down from over 60,000 detections to fewer than 9,000. While Lumma Stealer is spread in various ways, one of its most prolific vectors was FakeCaptcha sites used in the ClickFix social engineering attacks. The detections of HTML/FakeCaptcha also dropped in H2, going from over 1.6 million detections to less than 60,000.
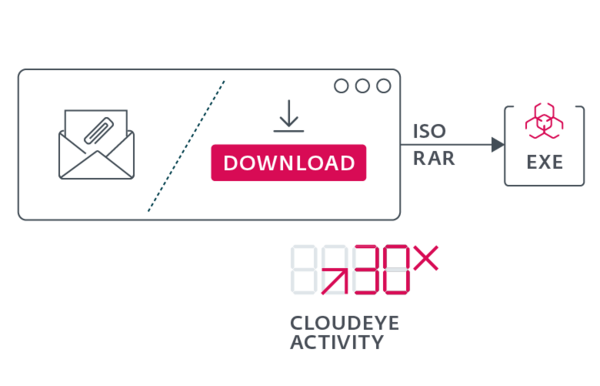
CloudEyE, AKA GuLoader, is a malware-as-a-service downloader and cryptor, used to deploy malware such as ransomware and infostealers. Cryptors are designed to conceal a malicious payload from detection, with the payload compressed and encrypted within the cryptor. Prominent cryptors analyzed by ESET include AceCryptor and ModiLoader. CloudEyE activity surged thirtyfold in H2 to over 100,000 detections.
Leak sites data show that ransomware victim numbers surged in 2025, surpassing the total for 2024 by over 1,700 (as of the end of November). If the trend continues, ESET projects a 40% year-over-year increase in the number of victims. EDR killers proliferate, with Akira, Qilin and Warlock being the top users. ESET discovered HybridPetya, a new ransomware that can compromise modern UEFI-based systems.

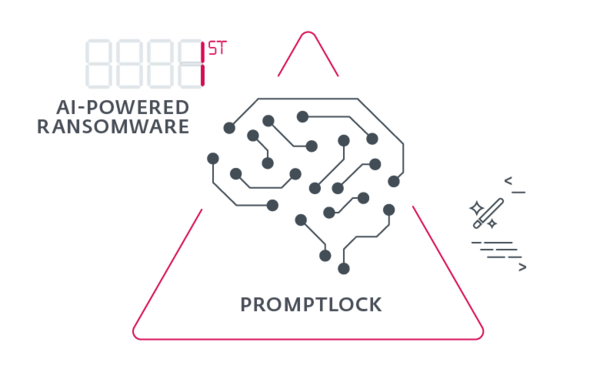
In H2 2025, ESET researchers found PromptLock, the first AI-powered ransomware. The malware can encrypt, exfiltrate or destroy a victim's data. While AI is still mainly fueling higher-quality social engineering, scams and phishing, this discovery signals a new era of threats.
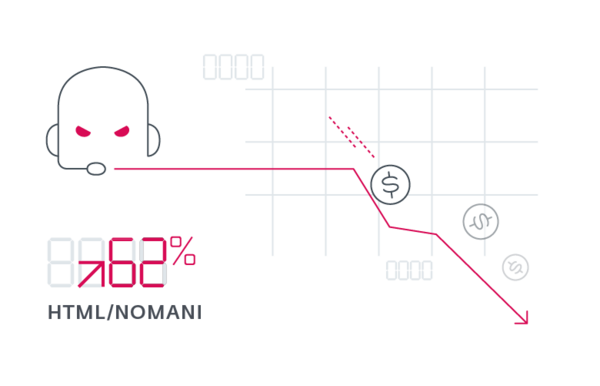
ESET telemetry shows scams detected as HTML/Nomani grew 62% YoY, with a small decrease in H2 2025. Over the year, ESET blocked over 64,000 URLs tied to these scams. Since 2024, ESET has seen several improvements in scams, including higher-quality deepfakes, signs of AI-generated phishing sites and ad campaigns. Nomani scams, which use AI-generated videos, have recently been expanding across multiple platforms.
ESET Threat Reports provide a regular, in-depth overview of the global threat landscape and the main trends and developments shaping it. The statistics and trends presented in the report are based on ESET telemetry data, as interpreted by ESET threat detection and security research and awareness experts. As such, the reports provide unique insights to help defenders navigate the evolving and increasingly complex threat environment.
The ESET Threat Report is released twice yearly, with the H1 issue covering the period from December to May and the H2 issue covering the period from June to November.
ESET Threat Report has a global scope – the core statistics and trends presented in the report are based on global telemetry data from ESET. However, regional developments may be covered in the report’s analyses to provide concrete examples of the discussed trends.
The threat statistics presented in ESET Threat Reports are based on data collected by ESET’s own detection systems across its range of security products – endpoint, cloud and mobile – and their proprietary, layered technologies. Other sources used in the report’s analyses may include honeypots, external security feeds as well as data from other cybersecurity vendors.
ESET Threat Reports offer in-depth analyses of latest threat landscape trends, enriched with comments and recommendations by ESET’s diverse team of cybersecurity specialists – many of which are frequent speakers at prestigious industry conferences like RSA, Black Hat and Virus Bulletin, and renowned for their expertise.
With ESET's R&D centers spanning Europe, Asia, and North America, ESET’s analysts provide around-the-clock global coverage, leveraging diverse time zones and locations to address the evolving threat landscape.
Additionally, the reports contain a regular Threat Telemetry section with comprehensive statistics across the monitored threat categories. This data is processed with the honest intention to mitigate bias, in an effort to maximize the value of the information provided. The charts come with calculated differences between the current and previous reporting periods to highlight trend changes.
ESET APT Activity Reports provide an overview of activities of selected advanced persistent threat (APT) groups investigated and analyzed by ESET Research within the reporting period. APT groups are typically highly sophisticated threat actors, often backed by nation states, engaging in targeted cyberattacks and espionage. In contrast, the Threat Reports focus on widespread cyberthreats – so called crimeware – that typically aren’t targeted in nature and can thus affect anyone.