Extended detection & response
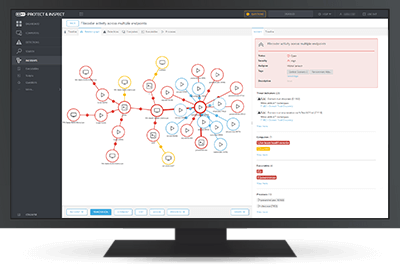
Extended detection and response (XDR) from ESET empowers you to quickly and effectively identify anomalous behavior and breaches, and provides advanced risk assessment, incident response, investigation and remediation capabilities.
ESET Inspect
The XDR-enabling component of the ESET PROTECT platform, delivering breach prevention, enhanced visibility and remediation.
Also available as part of our ESET PROTECT MDR solution.