What is firewall?
The term “firewall” originally referred to a structure that is supposed to confine fire within a closed space, thus hampering its spread and mitigating its harmful effects on humans and property.
By analogy, in network security a firewall is a software- or hardware-based system that works as a gatekeeper between trusted and untrusted networks or its parts. It achieves this by filtering out harmful or potentially unwanted content and communication.
Read more
- Network firewalls usually fulfil this function for internal systems comprising several devices or sub-networks. This type of firewall runs on network hardware and can be easily scaled to fit businesses of any size.
- Host-based firewalls run directly on the user machines (or endpoints) and therefore can offer far more personalized filtering rules.
Most operating systems provide their own built-in host-based firewall. However, these tend to feature only basic functionality and, as widespread as they are, have probably been investigated thoroughly by the potential attackers.
The first commercial firewalls designed for computer networks were developed in the late 1980s by Digital Equipment Corporation (DEC). The technology gained prominence and became widespread over the following decade due to rapid growth of the global internet.
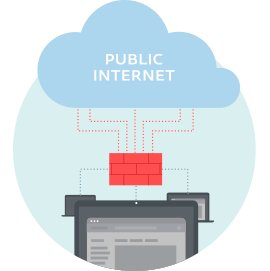
How do firewalls work?
There are multiple types of firewalls, each using a different approach to traffic filtering. First generation firewalls worked as packet filters, comparing basic information such as original source and destination of the packet, the port being used, or the protocol against a predefined list of rules.
Second generation comprised the so-called stateful firewalls, which added another parameter to the filter setup, namely connection state. Based on this information, the technology could determine if the packet was starting the connection, was a part of an existing connection or wasn’t involved at all.

What are the benefits of using a firewall?
The biggest benefit for users is enhanced security. By using a firewall you set up a security perimeter that can help to protect your computer or network from harmful incoming traffic.
This technology can also filter harmful outgoing traffic. By doing this it lowers the chance of undetected data exfiltration by a malicious insider as well as reduces the risk that the devices behind the firewall will become a part of a botnet - a large group of internet-connected devices enslaved by the attackers for malevolent purposes.
Read more
Firewalls are especially beneficial for companies with networks consisting of several internet-connected endpoints. If the firewall is properly set up at the edge of such network, it creates a single point of entry where some of the incoming threats can be identified and mitigated.
It also separates the company’s internal systems from the public internet, and thus creates a protected environment where data can flow more freely and more securely.
ESET offers you a firewall feature
ESET HOME Security Premium
Powerful, multilayered protection to encrypt sensitive data, manage passwords easily, secure online transactions and more. A user-friendly solution for enhanced privacy online. Secures Windows, macOS, Android, and iOS devices.