ESET Resource Center
May 2025
Quick Summary
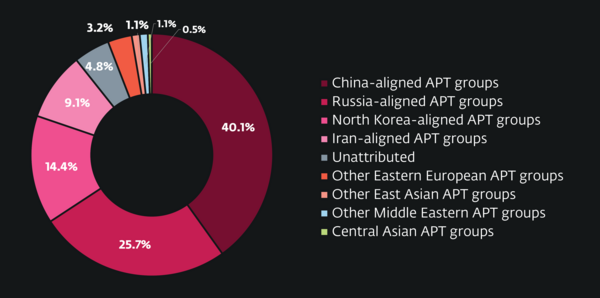
- Russian APT groups intensified attacks against Ukraine and the EU, exploiting zero-day vulnerabilities and deploying wipers.
- China-aligned groups like Mustang Panda and DigitalRecyclers continued their espionage campaigns targeting the EU government and maritime sectors.
- North Korea-aligned groups expanded their financially motivated campaigns using fake job listings and social engineering.
Details
Russia-aligned threat actors, notably Sednit and Gamaredon, maintained aggressive campaigns primarily targeting Ukraine and EU countries. Ukraine was subjected to the greatest intensity of cyberattacks against the country’s critical infrastructure and governmental institutions. The Russia-aligned Sandworm group intensified destructive operations against Ukrainian energy companies, deploying a new wiper named ZEROLOT.
Gamaredon remained the most prolific actor targeting Ukraine, enhancing malware obfuscation and introducing PteroBox, a file stealer leveraging Dropbox. Sednit refined its exploitation of cross-site scripting vulnerabilities in webmail services, expanding Operation RoundPress from Roundcube to include Horde, MDaemon, and Zimbra. ESET discovered that the group successfully leveraged a zero-day vulnerability in MDaemon Email Server (CVE-2024-11182) against Ukrainian companies.
China-aligned APT groups continued their campaigns against governmental and academic institutions. At the same time, North Korea-aligned threat actors significantly increased their operations directed at South Korea, placing particular emphasis on individuals, private companies, embassies, and diplomatic personnel. Mustang Panda remained the most active, targeting governmental institutions and maritime transportation companies via Korplug loaders and malicious USB drives.
Attack Sources
North Korea-aligned threat actors were particularly active in financially motivated campaigns. DeceptiveDevelopment significantly broadened its targeting, using fake job listings primarily within the cryptocurrency, blockchain, and finance sectors. The group employed innovative social engineering techniques to distribute the multiplatform WeaselStore malware. The Bybit cryptocurrency theft, attributed by the FBI to TraderTraitor APT group, involved a supply-chain compromise of Safe{Wallet} that caused losses of approximately USD 1.5 billion.
Iran-aligned APT groups maintained their primary focus on the Middle East region, predominantly targeting governmental organizations and entities within the manufacturing and engineering sectors in Israel. Additionally, ESET observed a significant global uptick in cyberattacks against technology companies, largely attributed to increased activity by North Korea-aligned DeceptiveDevelopment.
“The highlighted operations are representative of the broader threat landscape that we investigated during this period. They illustrate the key trends and developments, and contain only a small fraction of the cybersecurity intelligence data provided to customers of ESET APT reports,” adds Boutin.
ESET products protect our customers’ systems from the malicious activities described in this report. Intelligence shared here is primarily based on proprietary ESET telemetry data and has been verified by ESET researchers, who prepare in-depth technical reports and frequent activity updates detailing activities of specific APT groups.
These threat intelligence analyses, known as ESET APT Reports PREMIUM, assist organizations tasked with protecting citizens, critical national infrastructure, and high-value assets from criminal and nation-state-directed cyberattacks. This report contains only a fraction of the cybersecurity intelligence data provided to customers of ESET’s private APT reports.
Don't miss out
PREMIUM CONTENT
WHITE PAPERS
Navigating Ransomware in 2025: Key Insights & Prevention Strategies
Stay ahead of ransomware threats! Explore the latest trends, prevention strategies, and discover our new tool—ESET Ransomware & Remediation.
PREMIUM CONTENT
WHITE PAPERS
Prevention first: Mastering Cybersecurity with MDR
Discover the critical role of Managed Detection & Response (MDR) in prevention and see how ESET PROTECT MDR can strengthen your security in this Buyer’s Guide.
REPORTS
ESET PROTECT is Top 3 in the G2 Winter 2025 Grid® Report for Extended Detection and Response (XDR) Platforms
Discover why ESET PROTECT earned a top 3 leader position in the G2 Winter 2025 Grid® Report for Extended Detection and Response (XDR) Platforms, based on the latest customer reviews.
Ready for next step?
Enter the world of enterprise protection