Bratislava, Montreal – ESET researchers have discovered a previously unreported cyber espionage framework they dub Ramsay. The framework is tailored for collecting and exfiltrating sensitive documents from air-gapped systems that are not connected to the internet or other online systems. Since the number of victims so far is very low, ESET believes that this framework is under an ongoing development process.
“We initially found an instance of Ramsay in a VirusTotal sample uploaded from Japan that led us to the discovery of further components and other versions of the framework along with substantial evidence to conclude that the framework is still in a developmental stage, with delivery vectors subject to fine testing,” says Alexis Dorais-Joncas, head of ESET’s Montreal-based research team.
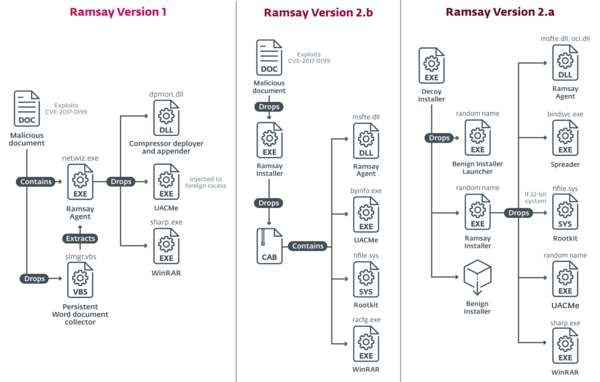
According to ESET findings, Ramsay has gone through several iterations based on the different instances of the framework found, denoting a linear progression on the number and complexity of its capabilities. The developers in charge of infection vectors seem to be trying different approaches, such as using old exploits for Microsoft Word vulnerabilities from 2017 and deploying trojanized applications for delivery, potentially via spear-phishing. The three discovered versions of Ramsay differ in complexity and sophistication, with the latest third version being the most advanced, especially with regard to evasion and persistence.
Ramsay’s architecture provides a series of capabilities managed via a logging mechanism:
- File collection and covert storage: The primary goal of this framework is to collect all existing Microsoft Word documents within a target’s file system.
- Command execution: Ramsay’s control protocol implements a decentralized method of scanning and retrieving commands from control documents.
- Spreading: Ramsay’s embeds a component that seems to be designed to operate within air-gapped networks.
“Especially noteworthy is how the architectural design of Ramsay, especially the relationship between its spreading and control capabilities, allows it to operate in air-gapped networks – meaning networks that are not connected to the internet,” says Dorais-Joncas.
For more technical details about Ramsay, read the blog post Ramsay: A cyber espionage toolkit tailored for air-gapped networks on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give consumers and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D centers worldwide, ESET is the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.