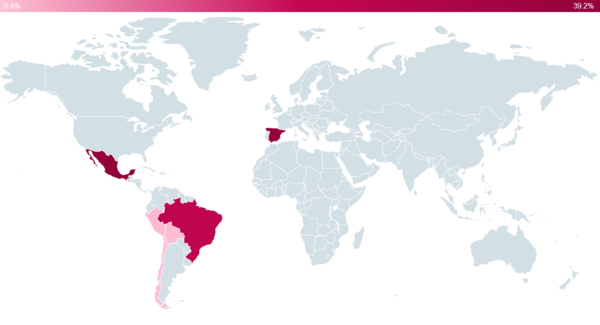
BRATISLAVA, PRAGUE - As part of an ongoing series on Latin American banking trojans, ESET researchers take an in-depth look at Grandoreiro. This trojan targets users especially in Brazil, Mexico, Spain and Peru. Distributed almost exclusively through email spam, it has lately started to utilize fake websites capitalizing on the global coronavirus pandemic. Grandoreiro reveals a persistent effort from its authors to evade detection. Although ESET has seen Grandoreiro primarily distributed through spam, where the authors usually utilize a fake Java or Flash update, recently we have observed a shift to COVID19 related scams. The trojan was hiding in videos on fake websites promising information about the coronavirus. However, instead of playing, clicking the video leads to the download of a payload on visitors’ devices.Grandoreiro has been active since at least 2017 in Brazil and Peru, expanding to Mexico and Spain in 2019. As with other Latin American banking trojans in this series, Grandoreiro attacks its victims by displaying fake pop-up windows as a ploy to get them to divulge sensitive information.
<Image 1. below: Heat map showing ESET's detections of Grandoreiro.>
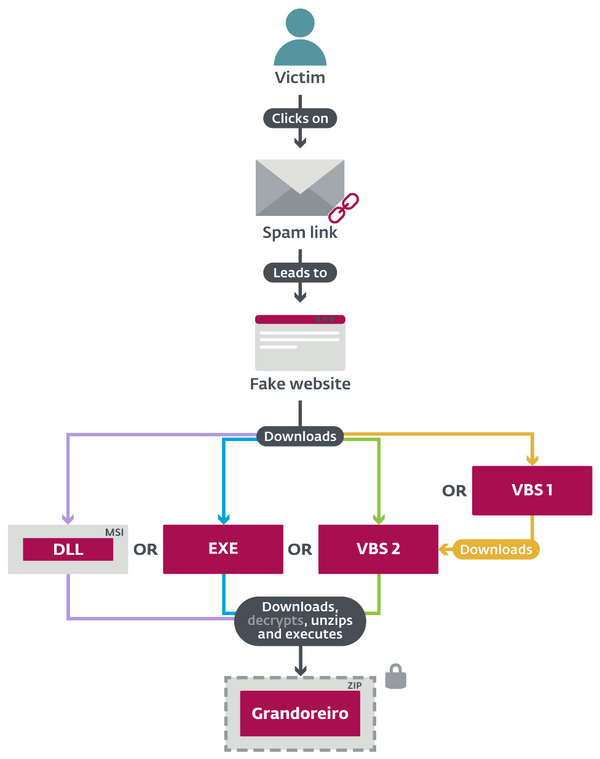
The backdoor functionality of Grandoreiro includes manipulating windows; updating itself; capturing keystrokes; simulating mouse and keyboard actions; navigating browsers to chosen URLs; signing out and restarting machines; and blocking access to websites. Grandoreiro collects various information about affected machines and, in some versions, it also steals credentials stored in Google Chrome as well as data stored in Microsoft Outlook browsers.“For a Latin American banking trojan, Grandoreiro utilizes a surprisingly large number of tricks to evade detection and emulation. That includes many techniques to detect or even disable banking protection software,” says ESET researcher Robert Šuman, leading the team analyzing Grandoreiro. “They seem to be developing the banking trojan very rapidly. Almost every new version we see introduces some changes. We also suspect they are developing at least two variants simultaneously. Interestingly, from a technical point of view, they also utilize a very specific application of the binary padding technique that makes it hard to get rid of the padding while keeping a valid file,” adds Šuman.Unlike the majority of Latin American banking trojans, Grandoreiro utilizes quite small distribution chains. For different campaigns, it may choose a different type of downloader. These downloaders are often stored on well-known public online sharing services such as GitHub, Dropbox, Pastebin, 4shared or 4Sync.
<Image 2 - Possible ways that Grandoreiro distribution chains may appear>
For more technical details about Grandoreiro, read the blogpost “Grandoreiro: How engorged can an EXE get?” on WeLiveSecurity.com. Make sure to follow ESET research on Twitter for the latest news from ESET Research.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services for businesses and consumers worldwide. With solutions ranging from endpoint and mobile security to encryption and two-factor authentication, ESET’s high-performing, easy-to-use products give consumers and businesses the peace of mind to enjoy the full potential of their technology. ESET unobtrusively protects and monitors 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company. Backed by R&D centers worldwide, ESET is the first IT security company to earn 100 Virus Bulletin VB100 awards, identifying every single “in-the-wild” malware without interruption since 2003. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.