The research featured in ESET’s industry report on government works in concert with perspectives from the European Commission, CERN and Europol presented at the ESET European Cybersecurity Day virtual conference on April 28.
BRATISLAVA – The European Union’s cybersecurity strategy, and that of all governments globally, has been challenged not only in its move to “digital by default,” but also by the COVID-19 pandemic, the mass movement to working from home, and threats such as cyberespionage, ransomware and supply-chain attacks. Above all, the most formidable challenge, and foe, shared by all governments is advanced persistent threat (APT) groups.
APT groups leveraging evolved tools
The ESET industry report on government examines the threatscape APT actors are erecting, and underlines its complex nature with an exclusive look at EmissarySoldier, a malicious campaign brought to bear by the LuckyMouse APT group using its SysUpdate toolkit to compromise machines, some of which were running the popular application Microsoft SharePoint.
This dive into LuckyMouse examines its relatively unknown SysUpdate toolkit – the first samples of which were discovered in 2018. Since then, the toolkit has seen various development stages. LuckyMouse’s current modus operandi is to install its implants via a so-called trident model that uses three components: a legitimate application vulnerable to DLL hijacking, a custom DLL that loads the payload and a raw Shikata Ga Nai-encoded binary payload.
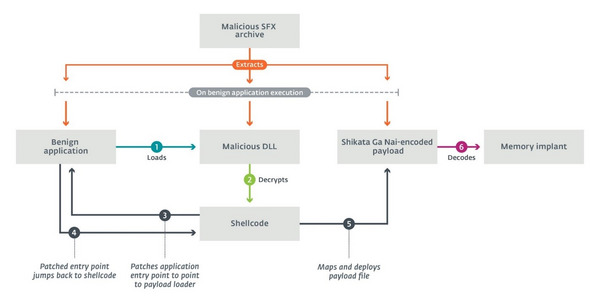
Since SysUpdate's modular architecture enables its operators to limit exposure of malicious artifacts at will, ESET researchers did not retrieve any malicious modules and expect this to be an ongoing challenge in future analyses. Regardless, LuckyMouse increased its activity in 2020, seemingly going through a retooling process where various features were being incrementally integrated into SysUpdate’s toolset.
The evolution of tools leveraged by APT groups like LuckyMouse is of key concern as governments are vested with the responsibility to ensure stability for citizens, the business environment and engagement with other nation-states. These tasks of governance are under threat as LuckyMouse and other APT groups, including state actors and their collaborators, home in on widespread collaboration platforms like Microsoft SharePoint and digital by default service provision.
Government in focus
The years 2020 and 2021 have seen several ESET research collaborations come to maturity, including engagements with the likes of the European Organization for Nuclear Research (CERN, Europol, and the French National Cybersecurity Agency (ANSSI). Many of their perspectives, shared at the virtual event and in the report, stress that governments and their IT infrastructure exist as default targets.
The report highlights the need for technologists to continue supporting governments in closing security gaps and monitoring the tactics, techniques and procedures of APT groups via the various endpoint detection and response technologies at their disposal. To download the report, visit WeLiveSecurity.com and make sure to follow ESET Research on Twitter.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.