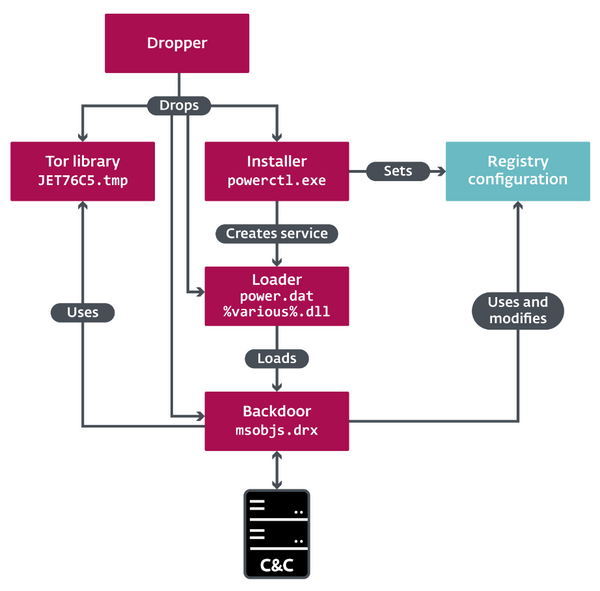
BRATISLAVA – ESET researchers have discovered a previously undocumented backdoor used to attack a freight logistics company in South Africa, which they have dubbed Vyveva. They have attributed the malware to the infamous Lazarus group due to shared similarities with the group’s previous operations and samples. The backdoor includes several cyberespionage capabilities, such as file exfiltration and gathering information about the targeted computer and its drives. It communicates with its Command & Control (C&C) server via the Tor anonymity network.
ESET telemetry for Vyveva suggests targeted deployment as ESET researchers have found only two victim machines, both of which are servers owned by the aforementioned South African logistics company. According to the ESET investigation, Vyveva has been in use since at least December 2018.
“Vyveva shares multiple code similarities with older Lazarus samples that are detected by ESET technology. However, the similarities do not end there: the use of a fake TLS protocol in network communication, command line execution chains, and the methods of using encryption and Tor services all point toward Lazarus. Hence, we can attribute Vyveva to this APT group with high confidence,” says ESET researcher Filip Jurčacko, who analyzed the discovered Lazarus arsenal.
The backdoor executes commands issued by the threat actors, like file and process operations and information gathering. There is also a less commonly seen command for file timestomping, which allows copying timestamps from a “donor” file to a destination file or use of a random date.
Vyveva uses the Tor library to communicate with a C&C server. It contacts the C&C at three-minute intervals, sending information about the victimized computer and its drives before receiving commands. “However, of particular interest are the backdoor’s watchdogs used to monitor newly connected and disconnected drives, and a session watchdog monitoring the number of active sessions, like logged-on users. These components can trigger a connection to the C&C server outside the regular, preconfigured three-minute interval,” explains Jurčacko.
For more technical details about Vyveva, read the blog post (Are you) afreight of the dark? Watch out for Vyveva, the latest addition to the Lazarus toolkit on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and Twitter.