- Iran-linked advanced persistent threat (APT) group OilRig actively developed and used a series of downloaders with a similar logic throughout 2022. There are three new downloaders – ODAgent, OilCheck, and OilBooster – and newer versions of the SC5k downloader.
- The targets, all in Israel, included an organization in the healthcare sector, a manufacturing company, and a local governmental organization. All targets were previously affected by multiple OilRig campaigns.
- The downloaders use various legitimate cloud services for command and control communications and data exfiltration; namely, Microsoft Graph OneDrive API, Microsoft Graph Outlook API, and Microsoft Office EWS API.
BRATISLAVA, MONTREAL — December 14, 2023 — ESET researchers analyzed a growing series of new OilRig downloaders that the group used in several campaigns throughout 2022 to maintain access to target organizations of special interest, all located in Israel. They include an organization in the healthcare sector, a manufacturing company, and a local governmental organization. OilRig is an APT group believed to be based in Iran, and its operations, as are these latest downloaders, are aimed at cyberespionage. The new lightweight downloaders – SampleCheck5000 (SC5k v1-v3), OilCheck, ODAgent, and OilBooster – are notable for using legitimate cloud storage and cloud-based email services for command and control (C&C) communications and data exfiltration, namely, the Microsoft Graph OneDrive or Outlook Application Programming Interfaces (API), and the Microsoft Office Exchange Web Services API.
“On par with the rest of OilRig’s toolset, these downloaders are not particularly sophisticated. However, the continuous development and testing of new variants, experimentation with various cloud services and different programming languages, and the dedication to re-compromise the same targets over and over again, make OilRig a group to watch out for,” says ESET researcher Zuzana Hromcová, who analyzed the malware along with ESET researcher Adam Burgher.
ESET attributes SC5k (v1-v3), OilCheck, ODAgent, and OilBooster to OilRig with a high level of confidence. These downloaders share similarities with the MrPerfectionManager and PowerExchange backdoors – other recent additions to OilRig’s toolset that use email-based C&C protocols – with the difference that SC5k, OilBooster, ODAgent, and OilCheck use attacker-controlled cloud service accounts rather than the victim’s internal infrastructure.
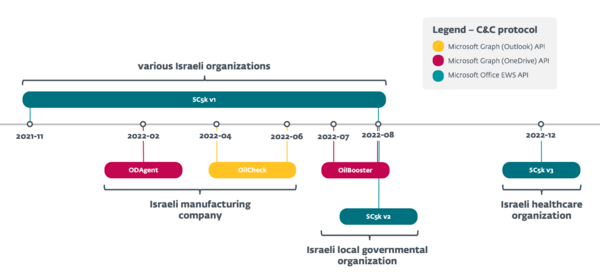
The downloader ODAgent was detected in the network of a manufacturing company in Israel – interestingly, the same organization was previously affected by OilRig’s SC5k downloader, and later by another new downloader, OilCheck, between April and June 2022. SC5k and OilCheck have similar capabilities to ODAgent but use cloud-based email services for their C&C communications. Throughout 2022, ESET observed the same pattern being repeated on multiple occasions, with new downloaders being deployed in the networks of previous OilRig targets: For example, between June and August 2022, ESET detected the OilBooster, SC5k v1, and SC5k v2 downloaders and the Shark backdoor, all in the network of a local governmental organization in Israel. Later, ESET detected yet another SC5k version (v3) in the network of an Israeli healthcare organization, also a previous OilRig victim.
OilRig has used these downloaders only against a limited number of targets, according to ESET telemetry, and all of them were persistently targeted months earlier by other OilRig tools. As it is common for organizations to access Office 365 resources, OilRig’s cloud service-powered downloaders can thus blend more easily into the regular stream of network traffic – apparently also the reason why the attackers chose to deploy these downloaders to a small group of especially interesting, repeatedly victimized targets.
OilRig, also known as APT34, Lyceum, Crambus, or Siamesekitten, is a cyberespionage group that has been active since at least 2014 and is commonly believed to be based in Iran. The group targets Middle Eastern governments and a variety of business verticals, including chemical, energy, financial, and telecommunications.
For more technical information about the latest OilRig downloaders, check out the blogpost “OilRig’s persistent attacks using cloud service-powered downloaders” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Timeline of OilRig’s downloaders
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multifactor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defenses in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centers worldwide, working in support of our shared future. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X (Twitter).