ESET Resource center

Customer
Mercury Engineering
Industry
Engineering
Solutions
ESET Endpoint Protection Standard
Organization Size
Large (1,000 - 9,999 employees)
Country
United States
Downloads
Customer story
Infographic
ESET Research warns Malaysian bank customers about three malicious Android apps targeting their money
ESET researchers have analyzed three malicious Android applications targeting customers of eight Malaysian banks. To make a profit off customers who have increasingly turned to online shopping during the pandemic, cybercriminals are tricking these eager shoppers into downloading malicious applications. In an ongoing campaign, the threat actors are trying to steal banking credentials by using fake websites that pose as legitimate services, sometimes outright copying the original. These websites use similar domain names to the services they are impersonating.
THE CUSTOMER
"To make the already couch-friendly approach of online shopping even more convenient, people are increasingly using their smartphones to shop. Smartphone purchases make up the majority of online shopping orders – most of them from vendor-specific applications,” says ESET researcher Lukáš Štefanko, who analyzed the malicious applications.
This campaign was first reported at the end of 2021, with the attackers impersonating the legitimate cleaning service Maid4u. Distributed through Facebook ads, the campaign tempted potential victims to download Android malware from a malicious website. In January 2022, MalwareHunterTeam identified three more malicious websites and Android trojans attributed to this campaign. Recently, ESET researchers found four additional fake websites. All seven websites impersonated services that are only available in Malaysia.

The biggest thing that stands out is its strong technical advantage over other product in the marketplace. ESET offers us reliable security, meaning that I can work on any project at any time knowing our computers are
protected 100%.
THE CUSTOMER
The copycat websites do not provide an option to shop directly through them. Instead, they include buttons that claim to download apps from Google Play. However, clicking these buttons does not actually lead to the Google Play store, but to servers under the threat actors’ control. To succeed, this attack requires the intended victims to enable the non-default “Install unknown apps” option on their devices. When the time comes to pay for the order, the victims are presented with payment options – they can pay either by credit card or by transferring the required amount from their bank accounts. At the time this research was active, it was not possible to select the credit card payment option.
THE CUSTOMER
After picking the direct transfer option, victims are presented a fake FPX payment page and asked to choose their bank out of the eight Malaysian banks provided, and then enter their credentials. The targeted banks are Maybank, Affin Bank, Public Bank Berhad, CIMB bank, BSN, RHB, Bank Islam Malaysia, and Hong Leong Bank. After the victims submit their banking credentials, they receive an error message informing them that the user ID or password they provided was invalid. At this point, the entered credentials have been sent to the malware operators. To make sure the threat actors can get into their victims’ bank accounts, the fake e-shop applications also forward all SMS messages received by the victim to the operators in case they contain Two-Factor Authentication (2FA) codes sent by the bank.
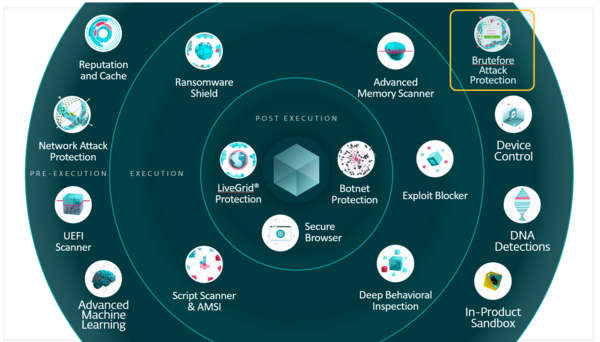
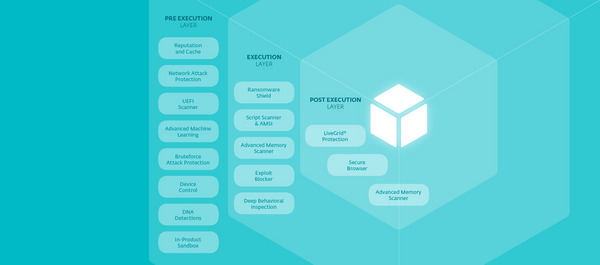
ESET PROTECT Platform is the world’s most formidable cyber threat prevention, detection and detecti.
Text and image element
KEY BENEFITS
- More time spent on other projects due to hassle-free nature of ESET´s security solution
- Robust customization and configuration abilities exceed the needs of IT staff
- Easy installation and deployment process made it easy to switch from previous AV
- More resources to be utilized on computers due to small footprint
- Downtime, issues, and user support are minimized by prompt response from technical support
Similar stories
LoJax: First UEFI rootkit found in the wild, courtesy of the Sednit group
Eset researchers have shown that the Sednit operators used different components of the LoJax malware to target a few government organizations in the Balkans as well as in Central and Eastern Europe
LoJax: First UEFI rootkit found in the wild, courtesy of the Sednit group
Eset researchers have shown that the Sednit operators used different components of the LoJax malware to target a few government organizations in the Balkans as well as in Central and Eastern Europe
LoJax: First UEFI rootkit found in the wild, courtesy of the Sednit group
Eset researchers have shown that the Sednit operators used different components of the LoJax malware to target a few government organizations in the Balkans as well as in Central and Eastern Europe
Featured Resources