1bn+
users worldwide
400k+
business customers
GREYCORTEX - Network Traffic Analysis
Network traffic analysis tool exploiting artificial intelligence, machine learning and big data to ensure secure IT operations for enterprise, government and critical infrastructure users. Provides:

Round-the-clock security monitoring

Powerful rapid detection & response capabilities

Deep visibility into the internal network

Easy to use functionality
Higher capability than other protocols
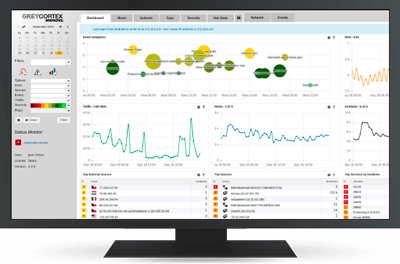
MENDEL collects much more information on network traffic than NetFlow, IPFIX or similar protocols. The web user interface presents comprehensive data on network traffic. Data includes management overviews, communication of the network, subnetworks, users and applications, peers, individual flows and their content - in order to investigate interesting events.
Identifies threats before damage occurs
MENDEL investigates beyond known threats to detect symptoms of malicious behavior at the atomic level. Threats are identified in their early stages. This decreases incident response time, prevents further damage and reduces overall risk to the organization.
Identifies threats in IoT Devices
MENDEL monitors network flow data, also in IoT devices, to identify traffic in and out of the network and communication flows between devices within the network. This includes additional anomalous devices, excessive communication from one device to another or to a host outside the network, and periodic communication that is common in advanced persistent threats.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
The ESET difference
Flow-based and packet-based technology
Instead of relying on older and limited SNMP polling, MENDEL leverages flow-based and content-based monitoring. Flow-based monitoring provides near real-time (1 minute intervals) visibility into network statistics and other summary and detailed issues. Deep content inspection (DCI) extends this information with real-time comprehensive contextual metadata (user identity, applications, for example).
Application monitoring and more
MENDEL Analyst constantly monitors communication of users and network applications of all ports and on TCP, UDP, ICMP and many other protocols. This enables monitoring of current and average bandwidth, response times, transit times, delay, jitter, ports in use, connection peers and more.
Powerful forensics
MENDEL Analyst generates metadata of network communication providing full contextual awareness – for example destination and source, user's identity and application protocol. Unlike technologies based on full packet capture, it allows the metadata on network traffic to be stored for a much longer time with low demands on storage capacity.
Detection methods
These include signature-based detection, deep packet inspection, network behavior analysis, specialized algorithms, network performance monitoring and application performance monitoring.
Product gallery
ESET GREYCORTEX MENDEL
Make an enquiry
Leave us your contact details to receive an offer tailored for your company´s needs. No commitment.
Looking for the complete security of your network?
Related bundled solutions
ESET Targeted Attack Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
- Endpoint Detection & Response
ESET Identity & Data Protection
- Two-factor Authentication
- Endpoint Encryption

ESET Dynamic Mail Protection
- Security Management Center
- Mail Security
- Cloud Sandbox Analysis
ESET Secure Business
- Security Management Center
- Endpoint Security
- File Server Security
- Mail Security
Stay on top of cybersecurity news
Brought to you by awarded and recognized security researchers from ESET's 13 global R&D centers.