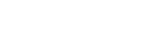1bn+
users worldwide
400k+
business customers
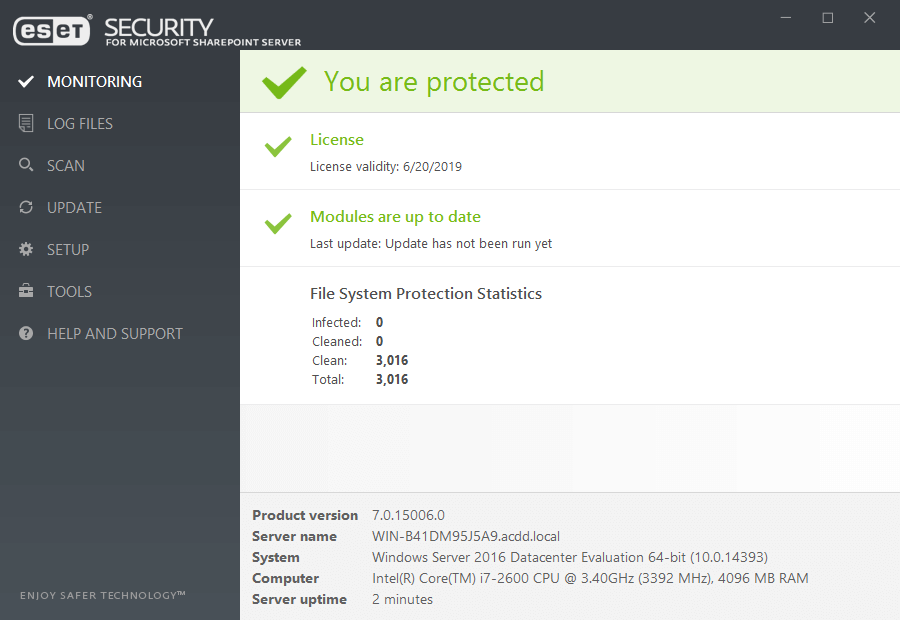
ESET Security for Microsoft SharePoint Server
Advanced protection for SharePoint servers against malicious uploads and unwanted files. Guarantees stable, conflict-free server environment. Provides:

Protection against ransomware

Data breaches prevention

Zero-day threats detection

File-less attacks prevention
Multilayered protection
All ESET's products have the ability to detect malware pre-execution, during execution and post-execution. An additional protection can be implemented in the form of endpoint detection and response with ESET Enterprise Inspector. Focusing on the whole of the malware lifecycle, not just on a specific part, allows ESET to provide the highest level of protection possible.
Unparalleled Performance
ESET products continue to excel in the performance arena and win third-party tests that prove how lightweight our endpoints are on systems. ESET Security for SharePoint is built on 64-bit core and includes DLL modules to ensure more RAM saving, faster computer startup times and allows us to natively support future Windows updates.
Machine learning
All ESET products currently use machine learning in conjunction with all of our other layers of defense and have done so since 1997. Specifically, machine learning is used in the form of consolidated output and neural networks.
Use cases
PROBLEM
Businesses want to be protected from ransomware attacks and ensure their network drives and SharePoint databases are safe from being encrypted.
SOLUTION
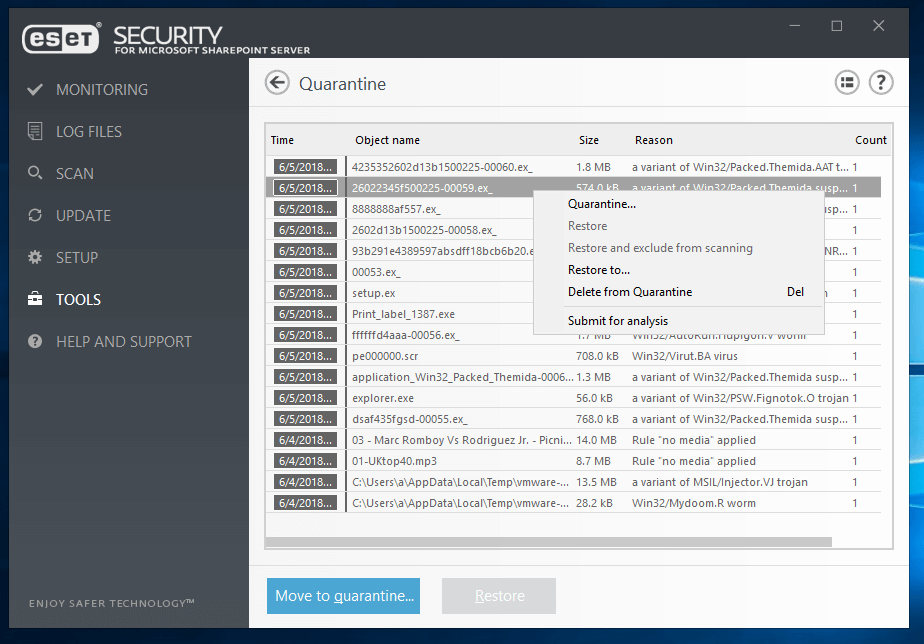
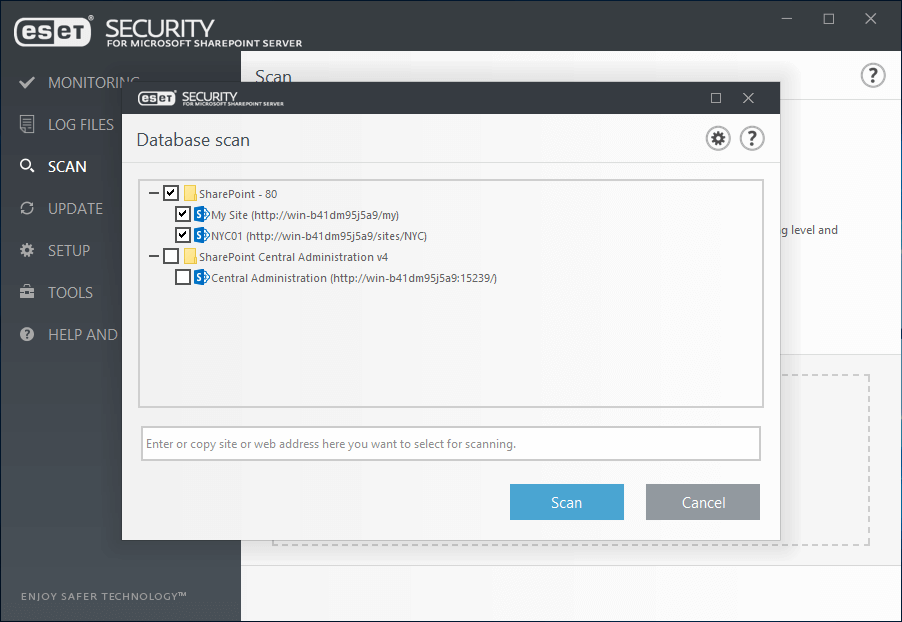
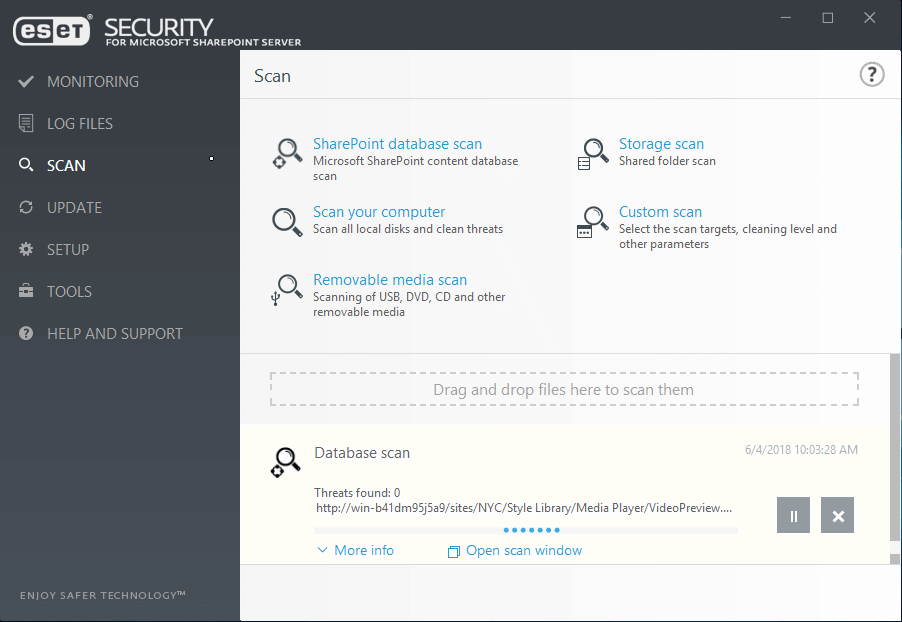
- On upload of a file into the SharePoint Server, ESET scans files to ensure they are not malicious.
- Network Attack Protection has the ability to prevent ransomware from ever infecting a system by stopping exploits at the network level.
- Our multilayered defense features an in-product sandbox that has the ability to detect malware that attempts to evade detection by using obfuscation.
- Leverage ESET’s cloud malware protection system to automatically protect against new threats without the need to wait for the next detection update.
- All products contain post-execution protection in the form of Ransomware Shield to ensure that businesses are protected from malicious file encryption.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
The ESET difference
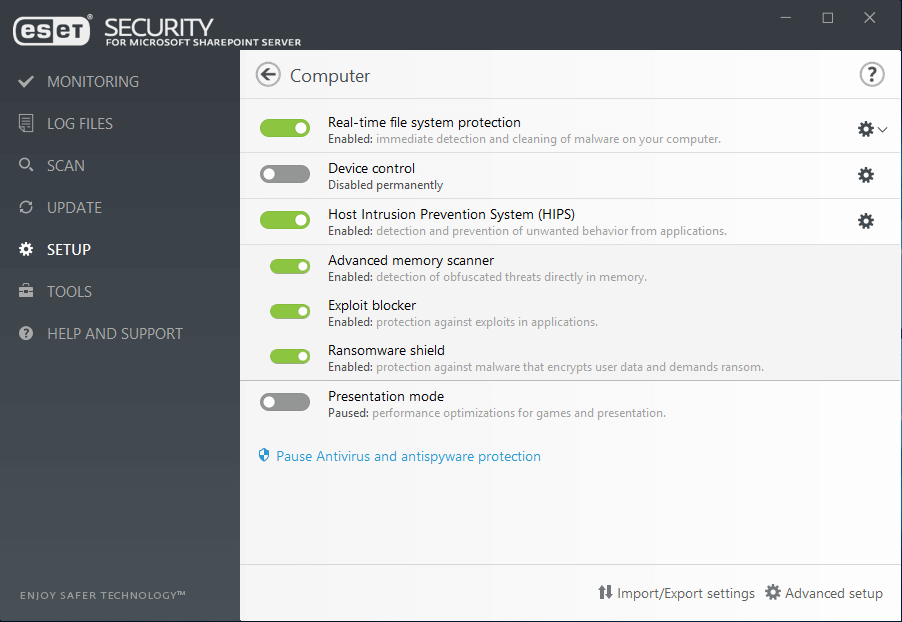
Ransomware Shield
An additional layer protecting users from ransomware. Our technology monitors and evaluates all executed applications based on their behavior and reputation. It is designed to detect and block processes that resemble behavior of ransomware.
Network Attack Protection
ESET Network Attack Protection improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities, for which a patch has not yet been released or deployed.
Behavioral Detection - HIPS
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.
AMSI/Protected Service Support
ESET products leverage the Antimalware Scan Interface (AMSI) to provide enhanced malware protection for users, data, applications, and workload. In addition, it utilizes the protected service interface that is a new security module built into Windows that only allows trusted, signed code to load and better protect against code injection attacks.
Database direct access
An optional method to pull files where ESET Security for SharePoint bypasses the SharePoint object model and pulls the file directly from the dedicated database server to provide even better performance.
Botnet Protection
ESET Botnet Protection detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.
Remote management
All ESET security products are managed from a single-pane-of-glass that can be installed on Windows or Linux. In addition to installing, ESET has a virtual appliance that you can simply import in for quick and easy setup.
Support for EDR
ESET Security for Microsoft SharePoint supports ESET’s endpoint detection and response solution - ESET Enterprise Inspector for immediate analysis and remediation of network security issues.
Explore our customized solutions
Please leave us your contact details so we can design a personalized offer to fit your requirements.
No commitment.
System Requirements
- Operating systems:
Microsoft Windows Server 2019, 2016, 2012 R2, 2012, 2008 R2, 2008
Microsoft Small Business Server 2011, 2008, 2003 - Supported SharePoint versions:
Microsoft SharePoint Server 2019, 2016, 2013, 2010, Microsoft SharePoint Enterprise 2010, Microsoft Office SharePoint Server 2007 - Compatible with ESET Security Management Center and ESET Remote Administrator 6. See more information about remote management compatibility.
Looking for complete security for your network?
Related bundled solutions
ESET Targeted Attack Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
- Endpoint Detection & Response
ESET Dynamic Endpoint Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
ESET Secure Business Cloud
- Cloud Administrator
- Endpoint Security
- File Server Security
- Mail Security
ESET Identity & Data Protection
- Two-factor Authentication
- Endpoint Encryption
Stay on top of cybersecurity news
Brought to you by awarded and recognized security researchers from ESET's 13 global R&D centers.