1bn+
users worldwide
400k+
business customers
ESET Cloud Administrator
Cloud-managed security for up to 250 seats saving cost, time and simplifying the protection of your network.

Setup and deployment within minutes

No need for additional hardware or software

Single point of network security management

Accessible safely via web browser from anywhere
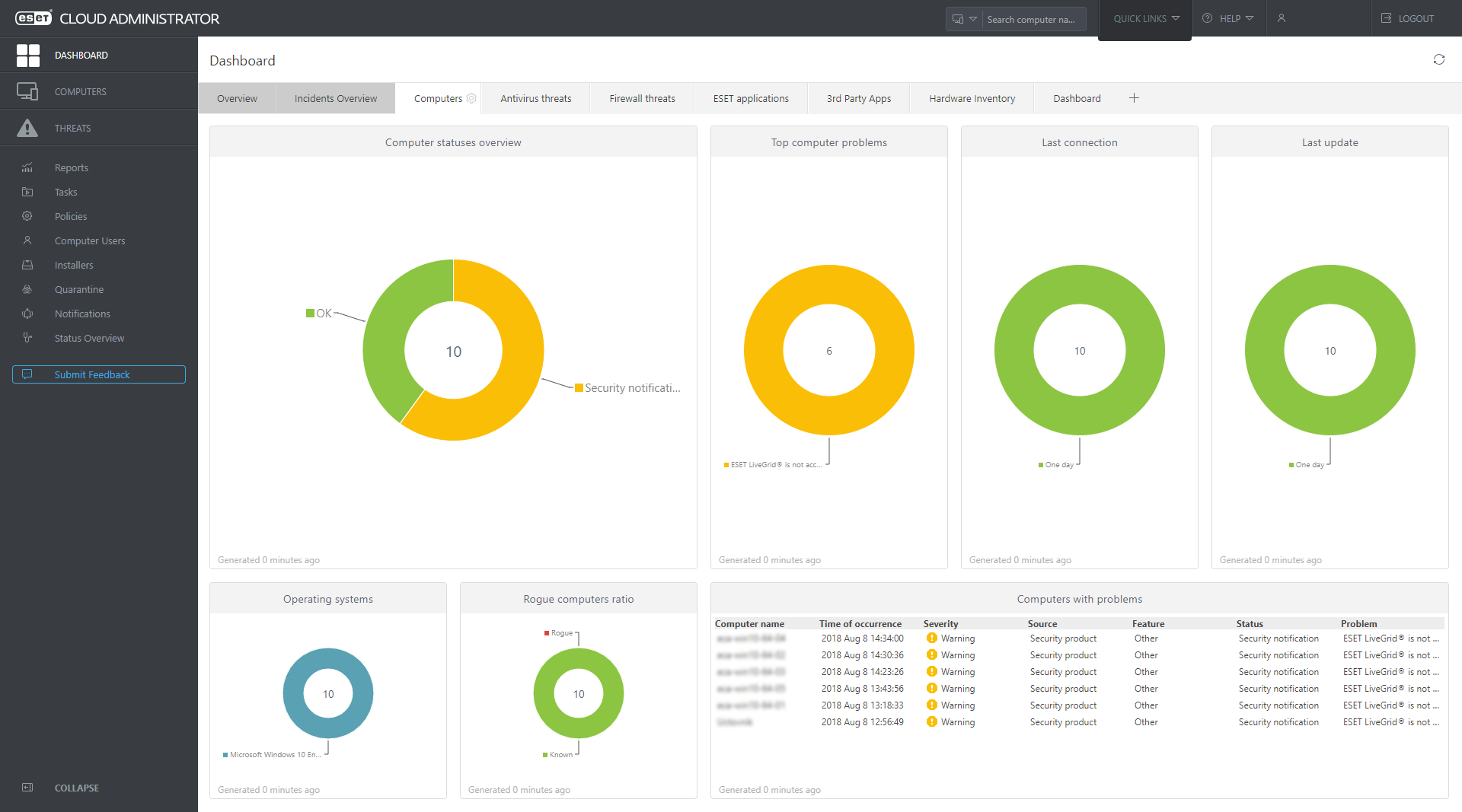
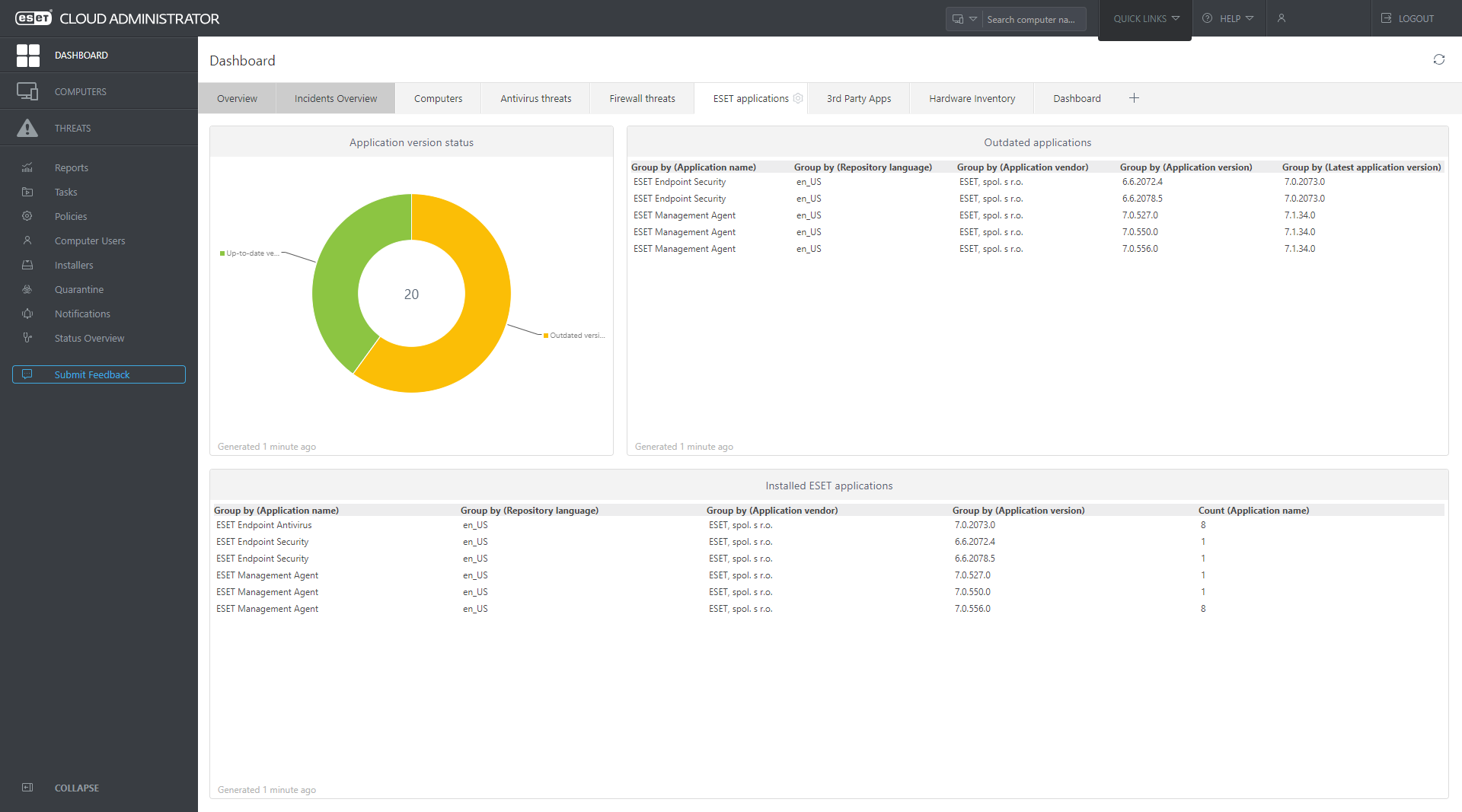
Total visibility
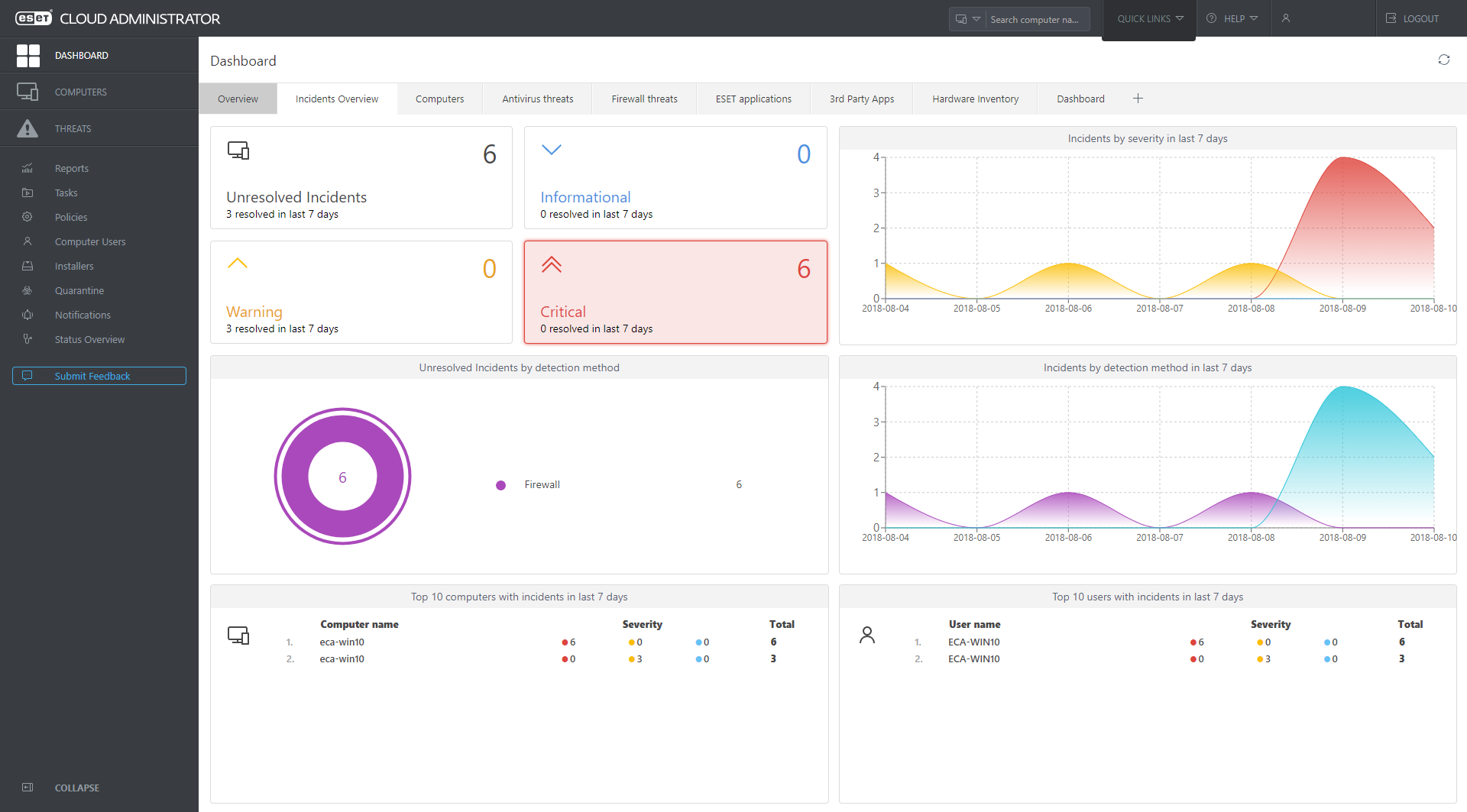
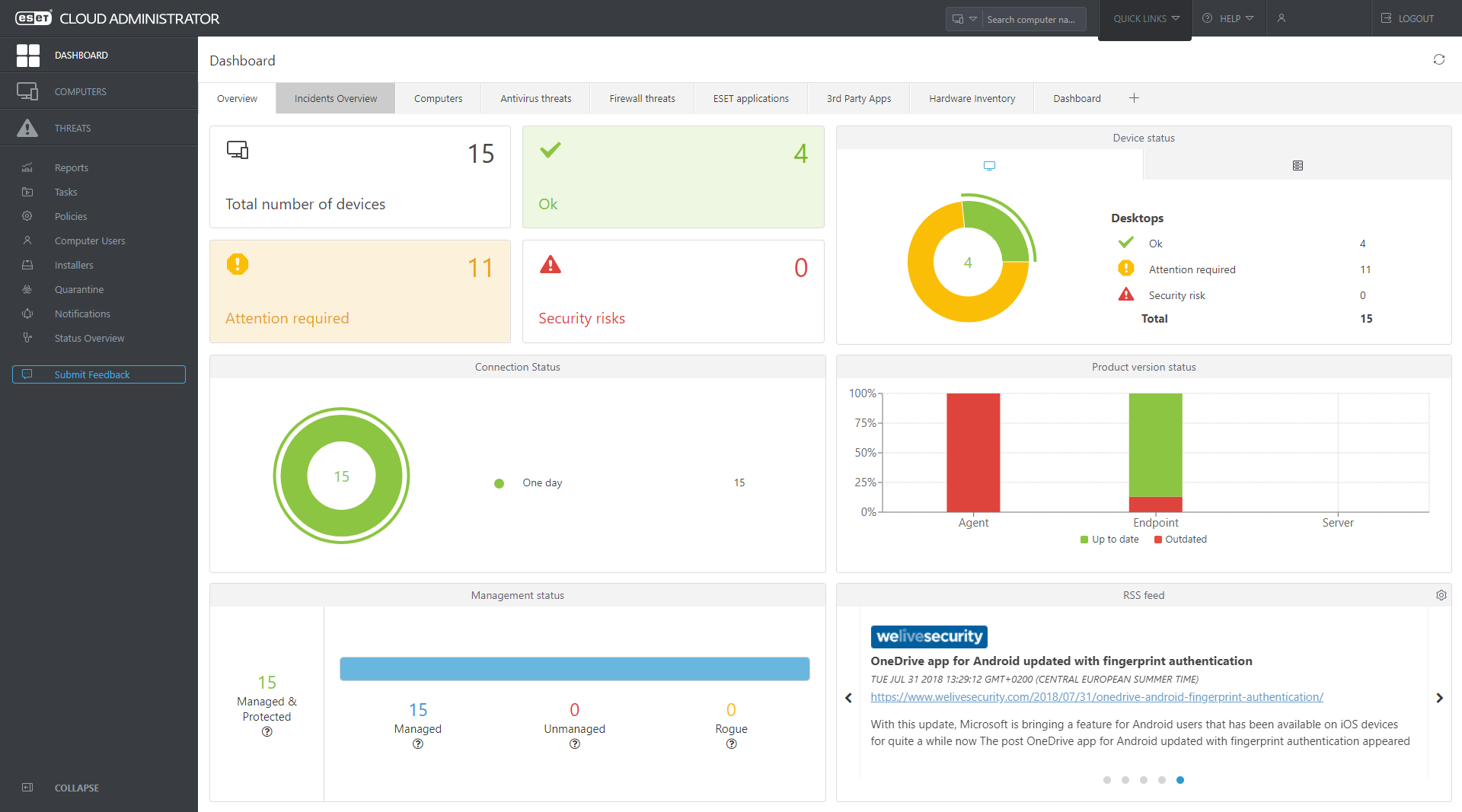
Monitor the overall network status with continuous automatic reports to a single pane of glass. Benefit from interactive charts and tables enabling a comprehensible, real time overview of your network security. Drill down to oversee the status of computers, threats or quarantined items.
Easy to use
Manage security for multiple endpoints from wherever you are. Remotely configure security products on connected endpoints. Automate policies and tasks for specific computers or static or dynamic groups.
Convenient
Get notified in real time to respond instantly to threats. Benefit from automated functions such as setup, server cleanups, upgrades and certificates management. Utilize all latest features and improvements without any action required.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
Get the level of protection that's right for your business
Each package includes individual standalone products for endpoint and server security, which have been bundled for your convenience.
CLOUD-BASED MANAGEMENT
- Remote Management
- Endpoint Security
- Endpoint Antivirus
- Mobile Security*
- Virtualization Security*
- Server Security
- Mail Security
- Full Disk Encryption add-on
CLOUD-BASED MANAGEMENT
- Remote Management
- Endpoint Security
- Endpoint Antivirus
- Mobile Security*
- Virtualization Security*
- Server Security
- Mail Security
- Full Disk Encryption add-on
CLOUD-BASED MANAGEMENT
ESET Endpoint Protection Standard
- Remote Management
- Endpoint Security
- Endpoint Antivirus
- Mobile Security*
- Virtualization Security*
- Server Security
- Mail Security
- Full Disk Encryption add-on
*ESET Cloud Administrator does not currently support mobile and virtualization security management, although these products may still be installed and activated with your license.
Complete easy-to-manage security for your network
Recommended solutions
ESET Secure Business Cloud
On top of protecting all your computers, laptops, and file servers, make your email gateway impenetrable. ESET mail security eliminates email-borne malware at the server level, before it can do any damage.
- Cloud-based management
- Endpoint security
- File server security
- Mail security
What's inside

ESET Endpoint Antivirus & Security for Windows
Leverages a multilayered approach that utilizes multiple technologies in dynamic equilibrium to constantly balance performance, detection and false positives.
Show features
Behavioral Detection - HIPS
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.
Network Attack Protection
ESET Network Attack Protection improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities, for which a patch has not yet been released or deployed.
In-product Sandbox
ESET’s in-product Sandbox assists in identifying the real behavior hidden underneath the surface of obfuscated malware. Utilizing this technology, ESET solutions emulate different components of computer hardware and software to execute a suspicious sample in an isolated virtualized environment.
Two-way firewall
Prevents unauthorized access to the company network. It provides anti-hacker protection, data exposure prevention, and enables defining trusted networks, making all other connections, such as to public Wi-Fi, restricted by default.
Ransomware Shield
An additional layer protecting users from ransomware. Our technology monitors and evaluates all executed applications based on their behavior and reputation. It is designed to detect and block processes that resemble behavior of ransomware.
AMSI/Protected Service Support
ESET products leverage the Antimalware Scan Interface (AMSI) to provide enhanced malware protection for users, data, applications, and workload. In addition, it utilizes the protected service interface that is a new security module built into Windows that only allows trusted, signed code to load and better protect against code injection attacks.
Exploit Blocker
ESET Exploit Blocker monitors typically exploitable applications (browsers, document readers, email clients, Flash, Java, and more) and instead of just aiming at particular CVE identifiers, it focuses on exploitation techniques. When triggered, the threat is blocked immediately on the machine.
Botnet Protection
ESET Botnet Protection detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.

ESET Endpoint Antivirus & Security for OS X/macOS
Provides complete protection and frees up valuable system resources. Fully manageable remotely.
Show features
Machine Learning
All ESET Endpoint products currently use machine learning in conjunction with all of our other layers of defense and have done so since 1997. Specifically, machine learning is used in the form of consolidated output and neural networks.
ESET Livegrid®
Whenever a zero-day threat such as ransomware is seen, the file is sent to our cloud-based malware protection system - LiveGrid®, where the threat is detonated and behavior is monitored. Results of this system are provided to all endpoints globally within minutes without requiring any updates.
In-product Sandbox
This helps to identify the real behavior hidden underneath the surface of obfuscated malware. Utilizing this technology, ESET solutions emulate different components of computer hardware and software to execute a suspicious sample in an isolated virtualized environment.
macOS Server Support
Ensures the solution does not interfere with macOS Server system and the most commonly used applications. Support for macOS Server for Mac 10.9 and above.
DNA Detections
Detection types range from very specific hashes to ESET DNA Detections, which are complex definitions of malicious behavior and malware characteristics. While the malicious code can be easily modified or obfuscated by attackers, the behavior of objects cannot be changed so easily and ESET DNA detections are designed to take advantage of this principle.
Data Access Protection
Strengthening the security with Web Control, Two-way Firewall, Anti-phishing and Device Control to prevent accessing malicious websites and network communication, fake website attempts to acquire sensitive information and unauthorized devices from your system.
ESET File Security for Microsoft Windows Server
Provides advanced protection for your company’s data passing through all general servers, network file storage including OneDrive, and multi-purpose servers to ensure business continuity.
Show features
Behavioral Detection - HIPS
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.
Network Attack Protection
ESET Network Attack Protection improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities, for which a patch has not yet been released or deployed.
Office 365 OneDrive Storage
After registration is done on a single server, ESET has the ability to scan OneDrive to provide visibility and monitor the trusted source of company storage.
AMSI/Protected Service Support
ESET products leverage the Antimalware Scan Interface (AMSI) to provide enhanced malware protection for users, data, applications, and workload. In addition, it utilizes the protected service interface that is a new security module built into Windows that only allows trusted, signed code to load and better protect against code injection attacks.
Ransomware Shield
An additional layer protecting users from ransomware. Our technology monitors and evaluates all executed applications based on their behavior and reputation. It is designed to detect and block processes that resemble behavior of ransomware.
Botnet Protection
ESET Botnet Protection detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.
Optional Cloud Sandbox Analysis
ESET Dynamic Threat Defense provides another layer of security for ESET File Security solutions by utilizing a cloud-based sandboxing technology to detect new, never before seen type of threats.
Unparalleled Performance
ESET products continue to excel in the performance arena and win third-party tests that prove how light-weight our endpoints are on systems. ESET File Security solutions are built on 64-bit core and include DLL modules to ensure more RAM saving, faster computer startup times and allow native support of future Windows updates.

ESET Mail Security for Microsoft Exchange Server
Provides an additional layer of security to organizations who are interested in stopping threats from ever reaching their users – multilayered security of the host itself.
Show features
Antispam
Using our own proprietary award-winning engine, spam is prevented from ever reaching your users’ mailboxes. Includes SPF and DKIM validation, backscatter protection and SMTP protection.
Anti-phishing protection
Prevents users from accessing web pages known for phishing by parsing messages body and subjects to identify URLs. URLs are then compared against phishing database and rules to decide whether they are good or bad.
Rules
ESET’s comprehensive rule system allows administrators to manually define email filtering conditions and actions to take with filtered emails.
Antimalware
Our second layer of protection built into ESET Mail Security provides detection of suspicious or malicious attachments to prevent users from being infected.
Hybrid office 365 scanning
Supports businesses who utilize Microsoft Exchange in a hybrid setup.
Web-based quarantine
Emails are automatically provided to users about their spam emails that were quarantined. Then users have the ability to log in and manage their own spam rather than this solely being managed by the administrator.

ESET Mail Security for IBM Domino
Additional layer of real-time email protection against targeted attacks, phishing and malware perfectly complementing ESET’s overlapping layers of security protection.
Show features
Antispam
Using our own proprietary award-winning engine, spam is prevented from ever reaching your users’ mailboxes. Includes SPF and DKIM validation, backscatter protection and SMTP protection.
Anti-phishing protection
Prevents users from accessing web pages known for phishing by parsing messages body and subjects to identify URLs. URLs are then compared against the phishing database and rules to decide whether they are good or bad.
Rules
ESET’s comprehensive rule system allows administrators to manually define email filtering conditions and actions to take with filtered emails.
Antimalware
Our second layer of protection built into ESET Mail Security provides detection of suspicious or malicious attachments to prevent users from being infected.
On-demand database scan
On-demand database scanner provides option to choose the targets to scan. Also, you can use the scheduler to run the database scan at a specific time or at an event.
Mail quarantine manager
Admin can inspect objects in this special IBM Domino database and decide to delete or release them. This feature offers simple management of emails quarantined by the transport agent.
Try before you buy
Submit your details to get a free 30 day trial license for ESET Cloud Administrator covering up to 25 seats.