In the wake of the initial WannaCry ransomware attack on May 12, we’ll be publishing news and updates. Here’s the latest:
As mentioned in a previous blog post, ESET detects and blocks the WannaCryptor.D threat and its variants. ESET currently detects ransomware behavior as FileCoder, and all ESET products provide multiple layers of technologies to protect computers from this infection.
Take these steps now
We strongly recommend using the following best practices for enhanced security.
1. Keep backups of your system
Plan to take backups of your system on regular intervals, and keep at least one such backup in offline storage, to protect your most recent work from an attack. ESET recommends using Backblaze personal backup.
2. Ensure that "Network drives" is selected in Real-time file system protection
With Network drive protection enabled, the ESET Real-time scanner will be able to trigger detection on an infected workstation, preventing the ransomware process from encrypting the drive. See Real-time file system protection for more information.
3. Restrict user permissions to the necessities
There are many types of restrictions, such as the restriction from accessing application data, and even some that are prebuilt as a Group Policy Object (GPO).
a. Disable files running from the AppData and LocalAppData folders.
b. Block execution from the Temp subdirectory (part of the AppData tree by default).
c. Block executable files running from the working directories of various decompression utilities
(for example, WinZip or 7-Zip).
Additionally, in ESET Endpoint Security/Antivirus, ESET Mail Security and ESET File Security, you can create HIPS rules to allow only certain applications to run on the computer and block all others by default: How do I create a HIPS rule and enforce it on a client workstation? (6.x)
4. Do not disable User Account Control (UAC)
Do not open attachments claiming to be a fax, invoice or receipt if they have a suspicious name or you did not expect to receive them.
5. Deploy a two-factor authentication (2FA) solution
6. Disable macros in Microsoft Office via Group Policy
Office 2013/2016 (the following link is for 2013 but are the same settings for 2016): Plan security settings for VBA macros for Office
7. Keep your systems up to date
To ensure you have the best protection available, keep your operating system and applications updated. Install the latest high priority updates offered in Windows Update tool, and check regularly or enable the Automatic Updates feature. New security updates patch the system vulnerabilities and reduces the risk of malware attack.
8. Disable RDP (Remote Desktop Protocol)
Encryption-based malware often accesses target machines using the Remote Desktop Protocol (RDP) tool integrated in Windows. RDP allows others to connect to your system remotely, so the attacker can misuse RDP to remove the protection and then deploy the malware.
a) Disable or change Remote Desktop Protocol
If you do not require the use of RDP, you can change the default port (3398) or disable RDP to protect your machine from Filecoder and other RDP exploits. For instructions on how to disable RDP, visit the appropriate Microsoft Knowledge Base article below:
o Windows XP
o Windows 7
o Windows 8
o Windows 10
For more information about RDP, see the following We Live Security article: Remote Desktop (RDP) Hacking 101: I can see your desktop from here!
b) Password-protect your ESET product settings
If you need to keep RDP running and cannot disable or change the RDP settings, you can use a password to protect the ESET product from being altered by an attacker. This prevents from unauthenticated settings modification, disabling the protection or even uninstalling the ESET product. We recommend using a different password from the one used for the RDP login credentials.
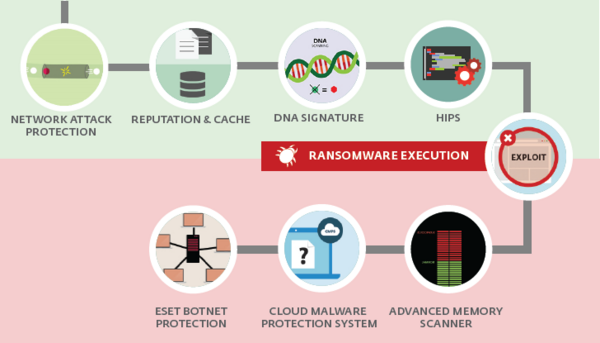
How ESET technology protects businesses
See the infographic below to see how all ESET solutions use multiple technologies for effective protection, including Advanced Memory Scanner, ESET Cloud Malware Protection System, and Exploit Blocker.
Additionally, ESET Endpoint Security/ESET Internet Security software provides an extra layer of protection with Network Attack Protection. This technology is able to block the exploit utilized in the spreading of WannaCry, Eternal Blue.
> Want to learn more about how ESET technologies protect against ransomware? Watch this brief video.
> See why businesses choose ESET’s accurate, light-footprint protection here.
Get the support you need
If you have questions or concerns about your ESET security solution, use the following resources:
- ESET North American customers: You can start a live chat session with a technical support agent at ESET Live Chat.
- ESET customers worldwide: Contact your local ESET partner for support.
- If you're not already an ESET customer: ESET Support Services are available to clean, optimize and secure your system. Call 866-944-3738 or click to schedule an appointment with ESET Support Services today!
