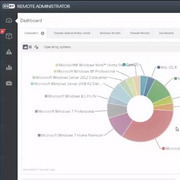
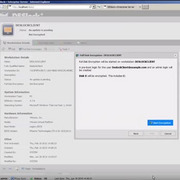
Product Datasheets
Prevent zero-day threats with powerful cloud-based sandboxing
Your business is only as secure as its weakest link.
Scalable and customizable solutions for your business.
Multilayered technology, machine learning and human expertise working together in dynamic equilibrium provided by the #1 global endpoint security partner from the EU.
Webinars
On-demand
Are you creating a potentially massive vulnerability when decommissioned hardware leaves the premises?
On-demand
We take a fresh look at zero-day threats, including some findings from recent research...
Tech Briefs
White Papers
Machine learning-based technologies increasingly help fight large-scale fraud, evaluate and optimize business processes, improve testing procedures and develop new solutions to existing problems.
For several years now, ESET experts from around the world have been contributing to our annual Trends report, which offers a brief review of the milestones reached in the world of cybersecurity and…
Ransomware attacks are different from denying access to data by permanently removing or erasing it.
While Machine Learning has proven to be a powerful tool in detecting malware for many years, the reality is that true Artificial Intelligence does not yet exist.
What our customers are saying
Don't just take our word for it. Read customer stories from users and businesses worldwide to see why they chose ESET.