With record numbers of employees working from home, the amount of remote desktop protocol ports exposed over the internet has increased.
Many employees benefit from using remote desktop protocol (RDP), such as system administrators who need to manage servers for websites or databases and employees who need access to shared resources for their everyday work. RDP allows access to servers, endpoints and resources residing in centralized locations or across remote networks.
When setting up firewalls to enable remote desktop protocol, network administrators have the option of either restricting RDP to the company network or allowing access over the internet. Exposing RDP ports to the outside world, however, brings a danger – hackers can discover and target them in an attack.
Using a tool like Shodan to search, hackers can currently find roughly 3.5 million RDP ports that are exposed to the internet:
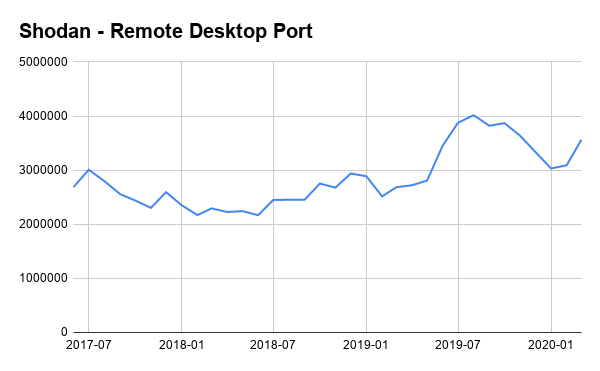
Source: https://blog.shodan.io/trends-in-internet-exposure/
The chart shows results only for port 3389, the default port number for RDP. Many companies use non-default port numbers for RDP – a kind of security by obfuscation. However, this represents no barrier to hackers, as it is trivial to scan and find other ports that show RDP activity.
Not surprisingly, Shodan reveals a recent rise in the number of devices with RDP exposed to the internet, which corresponds to the global shift to remote work witnessed in the most recent months.
For IT admins, it is paramount to ensure that RDP access over the internet is properly secured and that employees adhere to best password security practices. To that end, a brief look at some common attacks on RDP logins, along with security practices to counteract them, can help.
Brute force attacks
In a brute force attack, an attacker attempts to log in with random passwords, sometimes even making millions of attempts. This is normally automated via a software tool. If successful, this attack often prepares the path for the entry of ransomware, such as GandCrab and Sodinokibi, or other malware.
Recently, the writers of the TrickBot trojan added a new RDP brute force module. With the new upgrade, TrickBot has already attacked over 6,000 RDP servers. Using a strong password can make such brute force attacks computationally infeasible to accomplish.
To ensure that employees are using strong passwords, IT admins can use tools to compare hashes of employees’ passwords to a dictionary of hashes computed from weak passwords.
Credential stuffing attacks
A credential stuffing attack is similar to a brute force attack except that it attempts to use leaked credentials to log in. Leaked credentials can be found in the public domain, on hacking forums and in dark web marketplaces.
Hackers can automate these attacks by using credential stuffing software, such as SNIPR, Sentry MBA, STORM, Black Bullet, Private Keeper and WOXY. In order to evade firewalls and other protective technologies, attackers leverage batches of proxies (botnets) so that the repeated login attempts come from different IP addresses.
The success of credential stuffing relies on the fact that many users reuse their passwords. By always using a unique password, these kinds of attacks are easily frustrated.
Password spraying attacks
Password spraying is another variation of brute force in which an attacker strategically selects passwords to try against many user accounts. The idea is to avoid lockout policies from failed login attempts by pacing out the attack over a period of time and targeting a larger base of employee accounts.
Hackers can scrape employee usernames from the public domain with tools like Prowl, Raven and LinkedInt. These tools take company email domain names and scrape employee lists from LinkedIn.
With a list of usernames in hand, a hacker can then launch an automated password spraying attack.
Should hackers compromise even one standard user account, they can use that account to reveal the password and lockout policy of its Active Directory domain and fine-tune future password spray attacks against other users in the same domain.
ESET’s current detection for brute-force attacks – called “Botnet.CnC.Generic” – can block RDP, SQL and Server Message Block (SMB) attacks.
To better defend against password attacks, IT administrators should adhere to the following recommendations:
| Recommendation for securing RDP password | Reason | |
|---|---|---|
| 1 | Use complex and unique passwords for all admin/user accounts that can be accessed via RDP. | Protects against brute force, credential stuffing and password spraying attacks. |
| 2 | Doubly protect passwords with ESET Secure Authentication. | Provides an extra layer of protection in case passwords are compromised. |
| 3 | Establish a “3 invalid logon attempts lockout” policy via Group Policy. | Protects against brute force attacks. |
Managing networks more securely
Small or medium-sized business accustomed to using RDP to manage their remote employees may find that after a fresh install of endpoint security software, RDP connections are no longer working. This is the case, for example, when installing ESET Endpoint Security. For best security configuration, ESET products prohibit RDP access from the internet (via ESET Firewall) by default.
Ultimately, turning RDP off is the most secure option for any company due to its many security weaknesses. There are a variety of remote monitoring and management (RMM) tools that usually better meet business needs compared to RDP. However, it is important to be conscious of the security risks when selecting an RMM tool – vulnerabilities can affect them just as much as RDP.
For remote management of endpoint security software – a crucial piece of your cyber defenses – it is better to leverage robust tools like ESET Cloud Administrator or ESET Security Management Center.
If you need to let RDP through the ESET Firewall, you can follow these steps:
| Steps to set up RDP access in ESET Firewall* | |
|---|---|
| 1 | Create an individual rule in ESET Firewall to allow inbound communication on the local RDP port. |
| 2 | Add the public IP address of the IT admin’s computer to the firewall’s Trusted Zone. |
| 3 | Make sure the admin computer has a static IP address so that it will always be recognized in the Trusted Zone. |
| 4 | If Windows Firewall is not already disabled, deactivate any existing Windows Firewall RDP rules. |
*Computers running macOS can create a firewall rule following the steps detailed here.
IT admins should also utilize the following security configurations available in Group Policy:
| Recommendation for securing RDP Host via Windows Group Policy | Reason | |
|---|---|---|
| 1 | Enable “High” 128-bit client connection encryption. | Encrypts the data sent between RDP clients and servers. |
| 2 | Require secure RPC communication. | Allows only authenticated and encrypted requests from RPC clients. |
| 3 | Require use of TLS for RDP connections. | Requires the use of TLS 1.0 to authenticate the RD Session Host server. |
| 4 | Require user authentication for remote connections by using Network Level Authentication. | Requires that client computers support Network Level Authentication to connect to the RD Session Host server and that user authentication happens earlier in the remote connection process. |
For a deeper dive into the threats facing the use of RDP and more recommendations, read our white paper: Configuring security for a remote, but not distant future.
