1bn+
users worldwide
400k+
business customers
ESET Endpoint Encryption
A simple to use encryption application providing full remote control of endpoint encryption keys and security policy for files on hard drives, portable devices and emails. Ensures:

Zero data breaches

Compliance with requirements

Seamless encryption
Manage devices anywhere
ESET Endpoint Encryption can manage devices anywhere in the world without requiring VPNs nor any firewall exceptions. Management is handled by utilizing HTTPS internet connectivity making it extremely simple for businesses of any size to install and setup.
Zero impact on productivity
The implementation of encryption is completely transparent for the users and requires no action on their part. There is no extra overhead for IT departments and no need for user training.
Fast, seamless deployment
Server installation of ESET Endpoint Encryption usually takes less than 10 minutes, with complete setup of the solution under one hour.
Use cases
PROBLEM
Every company utilizes removable media devices to move data from one computer to another, but most companies do not have a way to verify that the data is staying only on company devices
SOLUTION
- Implement user-proof removable media to restrict the moving of data outside of the company.
- Restrict access to removable media devices to selected users.

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 32,000 endpoints
The ESET difference
No server required
ESET Endpoint Encryption requires no server for deployment and can seamlessly support remote users.
No special hardware required
TPM chips are optional but not required for using Full Disk Encryption.
Fully validated
ESET Endpoint Encryption is FIPS 140-2 validated with 256 bit AES encryption.
Multi-platform
Encryption supported across Windows 10, 8, 8.1, 7, Vista, XP, and Server 2003 – Server 2019 and iOS.
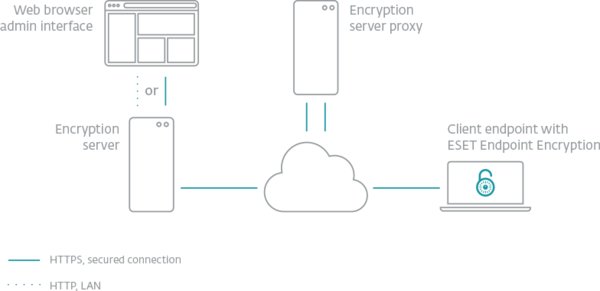
The management of endpoints via server proxy requires no incoming connections, making it extremely safe and easy to set up. No firewall exclusions or open ports are required. The encryption server can run on any Windows PC or server.
Explore our customized solutions
Please leave us your contact details so we can design a personalized offer to fit your requirements.
No commitment.
Supported features
One-click encryption of entire hard drive?
Try ESET Full Disk Encryption
- Comply with data protection regulations like GDPR, PCI and others
- Monitor encryption on user machines remotely
- Protect company data with a simple yet powerful solution
Looking for the complete security of your network?
Related enterprise-grade solutions
ESET Identity & Data Protection
- Two-factor Authentication
- Endpoint Encryption
ESET Endpoint Protection Advanced
- Security Management Center
- Endpoint Protection Platform
Related products and services
- ESET Secure Authentication
Powerful two-factor authentication makes access to networks and data safe and problem-free. - Data Loss Prevention
Safetica protects you from expensive data leaks and unnecessary personnel costs. - ESET Endpoint Security
Award-winning multilayered technology combining machine learning, big data and human expertise.
Stay on top of cybersecurity news
Brought to you by awarded and recognized security researchers from ESET's 13 global R&D centers.