Botnets are one of the top cyber threats to look out for in 2020, according to Forrester, and with a dispersed, remote workforce, many organizations may be more vulnerable than ever before. Botnet operations can become incredibly sophisticated, carrying out a wide range of illicit activities: collecting browser information, harvesting passwords, stealing login credentials from banking websites, or deploying ransomware.
One of the most infamous botnets is Trickbot, which has compromised over a million computing devices around the world since 2016. Earlier this month, ESET helped to disrupt Trickbot in a global collaboration with Microsoft and other partners.
ESET first detected Trickbot in late 2016, and it has since been recognized as one of the most prevalent banking malware families across the globe. The botnet has targeted several different industries – including education, real estate and government – but the most frequently targeted seems to be the financial sector. With its capabilities for stealing banking credentials and performing fraudulent transactions, Trickbot is a threat to financial data at any business, so businesses must be prepared to protect themselves against this threat.
Trickbot is extremely versatile, with a modular design that allows it to perform an array of malicious actions using a variety of plugins. ESET analyzed nearly 30 different plugins, of which over a third were infostealers. One of these, named injectDll, uses browser hooks to steal user credentials from banking websites, allowing Trickbot’s operators to perform fraudulent bank transfers and steal money from individuals and organizations. Another plugin, known as pwgrab, steals passwords from Filezilla, Microsoft Outlook and WinSCP. These are just two examples of the damage Trickbot could wreak on businesses once it has infested your systems.
A prolific distributor of ransomware – one of the largest threats to the upcoming US election – Trickbot is also a potential danger to election infrastructure. Operators of the botnet could infest a computer system used to report results or store voter rolls, sowing high levels of chaos and distrust among the electorate. The collaborative operation to disrupt Trickbot helped cut off key infrastructure, meaning that the botnet operators are no longer able to initiate new compromises or deploy ransomware as easily.
ESET telemetry shows Trickbot detection numbers plummeting in tandem with the disruption effort:
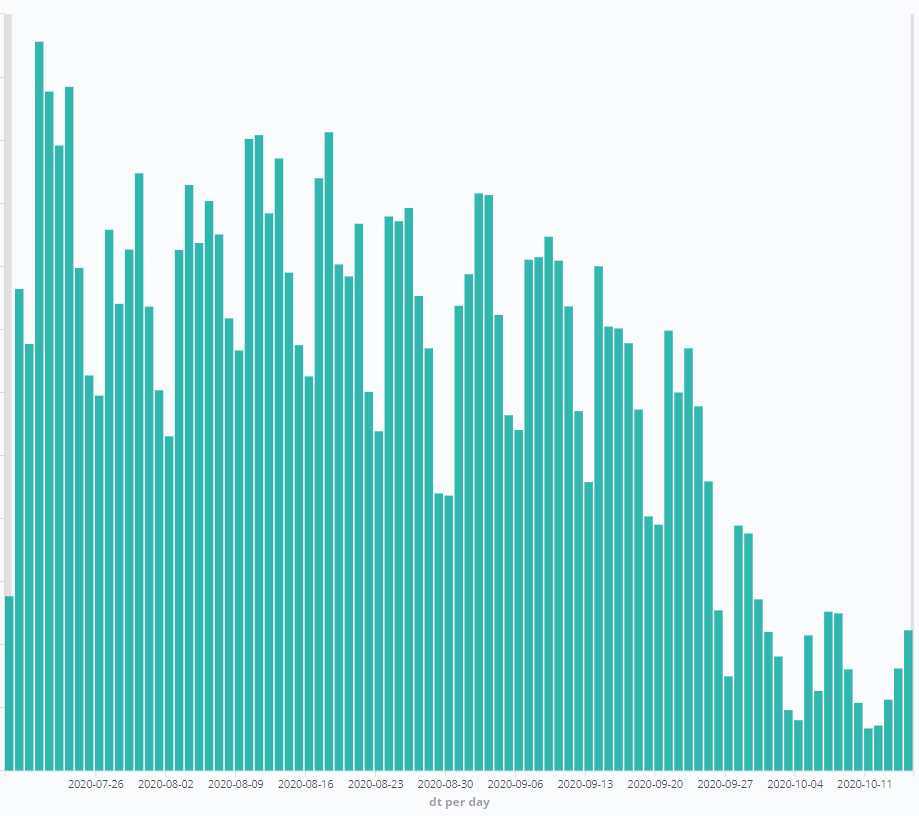
Figure 1: Trickbot detection numbers from July to October 2020
While the threat of Trickbot seems to have lessened for now, maintaining vigilance for other botnet attacks is still paramount. At the same time as Trickbot’s disruption, the rising detections in ESET telemetry for the Emotet botnet indicated a ramping up of Emotet’s activities, even downloading Trickbot, as well as Qbot, malware:
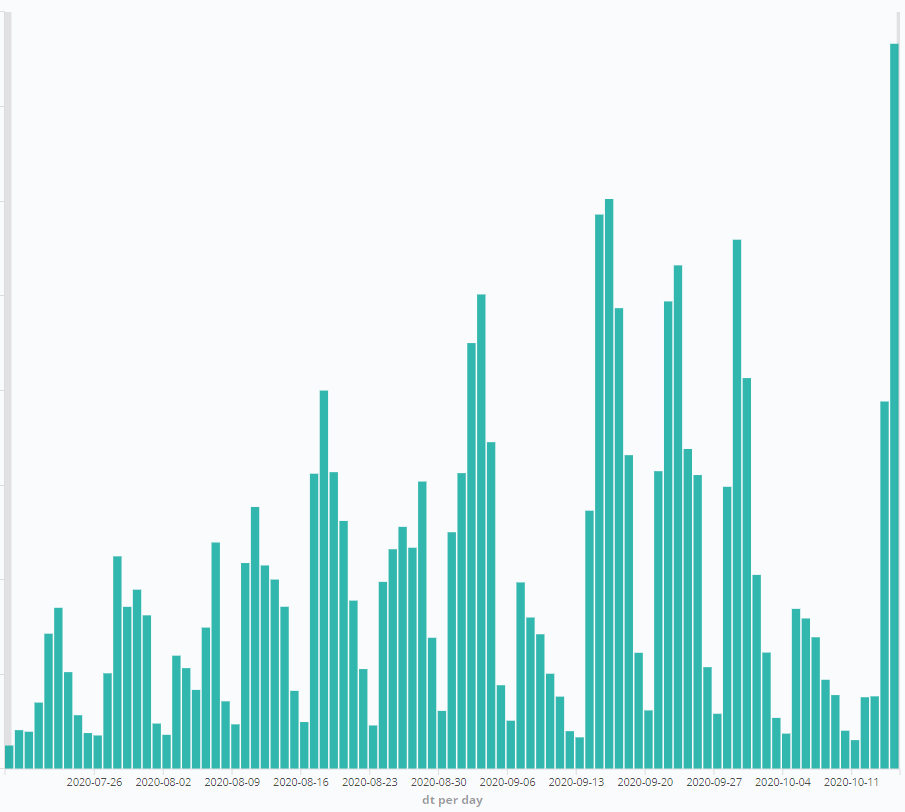
Figure 2: Emotet detection numbers from July to October 2020
The Emotet malspam campaign was recently bombarding users in Greece, Japan and Lithuania:
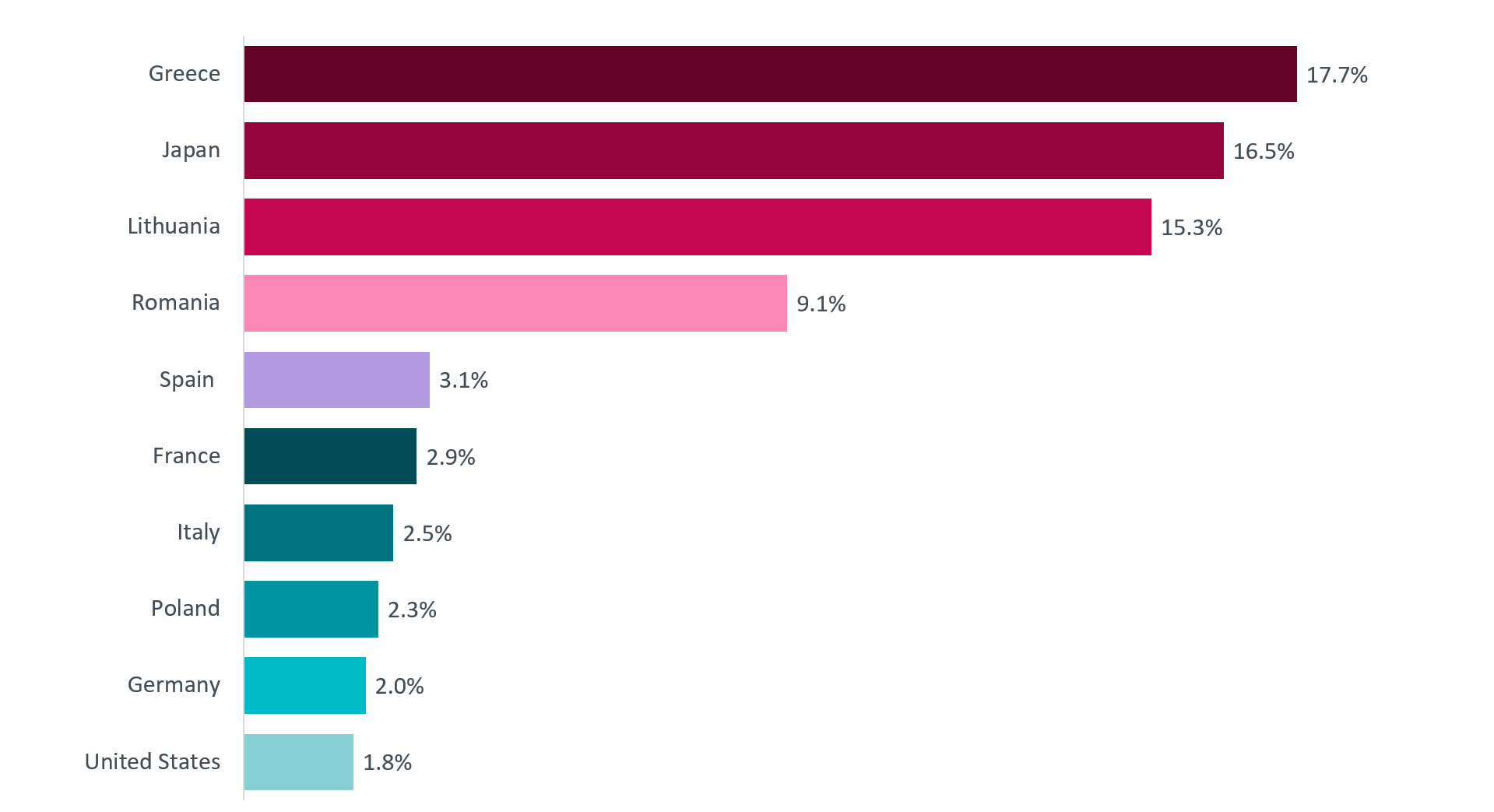
Figure 3: Countries most targeted by Emotet from July to October 19, 2020
Facing such a threat may seem like a daunting task, but there are a few ways businesses can protect themselves from botnet operations. Primarily, it is crucial to protect all endpoints with a security solution that has robust detection modules, such as ESET Endpoint Security. Businesses also need to ensure that their networks are always patched with the latest security updates to avoid falling victim to vulnerabilities that threat actors may exploit. Additionally, remote ports can provide an access point for hackers, so restrict access as far as possible – especially to remote desktop protocol (RDP) ports.
To find out more about ESET’s efforts to disrupt the Trickbot botnet, read ESET takes part in global operation to disrupt Trickbot on WeLiveSecurity.