When cybersecurity experts and vendors describe phishing attacks, they usually split them into two big groups.
The first group consists of spam campaigns targeting a broad general audience with simple fraudulent messages. This approach has a low success rate but can be easily deployed en masse. The second group involves sophisticated attacks tailored for a specific person or group of people. This requires more time and planning; however, this effort pays off with higher success rates and/or other value that attackers derive.
But there are also attacks that stand somewhere in the middle and benefit from both approaches. For example, their fraudulent messaging is simple and can target broader audiences, but at the same time they are able to avoid the usual phishing red flags, largely because malicious email attachments are obfuscated with specialised tools.
ESET researchers documented such an attack when they discovered an email phishing campaign targeting European businesses.
Advanced phishing campaigns using AI and various evasion techniques are on the rise and can pose a challenge even for managed service providers (MSPs), which aim to deliver seamless IT services, including cybersecurity, to their customers while also keeping in mind their own protection. Risk from these types of campaigns are mounting because even the most focused employees may fall victim to malicious emails despite previous awareness training. Moreover, basic types of anti-phishing protection may be unable to detect these threats.
To address these risks, ESET has beefed up the prevention capabilities, incorporating advanced Anti-Malware, Antispam, and Anti-Phishing protection into ESET PROTECT, a formidable cyber threat prevention, detection, and response platform that MSPs can use. Having all these automated layers of protection in one service, ESET PROTECT minimises the email attack surface, simultaneously reducing the complexity of subsequent security processes.
The most prevalent attack
Year after year, numerous surveys and reports confirm that phishing is the most prevalent attack vector.
The latest ESET H2 2023 Threat Report shows that malicious HTML files sending victims to phishing websites (HTML/Phishing.Agent trojan) remain by far the most numerous type of email threat. Overall, these attacks comprise almost a quarter (23.4 percent) of all cyber threats detected by ESET.
When it comes to the business sector, one in four U.S. companies that faced a cyberattack noticed that the initial vector was phishing in 2022.
Between 2017 and 2023, the proportion of phishing attacks among all cyberattacks reported by U.K. organisations (businesses and charities) rose from 72% to 79%, according to a survey conducted by the U.K. Department for Science, Innovation and Technology. Also, 56% of the surveyed businesses responded that they consider phishing attacks as the most disruptive that businesses face.
Phishing doesn’t have to be simple
Many of these phishing campaigns can be easily dodged by following simple awareness advice. However, as with most things in the world of IT, things are getting more complex and sophisticated — so is phishing.
ESET researchers spotted one of the latest examples of this trend just recently when monitoring the Remote Access Trojan (RAT) Rescoms, also known as Remcos.
RATs are malware that allows attackers to remotely control an infected computer, and ESET researchers discovered several recent email phishing campaigns using Rescoms and targeting businesses in European countries, including Spain, Poland, Slovakia, Bulgaria, and Serbia.
The goal of those campaigns of an unknown actor was to obtain credentials stored in browsers or email clients, which in case of a successful compromise would open the possibility for further attacks.
What makes these Rescoms campaigns special is that they use AceCryptor, a cryptor-as-a-service malware that is designed to hide other malware from cybersecurity tools.
In H2 2023, ESET detection engines saw and blocked over double the attacks using AceCryptor in comparison with H1 2023.
Moreover, this cryptor wasn’t the only tool that did its bit. In order to make phishing emails look as credible as possible, the threat actor deployed several strategies:
- All emails look like B2B offers for the victim companies.
- Email addresses used to send spam emails were imitating domains of other companies.
- Business email compromise (BEC) was involved in multiple campaigns — attackers abused previously compromised email accounts of other company employees to send spam emails.
- Attackers did their research and used existing companies and even existing employees’/owners’ names and contact information when they were signing those emails.
- The content of emails was in many cases quite elaborate.
<image. 1 - below> This phishing email, *with a malicious attachment, contains a message followed by information about the processing of personal information by the alleged sender:
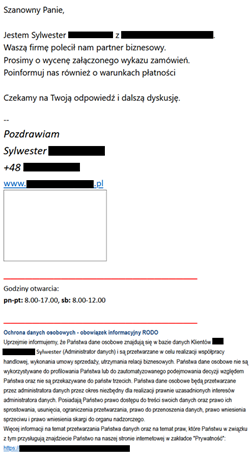
Translated message:
Dear Sir,
I am Sylwester [redacted] from [redacted]. Your company was recommended to us by a business partner. Please quote the attached order list. Please also inform us about the payment terms.
We look forward to your response and further discussion.
--
Best Regards,
How to defend
Because regular cybersecurity awareness training for employees may not be enough, and MSPs often need to take care not only about their protection but also their clients’ protection, the answer to this situation must be multi-layered protection.
The main idea is to protect businesses during several stages of the attack — when a malicious email arrives in the mailbox, when an employee opens it, when they click on an attached link or file, and when malware enters the company’s system if all previous defences were avoided.
For example, look at the multi-layered protection incorporated in the ESET PROTECT Platform:
- Anti-Spam technology filters spam messages with almost 100% accuracy.
- Anti-Phishing prevents users from accessing web pages known for phishing by parsing message bodies and subject lines to identify URLs. URLs are then compared against the phishing database and rules to determine the presence of a phishing attempt.
- Anti-malware scans email attachments to determine whether it is malicious, unknown, or safe.
- ESET’s in-product Sandbox assists in identifying the real behaviour hidden underneath the surface of obfuscated malware.
- If ESET Mail Security is unsure of the potential threat, it can forward the attachment to the proactive cloud-based threat defence tool called ESET LiveGuard Advanced. It analyses samples in a cloud sandbox, and then submits the result back to Mail Security within minutes.
- If the malicious attachment is opened, it will face ESET Endpoint Security monitoring and evaluating all executed applications based on their behaviour and reputation. It is designed to detect and block suspicious processes.
Such multi-layered and automated protection can detect even advanced phishing email threats such as the recent Rescoms campaigns. In fact, ESET PROTECT placed second in the latest AV-Comparatives Awards with 99.9% malware samples blocked with zero false positives in enterprise category. Overall, ESET received a Top-Rated Product Award in 2023.
Battling alert fatigue
An important part of an MSPs’ defence is also mitigation of alert fatigue, a situation where IT admins are so overwhelmed by alerts that they miss or ignore serious issues.
To make MSPs admins’ lives easier, the ESET PROTECT Platform allows admins to automate a variety of actions, including the resolution of sophisticated incidents. ESET also has complex MSP program with subscription flexibility, a unified ecosystem, automated responses, and integrations with the major RMM and PSA players.
All these efforts have been proven to decrease disruptions in daily workflow of ESET customers:
“Day-to-day life doesn't tend to get overly disrupted with ESET, which is brilliant for the help desk. They don't want to be receiving calls, truth be told. But we want to be ensured that we are on top of things, and our customers can work without having to chew up too much of our time,” says Andrew Owens, Head of Sales in Risc IT Solutions, a cloud solutions provider cooperating with ESET for the last 10 years.
Mastering vigilance without burnout
It is estimated that there are 361 billion emails sent and received daily around the world, with more than 45 percent of them spam. With such a plentiful threat landscape, it is important for businesses to be prepared for attacks on an almost daily basis without wearing down the IT team.
Having a highly automated security ecosystem from a global leader in digital security is a great way to master vigilance in the world of constant cyberthreats.