FamousSparrow exploited the Microsoft Exchange vulnerability chain known from March 2021.
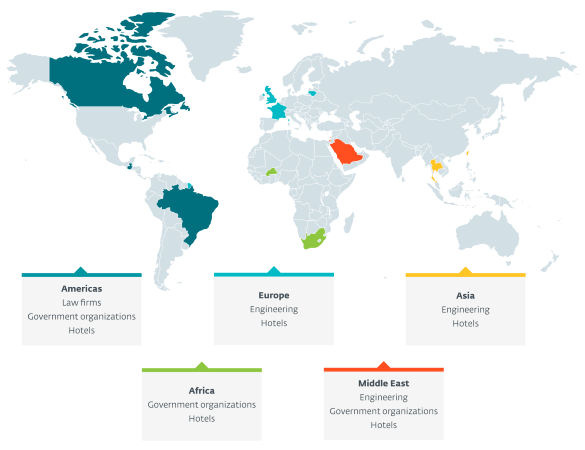
BRATISLAVA, MONTREAL – ESET researchers have uncovered a new cyberespionage group attacking mainly hotels worldwide but also governments, international organisations, engineering companies and law firms. ESET has named this group FamousSparrow and believes it has been active since at least 2019. FamousSparrow’s victims are located in Europe (France, Lithuania, the UK), the Middle East (Israel, Saudi Arabia), the Americas (Brazil, Canada, Guatemala), Asia (Taiwan) and Africa (Burkina Faso). The targeting suggests that FamousSparrow’s intent is cyberespionage.
Reviewing telemetry data during its investigation, ESET Research discovered that FamousSparrow leveraged the Microsoft Exchange vulnerabilities known as ProxyLogon that ESET reported on in March 2021. This remote code execution vulnerability chain was used by more than 10 APT groups to take over Exchange email servers worldwide.
According to ESET telemetry, FamousSparrow started to exploit the vulnerabilities on 3rd March 2021, the day following the release of the patches, meaning it is yet another APT group that had access to the details of the ProxyLogon vulnerability chain in March 2021. “This is another reminder that it is critical to patch internet-facing applications quickly, or, if quick patching is not possible, to not expose them to the internet at all,” advises Matthieu Faou, ESET researcher who uncovered FamousSparrow along with his colleague Tahseen Bin Taj.
“FamousSparrow is currently the only user of a custom backdoor that we discovered in the investigation and called SparrowDoor. The group also uses two custom versions of Mimikatz. The presence of any of these custom malicious tools could be used to connect incidents to FamousSparrow,” explains ESET researcher Tahseen Bin Taj.
Although ESET Research considers FamousSparrow to be a separate entity, there are some connections to other known APT groups. In one case, the attackers deployed a variant of Motnug, a loader used by SparklingGoblin. In another case, a machine compromised by FamousSparrow was also running Metasploit with cdn.kkxx888666[.]com as its command and control server, a domain related to a group known as DRDControl.
For more technical details about FamousSparrow, read the blogpost “FamousSparrow: A suspicious hotel guest” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
Geographic distribution of FamousSparrow targets
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multi-factor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defences in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centres worldwide, working in support of our shared future. For more information, visit our website or follow us on LinkedIn, Facebook, and Twitter.