Fitness trackers and other wearable smart devices are taking the world by storm. They come in all shapes and sizes with a myriad of price points but how secure are they? And how well do they handle your precious private data?
On this blog we constantly talk about how important it is to protect your information, no matter how mundane or innocuous it may seem.
From the very early blogs about giving away email addresses for cookies to the more recent info stealing browser extensions, folks having vulnerable data is a recurring them.
Today it’s wearables: specifically fitness related wearables which interface with a smartphone via Bluetooth or Bluetooth Low Energy (BLE).
‘Bluesniping’
’Bluesniping’ is a practice whereby BLE data being transmitted from a fitness wearable (specifically those made by Nike, FitBit and Jawbone in this instance) to a smartphone can be intercepted by a different smartphone running a special app.
Although it’s become fairly common for folks to post their workouts and fitness info to social media, some are still highly protective of that data.
“As with all personal GPS information it could be used to map your whereabouts, times leaving and arriving back at home or other premises,” explains Mark James, ESET security specialist.
“Along with personal health information, this could be used in targeted phishing attacks to enable the “Personal” touch when trying to trick you into following a link or visiting a web page.”
Yes any form of information is valuable but how likely is the average user to see or experience this kind of attack?
“As with a lot of these types of data sniffing vulnerabilities it is fairly easy with the right hardware, as components are getting faster and smaller.”
Although targeting a different kind of information Israeli researchers managed to fit a data sniffing device into a pitta bread: devious and delicious.
“The need to have to have a large room full of electronics is not the case anymore, these components are small enough to keep in our pockets and often a tablet or smartphone could be used as the interface, anyone choosing to sniff and abuse this data could easily do so covertly.”
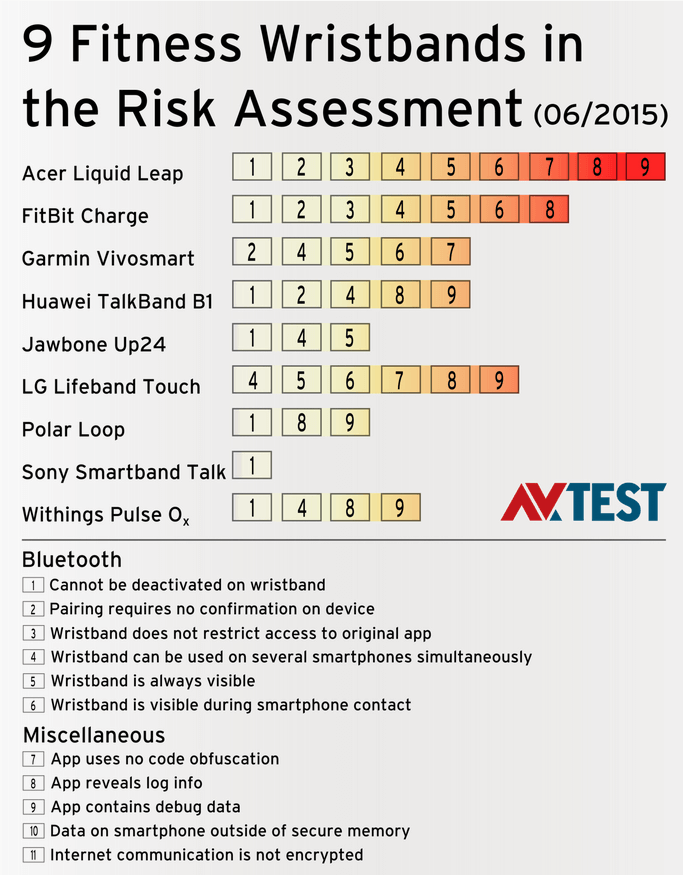
AV-TEST test wearables
AV-TEST, independent Antivirus testing organisation and researchers, have put nine of the most popular pan device fitness wristbands to a series of security tests.
Interestingly enough their conclusion on how to stay secure whilst using a fitness tracker is, rather candidly, simply not to use one.
They put them through their security paces in a number of different ways, as illustrated by the accompanying infographic.
The results, as you can see, are quite startling but not entirely surprising. Personal data flying around just waiting to be sniffed or scooped up seems to be a common theme with smart devices and IoT adjacent tech.
And AV-TEST are bang on: if you don’t want your data to be vulnerable and you worry about it being exploited then simply don’t use fitness trackers, or IoT… or leave your house… ever.
Join the ESET UK LinkedIn Group and stay up to date with the blog.
Do you use a fitness tracker? Do you worry about these kinds of exploits?