BRATISLAVA, MONTREAL – A few days ago, ESET researchers discovered a new supply-chain attack compromising the update mechanism of NoxPlayer, an Android emulator for PCs and Macs. Three different malware families were spotted being distributed from tailored malicious updates to selected victims with no sign of leveraging any financial gain, but rather, only cyberespionage capabilities were seen. ESET dubbed the malicious operation NightScout.
BigNox is a company based in Hong Kong that provides various products, primarily an Android emulator for PCs and Macs called NoxPlayer. The company claims that it has more than 150 million users in over 150 countries who speak at least 20 different languages. That said, BigNox’s follower base is predominantly in Asian countries.
“Based on ESET telemetry, we saw the first indicators of compromise in September 2020. Activity continued apace until we uncovered explicitly malicious activity this week, at which point we reported the incident to BigNox,” says ESET researcher Ignacio Sanmillan, who revealed Operation NightScout.
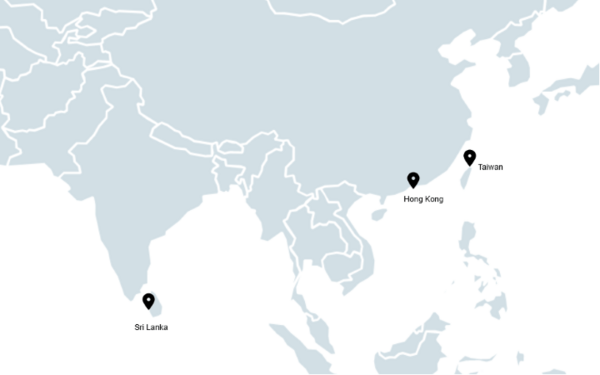
Operation NightScout is a highly targeted operation, with ESET researchers able to identify only several victims. Those identified victims are based in Taiwan, Hong Kong and Sri Lanka. “Based on the compromised software in question and the delivered malware exhibiting surveillance capabilities, we believe this may indicate the intent of intelligence collection on targets involved in the gaming community,” elaborates Sanmillan.
Map – Distribution of NightScout victims
In this specific supply-chain attack, the NoxPlayer update mechanism served as the vector of compromise. On launch, if NoxPlayer detects a newer version of the software, it will prompt the user with a message box offering the user the option to install it, thus delivering the malware.
“We have sufficient evidence to state that BigNox’s infrastructure was compromised to host malware and also to suggest that their API infrastructure could have been compromised. In some cases, additional payloads were downloaded by the BigNox updater from attacker-controlled servers,” adds Sanmillan.
A total of three different malicious update variants were observed by ESET researchers. The first malicious update variant does not seem to have been documented before and has enough capabilities to monitor its victims. The second update variant, in line with the first, was spotted being downloaded from legitimate BigNox infrastructure. The deployed final payload was an instance of Gh0st RAT (with keylogger capabilities) also widely used among threat actors.
The third variant, PoisonIvy RAT – a remote access tool popular with cybercriminals – was only spotted in activity subsequent to the initial malicious updates and downloaded from attacker-controlled infrastructure.
ESET has spotted similarities between loaders that our researchers have monitored in the past and some of those used in Operation NightScout. The similarities we see relate to instances discovered in a Myanmar presidential office website supply-chain compromise in 2018, and in early 2020 in an intrusion into a Hong Kong university.
“To be on the safe side, in case of intrusion, perform a standard reinstall from clean media. For uninfected NoxPlayer users, do not download any updates until BigNox sends notification that they have mitigated the threat, furthermore, best practice would be to uninstall the software”, advises Sanmillan.
For more technical details about Operation NightScout, read the blogpost “Operation NightScout: Supply-chain attack targets online gaming in Asia” on WeLiveSecurity. Make sure to follow ESET Research on Twitter for the latest news from ESET Research.
[Update – February 3, 2021]
Following the publication of our research, BigNox have contacted us to say that their initial denial of the compromise was a misunderstanding on their part and that they have since taken these steps to improve security for their users:
- use only HTTPS to deliver software updates in order to minimise the risks of domain hijacking and Man-in-the-Middle (MitM) attacks
- implement file integrity verification using MD5 hashing and file signature checks
- adopt additional measures, notably encryption of sensitive data, to avoid exposing users’ personal information
BigNox have also stated that they have pushed the latest files to the update server for NoxPlayer and that, upon startup, NoxPlayer will now run a check of the application files previously installed on the users’ machines.
*ESET assumes no responsibility for the accuracy of the information provided by BigNox.
About ESET
For more than 30 years, ESET® has been developing industry-leading IT security software and services to protect businesses, critical infrastructure and consumers worldwide from increasingly sophisticated digital threats. From endpoint and mobile security to endpoint detection and response, as well as encryption and multi-factor authentication, ESET’s high-performing, easy-to-use solutions unobtrusively protect and monitor 24/7, updating defences in real time to keep users safe and businesses running without interruption. Evolving threats require an evolving IT security company that enables the safe use of technology. This is backed by ESET’s R&D centres worldwide, working in support of our shared future. For more information, visit our website or follow us on LinkedIn, Facebook, and Twitter.