Comprehensive security solution for all business sizes
Extended detection & response
Get a complete prevention, detection and remediation solution
Extended endpoint visibility, threat hunting and incident response designed to mitigate any security issue in your network immediately.
Advanced Threat Defense
Prevent zero-day threats
Protection against ransomware and new, never-before-seen threat types that uses adaptive scanning, machine learning, cloud sandboxing and in-depth behavioural analysis.
Robust encryption
Protect business data
Helps comply with data regulations thanks to full disk encryption capabilities on Windows and macOS.
Lead-edge protection
Shield company in real time
Unique behavioural and reputation-based detection that is fully transparent to security teams and gives them real-time feedback gathered from over 110 million endpoints in ESET LiveGrid®.
Management Console Unified cybersecurity platform interface providing superior network visibility and control. Available as cloud or on-prem deployment.
Learn more
Modern Endpoint Protection Advanced multilayered protection for computers and smartphones powered by unique ESET LiveSense technology.
Learn more
Server Security Real-time protection for your company’s data passing through all general servers.
Learn more
Full Disk
Encryption Robust encryption solution for system disks, partitions or entire devices to achieve legal compliance.
Learn more
Advanced Threat
Defence Proactive cloud-based defence against zero-day and never-before-seen threat types utilising machine learning and cloud sandbox analysis.
Learn more
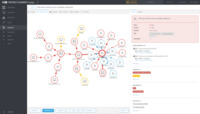
Detection & Response (XDR) The XDR-enabling component of the ESET PROTECT platform, delivering breach prevention, enhanced visibility and remediation.
Learn more
This capability is available from ESET PROTECT Complete.
This capability is available from ESET PROTECT Complete.
This capability is available from ESET PROTECT Complete.
This capability is available from ESET PROTECT Elite.
This capability is available in ESET PROTECT MDR.
This capability is available in ESET PROTECT MDR.
This capability is available in ESET PROTECT MDR.
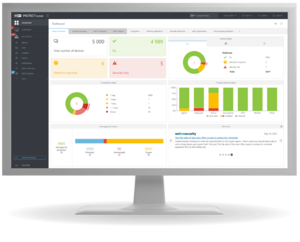
Manage your endpoints wherever you are
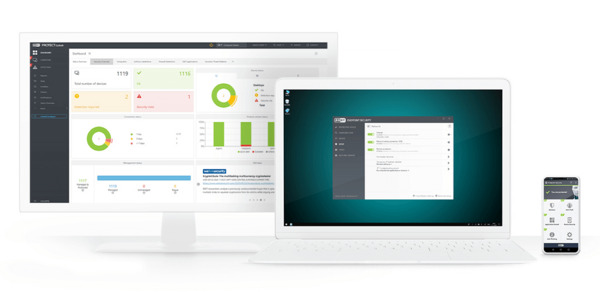
Experience ESET PROTECT's console's full potential right now.
No need for installation or setup.
Advanced reports
ESET PROTECT platform provides over 170 built-in reports and allows you to create custom reports from over 1000 data points.
Custom notifications
Use predefined notifications or create your own. The notification system features a full 'what you see is what you get' editor.
Single-click management
Actions such as 'create an exclusion', 'submit files for further analysis' or 'initiate a scan' are available within a single click.
What IT pros are saying

Angela S
"It is very much customisable tool. In my opinion it is the most functional, robust and manageable tool than any other."
Read full review

Jason D
"The interface is easy to use and lightweight on the system. When used on a 4+ core device with an SSD, the system impact is negligible for most office tasks."
Read full review

Jaliya S
"It is easy to use, simple and understandable. Therefore, we can easily manage the features of it. Also, it is easy to install, configure and update. "
Read full review

Jen D
"I love the way it helps us in detecting unnecessary things that are continuously running our systems behind. In this way it enhances the security of our system."
Read full review
Based on customer reviews, through G2 Crowd surveys that asked ESET business customers to rate their experiences using ESET PROTECT solutions.
Get started

protected by ESET since 2017
more than 9,000 endpoints

protected by ESET since 2016
more than 4,000 mailboxes

protected by ESET since 2016
more than 14,000 endpoints
ISP security partner since 2008
2 million customer base
System requirements and subscription information
ESET PROTECT Enterprise
Supported operating systems
For computers
- Microsoft Windows 11, 10, 8.1, 8, 7, SP1
- macOS 10.12 and later Ubuntu Desktop 20.04 LTS and 18.04 LTS 64-bit
- Red Hat Enterprise Linux 7, 8 64-bit with supported desktop environment installed
- SUSE Linux Enterprise Desktop 15 64-bit
For smartphones and tablets
- Android 5 (Lollipop) and later
- iOS 9 and later
For file servers
- Microsoft Windows Server 2022, 2019, 2016, 2012, 2008, R2 SP1
- Microsoft Windows Storage Server 2012, 2008R2
- Microsoft Windows Small Business Server 2011
- RedHat Enterprise Linux (RHEL) 7, 8
- CentOS 7, 8
- Ubuntu Server 16.04 LTS, 18.04 LTS, 20.04 LTS
- Debian 9, 10, 11
- SUSE Linux Enterprise Server (SLES) 12, 15
- Oracle Linux 8
- Amazon Linux 2
Licence information
Cloud and on-premises management included
Remote management platform is available as cloud-based or on-premises deployment. No need to buy or maintain additional hardware, reducing the total cost of ownership.
Flexible licencing
Mix and match your licences as needed
ESET Unilicense covers all the bases, allowing you to mix and match endpoint protection without wasting a single licence.
Add additional devices at any time
You can purchase licences for additional computers, laptops, mobile devices and servers any time.
Transfer a licence to another computer
You can transfer a valid ESET licence to a completely new computer from the original one. In addition, you can switch from one OS to another.
Switch to a different platform at any time
It's easy to switch your protection from one platform to another at any point during the licence term without having to purchase additional licences.
Related resources and documents
Use Cases
Phishing attacks and fake websites trying to steal login credentials are on the rise. See how ESET can help.
IDC
ESET named a ‘Major Player’ by IDC MarketScape: Worldwide Modern Endpoint Security for Enterprises 2021 Vendor Assessment
Analysts and testing
Find out what industry analysts are saying about ESET, and how we perform in independent tests.
Looking for more security options?
Best-in-class endpoint protection against ransomware & zero-day threats, backed by powerful data security
Complete, multilayered protection for endpoints, cloud applications and email, the number one threat vector
All-in-one prevention, detection & response combining enterprise-grade XDR with complete multilayered protection
Management Console Unified cybersecurity platform interface providing superior network visibility and control. Available as cloud or on-prem deployment.
Modern Endpoint Protection with Next-gen Antivirus Advanced multilayered protection for computers and smartphones powered by unique ESET LiveSense technology.
Full Disk Encryption Robust encryption solution for system disks, partitions or entire devices to achieve legal compliance.
Advanced Threat Defence Proactive cloud-based defence against zero-day and never-before-seen threat types utilising machine learning and cloud sandbox analysis.
Cloud App Protection Advanced protection for Microsoft 365 and Google Workspace apps, with additional proactive threat defence.
Mail Security An additional layer of security, protecting Exchange and IBM email servers from threats entering the network on top of the standard endpoint and file server protection.
Features advanced anti-phishing, anti-malware, and anti-spam combined with cloud-powered proactive threat defence. Provides you with robust quarantine management and rule definition/filtering system.
Prevents ransomware and other email-borne attacks without compromising email's speed.
Vulnerability & Patch Management Actively track & fix vulnerabilities in operating systems and applications across all endpoints.
Extended Detection
and Response Additional platform capability to proactively detect threats, effectively identify anomalous behaviour in the network and realise timely remediation, preventing breaches and business disruption.
ESET Inspect, the XDR-enabling cloud-based tool, provides outstanding threat and system visibility, allowing risk managers and security professionals to perform fast and in-depth root cause analysis and immediately respond to incidents.
Unlock a higher protection tier with the added advantage of EDR included. Click on the plus sign and reach out to our dedicated sales team to explore a tailored offering that meets your unique requirements. No commitment.
Unlock a higher protection tier with the added advantage of EDR included. Click on the plus sign and reach out to our dedicated sales team to explore a tailored offering that meets your unique requirements. No commitment.
Multi-Factor Authentication Single-tap, mobile-based multi-factor authentication that protects organisations from weak passwords and unauthorised access.
Deployment and Upgrade Ensures the effective installation and configuration of ESET business products. Service provided by experienced and certified ESET professionals.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Premium Support Advanced Help from ESET experts, whenever you need it. Get the maximum return on investment from your ESET products.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Threat Intelligence Get in-depth, up-to-date global knowledge about specific threats and attack sources.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Available as on demand upgrade providing additional protection layer. Click on the plus sign and contact sales for more details. No commitment.
Not sure which solution is best for your business?
Are you an existing customer?
Renew today
Renew, upgrade or add devices to your existing ESET subscription.
Manage licences
ESET Business Account is a licence management platform and entry point to ESET cloud services.
Installation
Install your purchased protection on additional devices.
Need assistance?
All ESET products include free technical support in your language.